NetApp Astra Control Center overview
 Suggest changes
Suggest changes


NetApp Astra Control Center offers a rich set of storage and application-aware data management services for stateful Kubernetes workloads deployed in an on-premises environment and powered by NetApp data protection technology.
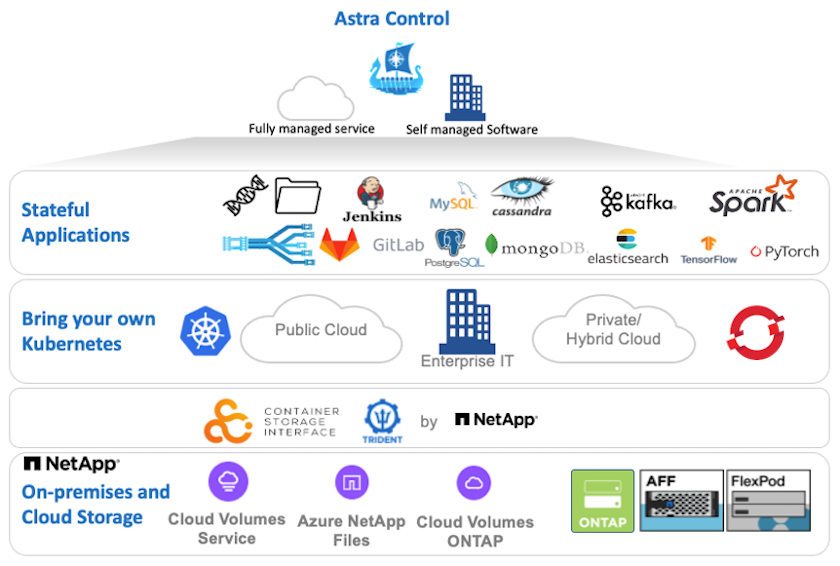
NetApp Astra Control Center can be installed on a Red Hat OpenShift cluster that has the Trident storage orchestrator deployed and configured with storage classes and storage backends to NetApp ONTAP storage systems.
For the installation and configuration of Trident to support Astra Control Center, see this document here.
In a cloud-connected environment, Astra Control Center uses Cloud Insights to provide advanced monitoring and telemetry. In the absence of a Cloud Insights connection, limited monitoring and telemetry (7-days worth of metrics) is available and exported to Kubernetes native monitoring tools (Prometheus and Grafana) through open metrics endpoints.
Astra Control Center is fully integrated into the NetApp AutoSupport and Active IQ Digital Advisor (also known as Digital Advisor) ecosystem to provide support for users, provide assistance with troubleshooting, and display usage statistics.
In addition to the paid version of Astra Control Center, a 90-day evaluation license is available. The evaluation version is supported through the email and community (Slack channel). Customers have access to these and other knowledge-base articles and the documentation available from the in-product support dashboard.
To get started with NetApp Astra Control Center, visit the Astra website.
Astra Control Center installation prerequisites
-
One or more Red Hat OpenShift clusters. Versions 4.6 EUS and 4.7 are currently supported.
-
Trident must already be installed and configured on each Red Hat OpenShift cluster.
-
One or more NetApp ONTAP storage systems running ONTAP 9.5 or greater.
It's best practice for each OpenShift install at a site to have a dedicated SVM for persistent storage. Multi-site deployments require additional storage systems. -
A Trident storage backend must be configured on each OpenShift cluster with an SVM backed by an ONTAP cluster.
-
A default StorageClass configured on each OpenShift cluster with Trident as the storage provisioner.
-
A load balancer must be installed and configured on each OpenShift cluster for load balancing and exposing OpenShift Services.
See the link here for information about load balancers that have been validated for this purpose. -
A private image registry must be configured to host the NetApp Astra Control Center images.
See the link here to install and configure an OpenShift private registry for this purpose. -
You must have Cluster Admin access to the Red Hat OpenShift cluster.
