Learn about Azure credentials and permissions in NetApp Console
 Suggest changes
Suggest changes


Learn how the NetApp Console uses Azure credentials to perform actions on your behalf and how those credentials are associated with marketplace subscriptions. Understanding these details can be helpful as you manage the credentials for one or more Azure subscriptions. For example, you might want to learn when to add additional Azure credentials to the Console.
Initial Azure credentials
When you deploy a Console agent from the Console, you need to use an Azure account or service principal that has permissions to deploy the Console agent virtual machine. The required permissions are listed in the Agent deployment policy for Azure.
When the Console deploys the Console agent virtual machine in Azure, it enables a system-assigned managed identity on the virtual machine, creates a custom role, and assigns it to the virtual machine. The role provides the Console with the permissions required to manage resources and processes within that Azure subscription. Review how the Console uses the permissions.
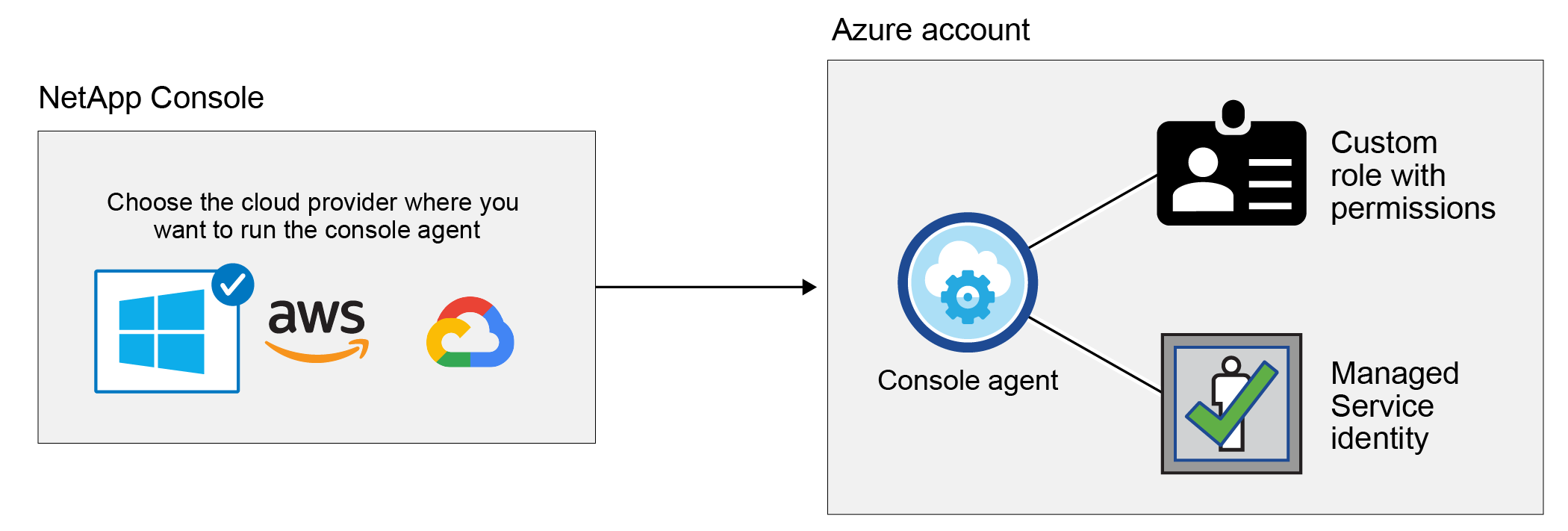
If you create a new system for Cloud Volumes ONTAP, the Console selects these Azure credentials by default:
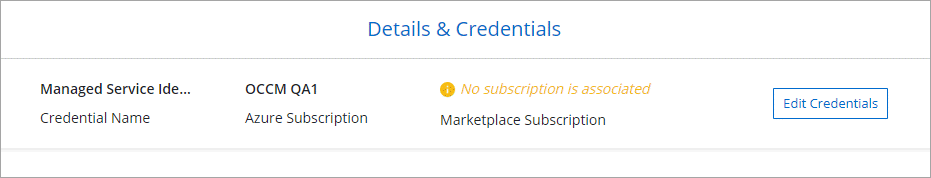
You can deploy all of your Cloud Volumes ONTAP systems using the initial Azure credentials, or you can add additional credentials.
Additional Azure subscriptions for a managed identity
The system-assigned managed identity assigned to the Console agent VM is associated with the subscription in which you launched the Console agent. If you want to select a different Azure subscription, then you need to associate the managed identity with those subscriptions.
