Use an Azure Private Link or service endpoints for Cloud Volumes ONTAP systems
 Suggest changes
Suggest changes


Cloud Volumes ONTAP uses an Azure Private Link for connections to its associated storage accounts. If needed, you can disable Azure Private Links and use service endpoints instead.
Overview
By default, the NetApp Console enables an Azure Private Link for connections between Cloud Volumes ONTAP and its associated storage accounts. An Azure Private Link secures connections between endpoints in Azure and provides performance benefits.
If required, you can configure Cloud Volumes ONTAP to use service endpoints instead of an Azure Private Link.
With either configuration, the Console always limits network access for connections between Cloud Volumes ONTAP and storage accounts. Network access is limited to the VNet where Cloud Volumes ONTAP is deployed and the VNet where the Console agent is deployed.
Disable Azure Private Links and use service endpoints instead
If required by your business, you can change a setting in the Console so that it configures Cloud Volumes ONTAP to use service endpoints instead of an Azure Private Link. Changing this setting applies to new Cloud Volumes ONTAP systems that you create. Service endpoints are only supported in Azure region pairs between the Console agent and Cloud Volumes ONTAP VNets.
The Console agent should be deployed in the same Azure region as the Cloud Volumes ONTAP systems that it manages, or in the Azure region pair for the Cloud Volumes ONTAP systems.
-
From the left navigation pane, go to Administration > Agents.
-
Click the
 icon for the Console agent that manages your Cloud Volumes ONTAP system.
icon for the Console agent that manages your Cloud Volumes ONTAP system. -
Select Cloud Volumes ONTAP Settings.
-
Under Azure, click Use Azure Private Link.
-
Deselect Private Link connection between Cloud Volumes ONTAP and storage accounts.
-
Click Save.
If you disabled Azure Private Links and the Console agent uses a proxy server, you must enable direct API traffic.
Work with Azure Private Links
In most cases, there's nothing that you need to do to set up Azure Private links with Cloud Volumes ONTAP. The Console manages Azure Private Links for you. But if you use an existing Azure Private DNS zone, then you'll need to edit a configuration file.
Requirement for custom DNS
Optionally, if you work with custom DNS, you need to create a conditional forwarder to the Azure private DNS zone from your custom DNS servers. To learn more, refer to Azure's documentation on using a DNS forwarder.
How Private Link connections work
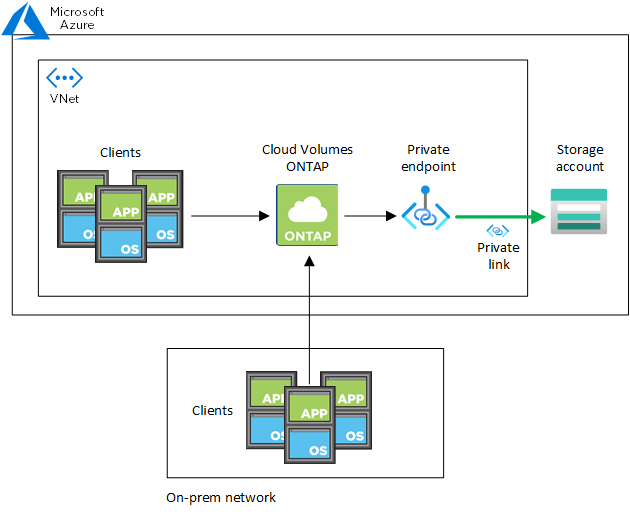
When the Console deploys Cloud Volumes ONTAP in Azure, it creates a private endpoint in the resource group. The private endpoint is associated with storage accounts for Cloud Volumes ONTAP. As a result, access to Cloud Volumes ONTAP storage travels through the Microsoft backbone network.
Client access goes through the private link when clients are within the same VNet as Cloud Volumes ONTAP, within peered VNets, or in your on-premises network when using a private VPN or ExpressRoute connection to the VNet.
Here's an example that shows client access over a private link from within the same VNet and from an on-premises network that has either a private VPN or ExpressRoute connection.

|
If the Console agent and Cloud Volumes ONTAP systems are deployed in different VNets, then you must set up VNet peering between the VNet where the Console agent is deployed and the VNet where the Cloud Volumes ONTAP systems are deployed. |
Provide details about your Azure Private DNS
If you use Azure Private DNS, then you need to modify a configuration file on each Console agent. Otherwise, the Console can't set the Azure Private Link connection between Cloud Volumes ONTAP and its associated storage accounts.
Note that the DNS name must match Azure DNS naming requirements as shown in Azure documentation.
-
SSH to the Console agent host and log in.
-
Navigate to the
/opt/application/netapp/cloudmanager/docker_occm/datadirectory. -
Edit
app.confby adding theuser-private-dns-zone-settingsparameter with the following keyword-value pairs:"user-private-dns-zone-settings" : { "resource-group" : "<resource group name of the DNS zone>", "subscription" : "<subscription ID>", "use-existing" : true, "create-private-dns-zone-link" : true }The
subscriptionkeyword is required only if the private DNS zone is in a different subscription than that of the Console agent. -
Save the file and log off the Console agent.
A reboot isn't required.
Enable rollback on failures
If the Console fails to create an Azure Private Link as part of specific actions, it completes the action without the Azure Private Link connection. This can happen when creating a new system (single node or HA pair), or when the following actions occur on an HA pair: creating a new aggregate, adding disks to an existing aggregate, or creating a new storage account when going above 32 TiB.
You can change this default behavior by enabling rollback if the Console fails to create the Azure Private Link. This can help to ensure that you're fully compliant with your company's security regulations.
If you enable rollback, the Console stops the action and rolls back all resources that were created as part of the action.
You can enable rollback through the API or by updating the app.conf file.
Enable rollback through the API
-
Use the
PUT /occm/configAPI call with the following request body:{ "rollbackOnAzurePrivateLinkFailure": true }
Enable rollback by updating app.conf
-
SSH to the host of the Console agent and log in.
-
Navigate to the following directory: /opt/application/netapp/cloudmanager/docker_occm/data
-
Edit app.conf by adding the following parameter and value:
"rollback-on-private-link-failure": true
-
Save the file and log off the Console agent.
A reboot isn't required.