-
You must have Admin access to NetApp ONTAP clusters.
-
An admin workstation with docker or podman, tridentctl, and oc or kubectl tools installed and added to your $PATH.
Docker installations must have docker version greater than 20.10 and Podman installations must have podman version greater than 3.0.
Install Astra Control Center
-
Log into the NetApp Support Site and download the latest version of NetApp Astra Control Center. To do so requires a license attached to your NetApp account. After you download the tarball, transfer it to the admin workstation.
To get started with a trial license for Astra Control, visit the Astra registration site. -
Unpack the tar ball and change the working directory to the resulting folder.
[netapp-user@rhel7 ~]$ tar -vxzf astra-control-center-21.12.60.tar.gz [netapp-user@rhel7 ~]$ cd astra-control-center-21.12.60
-
Before starting the installation, push the Astra Control Center images to an image registry. You can choose to do this with either Docker or Podman, instructions for both are provided in this step.
Podman-
Export the registry FQDN with the organization/namespace/project name as a environment variable ‘registry’.
[netapp-user@rhel7 ~]$ export REGISTRY=astra-registry.apps.ocp-vmw.cie.netapp.com/netapp-astra
-
Log into the registry.
[netapp-user@rhel7 ~]$ podman login -u ocp-user -p password --tls-verify=false astra-registry.apps.ocp-vmw.cie.netapp.com
If you are using kubeadminuser to log into the private registry, then use token instead of password -podman login -u ocp-user -p token --tls-verify=false astra-registry.apps.ocp-vmw.cie.netapp.com.Alternatively, you can create a service account, assign registry-editor and/or registry-viewer role (based on whether you require push/pull access) and log into the registry using service account's token. -
Create a shell script file and paste the following content in it.
[netapp-user@rhel7 ~]$ vi push-images-to-registry.sh for astraImageFile in $(ls images/*.tar) ; do # Load to local cache. And store the name of the loaded image trimming the 'Loaded images: ' astraImage=$(podman load --input ${astraImageFile} | sed 's/Loaded image(s): //') astraImage=$(echo ${astraImage} | sed 's!localhost/!!') # Tag with local image repo. podman tag ${astraImage} ${REGISTRY}/${astraImage} # Push to the local repo. podman push ${REGISTRY}/${astraImage} doneIf you are using untrusted certificates for your registry, edit the shell script and use --tls-verify=falsefor the podman push commandpodman push $REGISTRY/$(echo $astraImage | sed 's/[\/]\+\///') --tls-verify=false. -
Make the file executable.
[netapp-user@rhel7 ~]$ chmod +x push-images-to-registry.sh
-
Execute the shell script.
[netapp-user@rhel7 ~]$ ./push-images-to-registry.sh
Docker-
Export the registry FQDN with the organization/namespace/project name as a environment variable ‘registry’.
[netapp-user@rhel7 ~]$ export REGISTRY=astra-registry.apps.ocp-vmw.cie.netapp.com/netapp-astra
-
Log into the registry.
[netapp-user@rhel7 ~]$ docker login -u ocp-user -p password astra-registry.apps.ocp-vmw.cie.netapp.com
If you are using kubeadminuser to log into the private registry, then use token instead of password -docker login -u ocp-user -p token astra-registry.apps.ocp-vmw.cie.netapp.com.Alternatively, you can create a service account, assign registry-editor and/or registry-viewer role (based on whether you require push/pull access) and log into the registry using service account's token. -
Create a shell script file and paste the following content in it.
[netapp-user@rhel7 ~]$ vi push-images-to-registry.sh for astraImageFile in $(ls images/*.tar) ; do # Load to local cache. And store the name of the loaded image trimming the 'Loaded images: ' astraImage=$(docker load --input ${astraImageFile} | sed 's/Loaded image: //') astraImage=$(echo ${astraImage} | sed 's!localhost/!!') # Tag with local image repo. docker tag ${astraImage} ${REGISTRY}/${astraImage} # Push to the local repo. docker push ${REGISTRY}/${astraImage} done -
Make the file executable.
