Integrate your Active Directory with NetApp Data Classification
 Suggest changes
Suggest changes


You can integrate a global Active Directory with NetApp Data Classification to enhance the results that Data Classification reports about file owners and which users and groups have access to your files.
When you set up certain data sources (listed below), you need to enter Active Directory credentials in order for Data Classification to scan CIFS volumes. This integration provides Data Classification with file owner and permissions details for the data that resides in those data sources. The Active Directory entered for those data sources might differ from the global Active Directory credentials you enter here. Data Classification will look in all integrated Active Directories for user and permission details.
This integration provides additional information in the following locations in Data Classification:
-
You can use the "File Owner" filter and see results in the file's metadata in the Investigation pane. Instead of the file owner containing the SID (Security IDentifier), it is populated with the actual user name.
You can also view more details about the file owner: account name, email address, and SAM account name, or view items owned by that user.
-
You can see full file permissions for each file and directory when you click the "View all Permissions" button.
-
In the Governance dashboard, the Open Permissions panel will show a greater level of detail about your data.

|
Local user SIDs, and SIDs from unknown domains, are not translated to the actual user name. |
Supported data sources
An Active Directory integration with Data Classification can identify data from within the following data sources:
-
On-premises ONTAP systems
-
Cloud Volumes ONTAP
-
Azure NetApp Files
-
FSx for ONTAP
Connect to your Active Directory server
After you've deployed Data Classification and have activated scanning on your data sources, you can integrate Data Classification with your Active Directory. Active Directory can be accessed using a DNS Server IP address or an LDAP Server IP address.
The Active Directory credentials can be read-only, but providing admin credentials ensures that Data Classification can read any data that requires elevated permissions. The credentials are stored on the Data Classification instance.
For CIFS volumes/file shares, if you want to make sure your files "last accessed times" are unchanged by Data Classification classification scans, the user should have Write Attributes permission. If possible, we recommend making the Active Directory configured user part of a parent group in the organization which has permissions to all files.
-
You must have an Active Directory already set up for the users in your company.
-
You must have the information for the Active Directory:
-
DNS Server IP address, or multiple IP addresses
or
LDAP Server IP address, or multiple IP addresses
-
User Name and Password to access the server
-
Domain Name (Active Directory Name)
-
Whether you are using secure LDAP (LDAPS) or not
-
LDAP Server Port (typically 389 for LDAP, and 636 for secure LDAP)
-
-
The following ports must be open for outbound communication by the Data Classification instance:
Protocol Port Destination Purpose TCP & UDP
389
Active Directory
LDAP
TCP
636
Active Directory
LDAP over SSL
TCP
3268
Active Directory
Global Catalog
TCP
3269
Active Directory
Global Catalog over SSL
-
From the Data Classification Configuration page, click Add Active Directory.
-
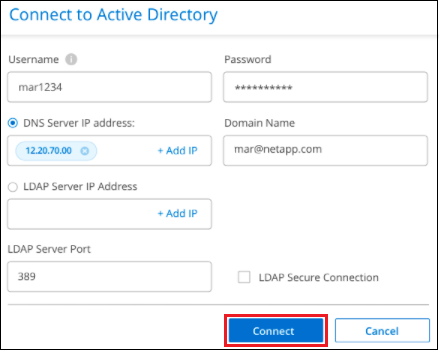
In the Connect to Active Directory dialog, enter the Active Directory details and click Connect.
You can add multiple IP addresses, if required, by selecting Add IP.
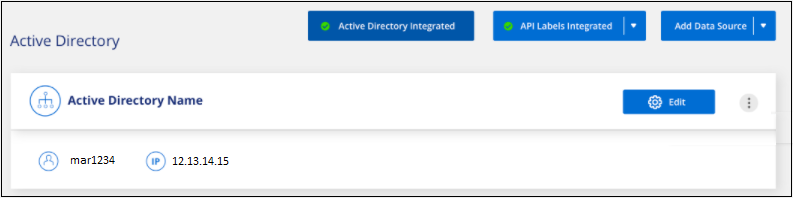
Data Classification integrates to the Active Directory, and a new section is added to the Configuration page.
Manage your Active Directory integration
If you need to modify any values in your Active Directory integration, click the Edit button and make the changes.
You can also delete the integration selecting the  button then Remove Active Directory.
button then Remove Active Directory.