Additional Azure credentials
If you want to use different Azure credentials with the Console, then you must grant the required permissions by creating and setting up a service principal in Microsoft Entra ID for each Azure account. The following image shows two additional accounts, each set up with a service principal and custom role that provides permissions:
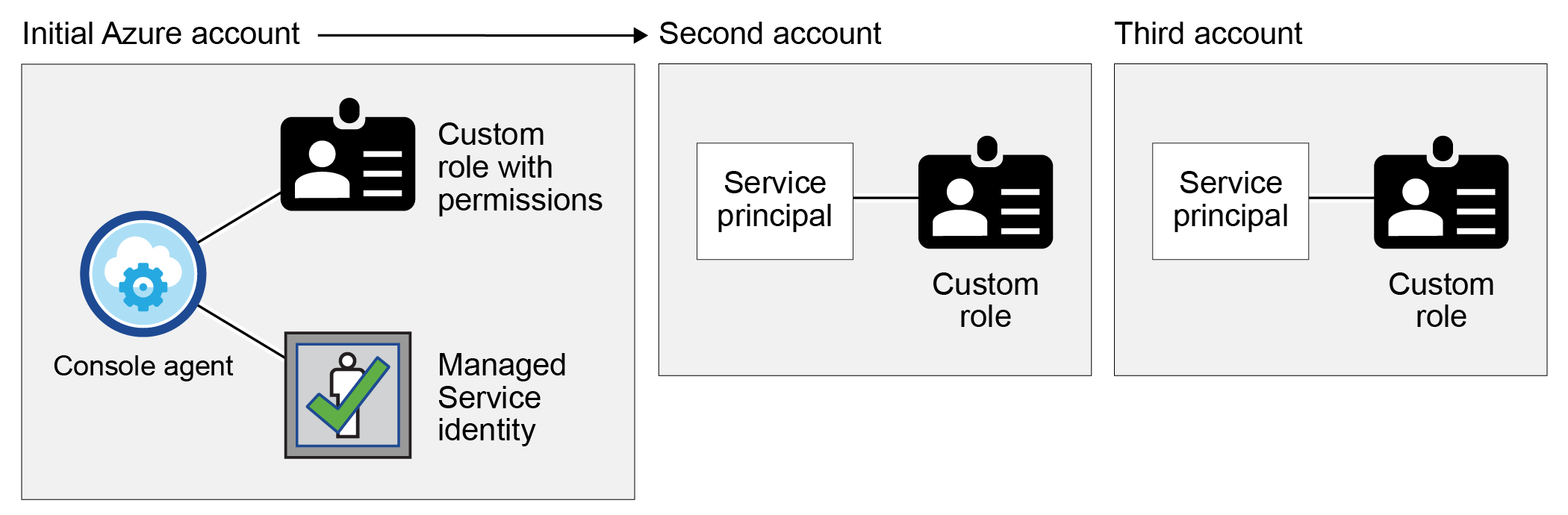
You would then add the account credentials to the Console by providing details about the AD service principal.
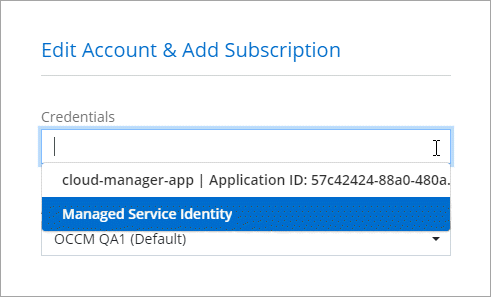
For example, you can switch between credentials when creating a new Cloud Volumes ONTAP system:
Credentials and marketplace subscriptions
The credentials that you add to a console agent must be associated with an Azure Marketplace subscription so that you can pay for Cloud Volumes ONTAP at an hourly rate (PAYGO) or NetApp data services or through an annual contract.
Note the following about Azure credentials and marketplace subscriptions:
-
You can associate only one Azure Marketplace subscription with a set of Azure credentials
-
You can replace an existing marketplace subscription with a new subscription
FAQ
The following question is related to credentials and subscriptions.
Can I change the Azure Marketplace subscription for Cloud Volumes ONTAP systems?
Yes, you can. When you change the Azure Marketplace subscription that's associated with a set of Azure credentials, all existing and new Cloud Volumes ONTAP systems will be charged against the new subscription.
Can I add multiple Azure credentials, each with different marketplace subscriptions?
All Azure credentials that belong to the same Azure subscription will be associated with the same Azure Marketplace subscription.
If you have multiple Azure credentials that belong to different Azure subscriptions, then those credentials can be associated with the same Azure Marketplace subscription or with different marketplace subscriptions.
Can I move existing Cloud Volumes ONTAP systems to a different Azure subscription?
No, it's not possible to move the Azure resources associated with your Cloud Volumes ONTAP system to a different Azure subscription.
How do credentials work for marketplace deployments and on-premises deployments?
The sections above describe the recommended deployment method for the Console agent, which is from the Console. You can also deploy a console agent in Azure from the Azure Marketplace, and you can install the Console agent software on your own Linux host.
If you use the Marketplace, you can provide permissions by assigning a custom role to the Console agent VM and to a system-assigned managed identity, or you can use a Microsoft Entra service principal.
For on-premises deployments, you can't set up a managed identity for the Console agent, but you can provide permissions by using a service principal.
To learn how to set up permissions, refer to the following pages:


