Set up Cloud Volumes ONTAP to use a customer-managed key in AWS
 Suggest changes
Suggest changes


If you want to use Amazon encryption with Cloud Volumes ONTAP, then you need to set up the AWS Key Management Service (KMS).
-
Ensure that an active Customer Master Key (CMK) exists.
The CMK can be an AWS-managed CMK or a customer-managed CMK. It can be in the same AWS account as the NetApp Console and Cloud Volumes ONTAP or in a different AWS account.
-
Modify the key policy for each CMK by adding the IAM role that provides permissions to the Console as a key user.
Adding the Identity and Access Management (IAM) role as a key user gives the Console permissions to use the CMK with Cloud Volumes ONTAP.
-
If the CMK is in a different AWS account, complete the following steps:
-
Go to the KMS console from the account where the CMK resides.
-
Select the key.
-
In the General configuration pane, copy the ARN of the key.
You'll need to provide the ARN to the Console when you create the Cloud Volumes ONTAP system.
-
In the Other AWS accounts pane, add the AWS account that provides the Console with permissions.
Typically, this is the account where the Console is deployed. If the Console is not installed in AWS, use the account for which you provided AWS access keys to the Console.

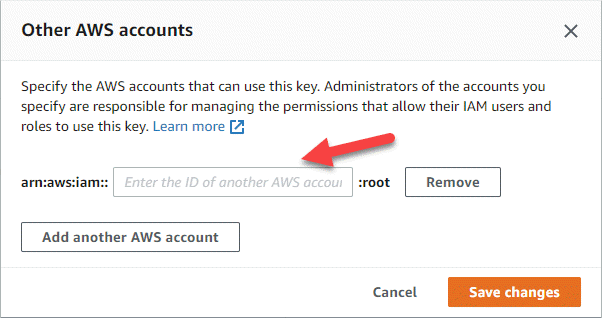
-
Now switch to the AWS account that provides the Console with permissions and open the IAM console.
-
Create an IAM policy that includes the permissions listed below.
-
Attach the policy to the IAM role or IAM user that provides permissions to the Console.
The following policy provides the permissions that the Console needs to use the CMK from the external AWS account. Be sure to modify the region and account ID in the "Resource" sections.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowUseOfTheKey", "Effect": "Allow", "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": [ "arn:aws:kms:us-east-1:externalaccountid:key/externalkeyid" ] }, { "Sid": "AllowAttachmentOfPersistentResources", "Effect": "Allow", "Action": [ "kms:CreateGrant", "kms:ListGrants", "kms:RevokeGrant" ], "Resource": [ "arn:aws:kms:us-east-1:externalaccountid:key/externalaccountid" ], "Condition": { "Bool": { "kms:GrantIsForAWSResource": true } } } ] }For additional details about this process, refer to the AWS Documentation: Allowing users in other accounts to use a KMS key.
-
-
If you are using a customer-managed CMK, modify the key policy for the CMK by adding the Cloud Volumes ONTAP IAM role as a key user.
This step is required if you enabled data tiering on Cloud Volumes ONTAP and want to encrypt the data stored in the Amazon Simple Storage Service (Amazon S3) bucket.
You'll need to perform this step after you deploy Cloud Volumes ONTAP because the IAM role is created when you create a Cloud Volumes ONTAP system. (Of course, you do have the option to use an existing Cloud Volumes ONTAP IAM role, so it's possible to perform this step before.)


