Validación de bóveda cibernética de ONTAP con PowerShell
 Sugerir cambios
Sugerir cambios


Una bóveda cibernética robusta debe ser capaz de resistir un ataque sofisticado, incluso cuando el atacante tiene credenciales para acceder al entorno con privilegios elevados.
Una vez que las reglas están en su lugar, un intento (asumiendo que de alguna manera el atacante pudo ingresar) de eliminar una instantánea del lado de la bóveda fallará. Lo mismo se aplica a todas las configuraciones de endurecimiento, aplicando las restricciones necesarias y protegiendo el sistema.
Ejemplo de código de PowerShell para validar la configuración de forma programada.
function analyze {
for($i = 0; $i -lt $DESTINATION_VOLUME_NAMES.Length; $i++) {
try {
# checking if volume is of type SnapLock Compliance
logMessage -message "Checking if SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) exists in vServer $DESTINATION_VSERVER"
$volume = Get-NcVol -Vserver $DESTINATION_VSERVER -Volume $DESTINATION_VOLUME_NAMES[$i] | Select-Object -Property Name, State, TotalSize, Aggregate, Vserver, Snaplock | Where-Object { $_.Snaplock.Type -eq "compliance" }
if($volume) {
$volume
logMessage -message "SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) exists in vServer $DESTINATION_VSERVER" -type "SUCCESS"
} else {
handleError -errorMessage "SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) does not exist in vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to create and configure the cyber vault SnapLock Compliance volume"
}
# checking SnapMirror relationship
logMessage -message "Checking if SnapMirror relationship exists between source volume $($SOURCE_VOLUME_NAMES[$i]) and destination SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i])"
$snapmirror = Get-NcSnapmirror | Select-Object SourceCluster, SourceLocation, DestinationCluster, DestinationLocation, Status, MirrorState | Where-Object { $_.SourceCluster -eq $SOURCE_ONTAP_CLUSTER_NAME -and $_.SourceLocation -eq "$($SOURCE_VSERVER):$($SOURCE_VOLUME_NAMES[$i])" -and $_.DestinationCluster -eq $DESTINATION_ONTAP_CLUSTER_NAME -and $_.DestinationLocation -eq "$($DESTINATION_VSERVER):$($DESTINATION_VOLUME_NAMES[$i])" -and $_.Status -eq "snapmirrored" }
if($snapmirror) {
$snapmirror
logMessage -message "SnapMirror relationship successfully configured and in healthy state" -type "SUCCESS"
} else {
handleError -errorMessage "SnapMirror relationship does not exist between the source volume $($SOURCE_VOLUME_NAMES[$i]) and destination SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) (or) SnapMirror status uninitialized/unhealthy. Recommendation: Run the script with SCRIPT_MODE `"configure`" to create and configure the cyber vault SnapLock Compliance volume and configure the SnapMirror relationship"
}
}
catch {
handleError -errorMessage $_.Exception.Message
}
}
try {
# checking NFS service is disabled
logMessage -message "Checking if NFS service is disabled on vServer $DESTINATION_VSERVER"
$nfsService = Get-NcNfsService
if($nfsService) {
handleError -errorMessage "NFS service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable NFS on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "NFS service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking CIFS/SMB server is disabled
logMessage -message "Checking if CIFS/SMB server is disabled on vServer $DESTINATION_VSERVER"
$cifsServer = Get-NcCifsServer
if($cifsServer) {
handleError -errorMessage "CIFS/SMB server running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable CIFS/SMB on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "CIFS/SMB server is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking iSCSI service is disabled
logMessage -message "Checking if iSCSI service is disabled on vServer $DESTINATION_VSERVER"
$iscsiService = Get-NcIscsiService
if($iscsiService) {
handleError -errorMessage "iSCSI service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable iSCSI on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "iSCSI service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking FCP service is disabled
logMessage -message "Checking if FCP service is disabled on vServer $DESTINATION_VSERVER"
