Requirements for Kubernetes clusters in Google Cloud
 Suggest changes
Suggest changes


You can add and manage managed Google Kubernetes Engine (GKE) clusters and self-managed Kubernetes clusters in Google using BlueXP. Before you can add the clusters to BlueXP, ensure the following requirements are met.

|
This topic uses Kubernetes cluster where configuration is the same for GKE and self-managed Kubernetes clusters. The cluster type is specified where configuration differs. |
Requirements
- Astra Trident
-
One of the four most recent versions of Astra Trident is required. You can install or upgrade Astra Trident directly from BlueXP. You should review the prerequisites prior to installing Astra Trident
- Cloud Volumes ONTAP
-
Cloud Volumes ONTAP must be in BlueXP under the same tenancy account, workspace, and Connector as the Kubernetes cluster. Go to the Astra Trident docs for configuration steps.
- BlueXP Connector
-
A Connector must be running in Google with the required permissions. Learn more below.
- Network connectivity
-
Network connectivity is required between the Kubernetes cluster and the Connector and between the Kubernetes cluster and Cloud Volumes ONTAP. Learn more below.
- RBAC authorization
-
BlueXP supports RBAC-enabled clusters with and without Active Directory. The BlueXP Connector role must be authorized on each GKE cluster. Learn more below.
Prepare a Connector
A BlueXP Connector in Google is required to discover and manage Kubernetes clusters. You'll need to create a new Connector or use an existing Connector that has the required permissions.
Create a new Connector
Follow the steps in one of the links below.
Add the required permissions to an existing Connector (to discover a managed GKE cluster)
If you want to discover a managed GKE cluster, you might need to modify the custom role for the Connector to provide the permissions.
-
In Cloud Console, go to the Roles page.
-
Using the drop-down list at the top of the page, select the project or organization that contains the role that you want to edit.
-
Click a custom role.
-
Click Edit Role to update the role's permissions.
-
Click Add Permissions to add the following new permissions to the role.
container.clusters.get container.clusters.list -
Click Update to save the edited role.
Review networking requirements
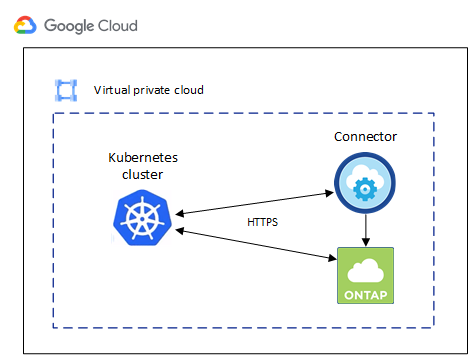
You need to provide network connectivity between the Kubernetes cluster and the Connector and between the Kubernetes cluster and the Cloud Volumes ONTAP system that provides backend storage to the cluster.
-
Each Kubernetes cluster must have an inbound connection from the Connector
-
The Connector must have an outbound connection to each Kubernetes cluster over port 443
The simplest way to provide this connectivity is to deploy the Connector and Cloud Volumes ONTAP in the same VPC as the Kubernetes cluster. Otherwise, you need to set up a peering connection between the different VPC.
Here's an example that shows each component in the same VPC.
Set up RBAC authorization
RBAC validation occurs only on Kubernetes clusters with Active Directory (AD) enabled. Kubernetes clusters without AD will pass validation automatically.
You need authorize the Connector role on each Kubernetes cluster so the Connector can discover and manage a cluster.
- Backup and restore
-
Backup and restore requires only basic authorization.
- Add storage classes
-
Expanded authorization is required to add storage classes using BlueXP and monitor the cluster for changes to the backend.
- Install Astra trident
-
You need to provide full authorization for BlueXP to install Astra Trident.
When installing Astra Trident, BlueXP installs the Astra Trident backend and Kubernetes secret that contains the credentials Astra Trident needs to communicate with the storage cluster.
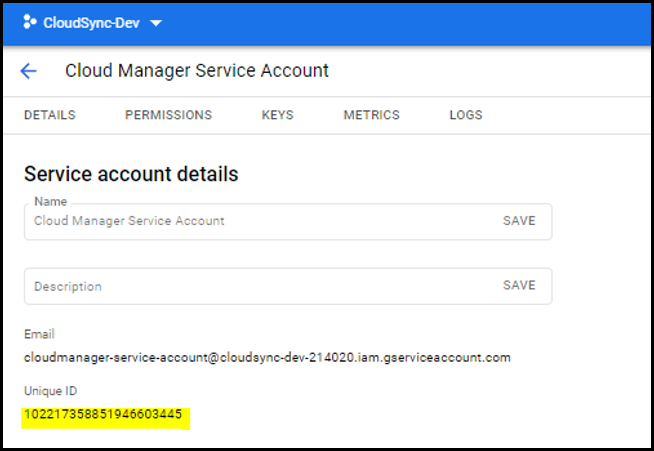
To configure subjects: name: in the YAML file, you need to know the BlueXP Unique ID.
You can find the unique ID one of two ways:
-
Using the command:
gcloud iam service-accounts list gcloud iam service-accounts describe <service-account-email> -
In the Service Account Details on the Cloud Console.
Create a cluster role and role binding.
-
You can customize authorization based on your requirements.
Backup/restoreAdd basic authorization to enable backup and restore for Kubernetes clusters.
Replace the
subjects: kind:variable with your username andsubjects: name:with the unique ID for the authorized service account.apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cloudmanager-access-clusterrole rules: - apiGroups: - '' resources: - namespaces verbs: - list - watch - apiGroups: - '' resources: - persistentvolumes verbs: - list - watch - apiGroups: - '' resources: - pods - pods/exec verbs: - get - list - watch - apiGroups: - '' resources: - persistentvolumeclaims verbs: - list - create - watch - apiGroups: - storage.k8s.io resources: - storageclasses verbs: - list - apiGroups: - trident.netapp.io resources: - tridentbackends verbs: - list - watch - apiGroups: - trident.netapp.io resources: - tridentorchestrators verbs: - get - watch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: k8s-access-binding subjects: - kind: User name: apiGroup: rbac.authorization.k8s.io roleRef: kind: ClusterRole name: cloudmanager-access-clusterrole apiGroup: rbac.authorization.k8s.ioStorage classesAdd expanded authorization to add storage classes using BlueXP.
Replace the
subjects: kind:variable with your username andsubjects: user:with the unique ID for the authorized service account.apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cloudmanager-access-clusterrole rules: - apiGroups: - '' resources: - secrets - namespaces - persistentvolumeclaims - persistentvolumes - pods - pods/exec verbs: - get - list - watch - create - delete - watch - apiGroups: - storage.k8s.io resources: - storageclasses verbs: - get - create - list - watch - delete - patch - apiGroups: - trident.netapp.io resources: - tridentbackends - tridentorchestrators - tridentbackendconfigs verbs: - get - list - watch - create - delete - watch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: k8s-access-binding subjects: - kind: User name: apiGroup: rbac.authorization.k8s.io roleRef: kind: ClusterRole name: cloudmanager-access-clusterrole apiGroup: rbac.authorization.k8s.ioTrident installationUse the command line to provide full authorization and enable BlueXP to install Astra Trident.
kubectl create clusterrolebinding test --clusterrole cluster-admin --user <Unique ID> -
Apply the configuration to a cluster.
kubectl apply -f <file-name>



 Get started
Get started