[netapp-user@rhel7 ~]$ chmod +x push-images-to-registry.sh
-
Execute the shell script.
[netapp-user@rhel7 ~]$ ./push-images-to-registry.sh
-
-
When using private image registries that are not publicly trusted, upload the image registry TLS certificates to the OpenShift nodes. To do so, create a configmap in the openshift-config namespace using the TLS certificates and patch it to the cluster image config to make the certificate trusted.
[netapp-user@rhel7 ~]$ oc create configmap default-ingress-ca -n openshift-config --from-file=astra-registry.apps.ocp-vmw.cie.netapp.com=tls.crt [netapp-user@rhel7 ~]$ oc patch image.config.openshift.io/cluster --patch '{"spec":{"additionalTrustedCA":{"name":"default-ingress-ca"}}}' --type=mergeIf you are using an OpenShift internal registry with default TLS certificates from the ingress operator with a route, you still need to follow the previous step to patch the certificates to the route hostname. To extract the certificates from ingress operator, you can use the command oc extract secret/router-ca --keys=tls.crt -n openshift-ingress-operator. -
Create a namespace
netapp-acc-operatorfor Astra Control Center.[netapp-user@rhel7 ~]$ oc create ns netapp-acc-operator namespace/netapp-acc-operator created
-
Create a secret with credentials to log into the image registry in
netapp-acc-operatornamespace.[netapp-user@rhel7 ~]$ oc create secret docker-registry astra-registry-cred --docker-server=astra-registry.apps.ocp-vmw.cie.netapp.com --docker-username=ocp-user --docker-password=password -n netapp-acc-operator secret/astra-registry-cred created
-
Log into the Red Hat OpenShift GUI console with cluster-admin access.
-
Select Administrator from the Perspective drop down.
-
Navigate to Operators > OperatorHub and search for Astra.
-
Select
netapp-acc-operatortile and clickInstall.
-
On the Install Operator screen, accept all default parameters and click
Install.
-
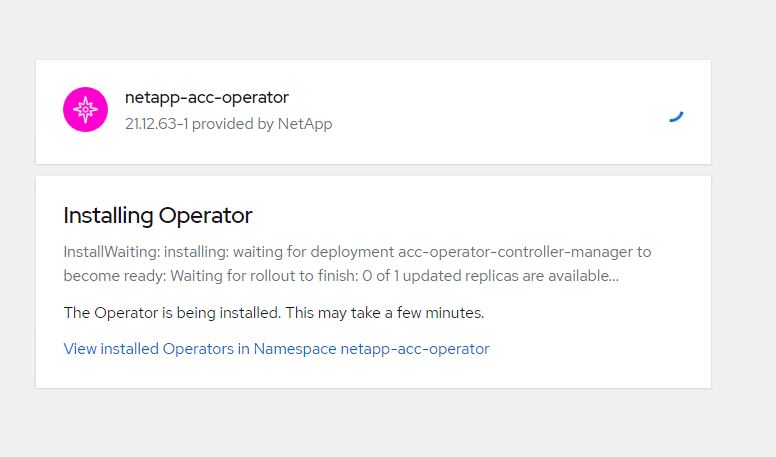
Wait for the operator installation to complete.