$fcpService = Get-NcFcpService
if($fcpService) {
handleError -errorMessage "FCP service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable FCP on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "FCP service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking if all data lifs are disabled on vServer
logMessage -message "Finding all data lifs on vServer : $DESTINATION_VSERVER"
$dataLifs = Get-NcNetInterface -Vserver $DESTINATION_VSERVER | Where-Object { $_.Role -contains "data_core" }
$dataLifs | Select-Object -Property InterfaceName, OpStatus, DataProtocols, Vserver, Address
logMessage -message "Checking if all data lifs are disabled for vServer : $DESTINATION_VSERVER"
# Disable the filtered data LIFs
foreach ($lif in $dataLifs) {
$checkLif = Get-NcNetInterface -Vserver $DESTINATION_VSERVER -Name $lif.InterfaceName | Where-Object { $_.OpStatus -eq "down" }
if($checkLif) {
logMessage -message "Data lif $($lif.InterfaceName) disabled for vServer $DESTINATION_VSERVER" -type "SUCCESS"
} else {
handleError -errorMessage "Data lif $($lif.InterfaceName) is enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable Data lifs for vServer $DESTINATION_VSERVER"
}
}
logMessage -message "All data lifs are disabled for vServer : $DESTINATION_VSERVER" -type "SUCCESS"
# check if multi-admin verification is enabled
logMessage -message "Checking if multi-admin verification is enabled"
$maaConfig = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; security multi-admin-verify show"
if ($maaConfig.Value -match "Enabled" -and $maaConfig.Value -match "true") {
$maaConfig
logMessage -message "Multi-admin verification is configured and enabled" -type "SUCCESS"
} else {
handleError -errorMessage "Multi-admin verification is not configured or not enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to enable and configure Multi-admin verification"
}
# check if telnet is disabled
logMessage -message "Checking if telnet is disabled"
$telnetConfig = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; security protocol show -application telnet"
if ($telnetConfig.Value -match "enabled" -and $telnetConfig.Value -match "false") {
logMessage -message "Telnet is disabled" -type "SUCCESS"
} else {
handleError -errorMessage "Telnet is enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable telnet"
}
# check if network https is restricted to allowed IP addresses
logMessage -message "Checking if HTTPS is restricted to allowed IP addresses $ALLOWED_IPS"
$networkServicePolicy = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; network interface service-policy show"
if ($networkServicePolicy.Value -match "management-https: $($ALLOWED_IPS)") {
logMessage -message "HTTPS is restricted to allowed IP addresses $ALLOWED_IPS" -type "SUCCESS"
} else {
handleError -errorMessage "HTTPS is not restricted to allowed IP addresses $ALLOWED_IPS. Recommendation: Run the script with SCRIPT_MODE `"configure`" to restrict allowed IP addresses for HTTPS management"
}
}
catch {
handleError -errorMessage $_.Exception.Message
}
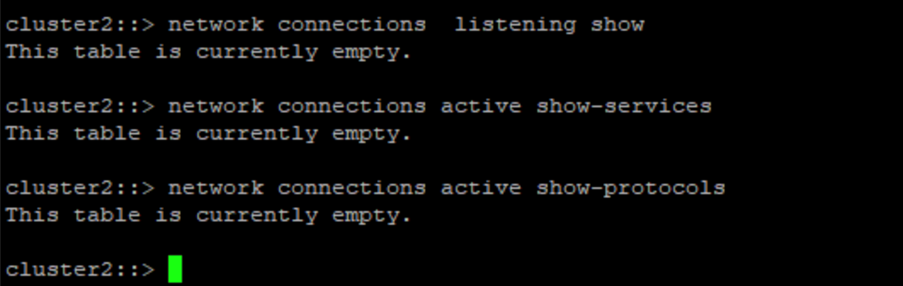
}Esta captura de pantalla muestra que no hay conexiones en el controlador de bóveda.
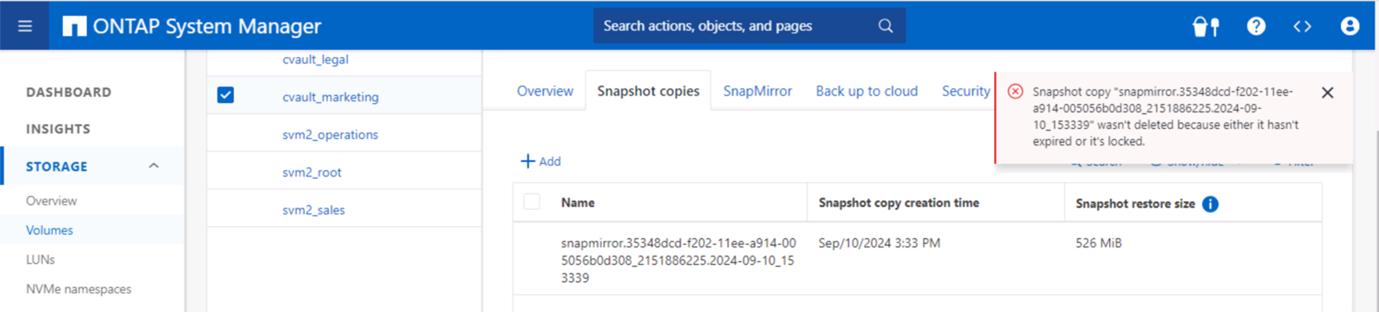
Esta captura de pantalla muestra que no es posible manipular las instantáneas.
Para validar y confirmar la funcionalidad del espacio de aire, siga los pasos a continuación:
-
Pruebe las capacidades de aislamiento de la red y la capacidad de suspender una conexión cuando no se transfieren datos.
-
Verifique que no se pueda acceder a la interfaz de administración desde ninguna entidad aparte de las direcciones IP permitidas.
-
Verificar La verificación de múltiples administradores está implementada para proporcionar una capa adicional de aprobación.
-
Validar la capacidad de acceder a través de CLI y API REST
-
Desde la fuente, active una operación de transferencia a la bóveda y asegúrese de que la copia almacenada no se pueda modificar.
-
Intente eliminar las copias de instantáneas inmutables que se transfieren al almacén.
-
Intente modificar el período de retención manipulando el reloj del sistema.