-
Once the operator installation succeeds, navigate to click on
View Operator.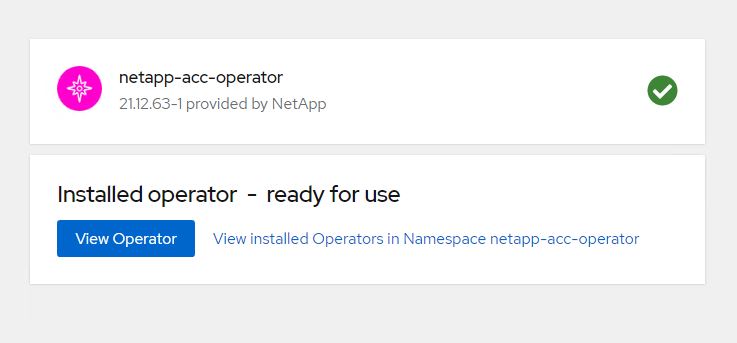
-
Then click on
Create Instancein Astra Control Center tile in the operator.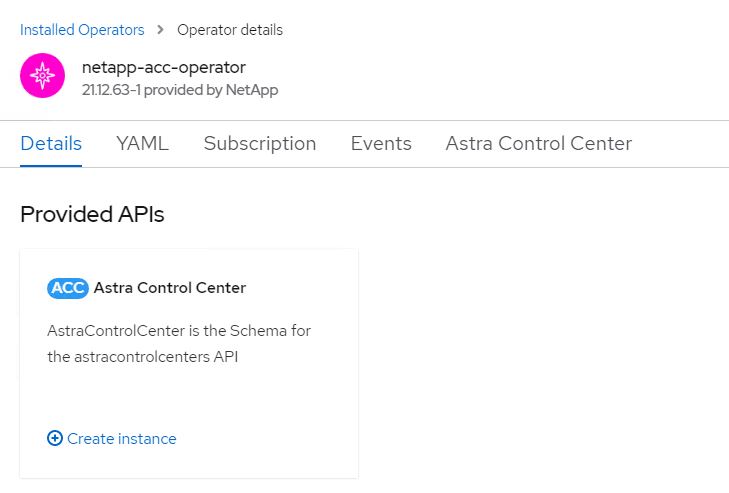
-
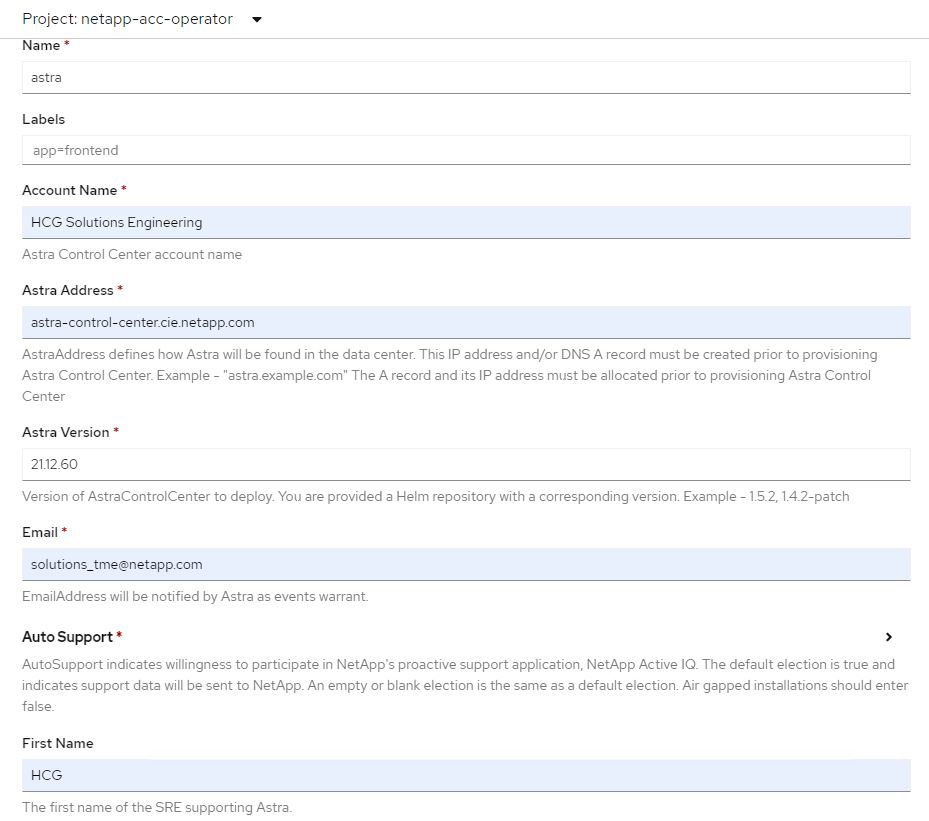
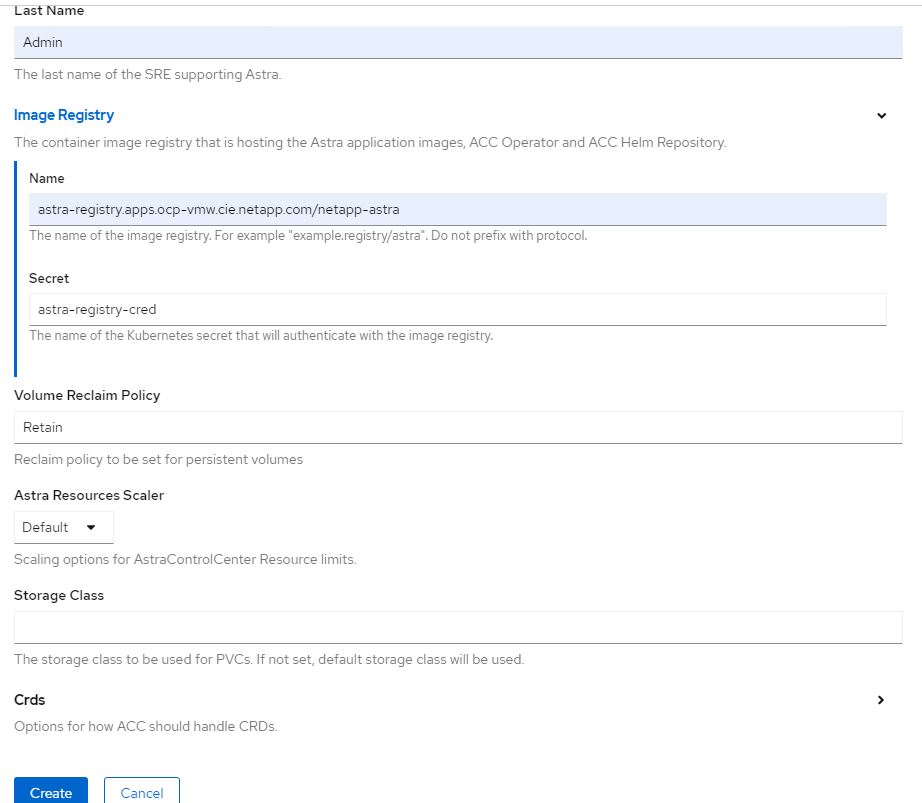
Fill the
Create AstraControlCenterform fields and clickCreate.-
Optionally edit the Astra Control Center instance name.
-
Optionally enable or disable Auto Support. Retaining Auto Support functionality is recommended.
-
Enter the FQDN for Astra Control Center.
-
Enter the Astra Control Center version; the latest is displayed by default.
-
Enter an account name for Astra Control Center and admin details like first name, last name and email address.
-
Enter the volume reclaim policy, default is Retain.
-
In Image Registry, enter the FQDN for your registry along with the organization name as it was given while pushing the images to the registry (in this example,
astra-registry.apps.ocp-vmw.cie.netapp.com/netapp-astra) -
If you use a registry that requires authentication, enter the secret name in Image Registry section.
-
Configure scaling options for Astra Control Center resource limits.
-
Enter the storage class name if you want to place PVCs on a non-default storage class.
-
Define CRD handling preferences.
-
-
To use Ansible playbooks to deploy Astra Control Center, you need an Ubuntu/RHEL machine with Ansible installed. Follow the procedures here for Ubuntu and RHEL.
-
Clone the GitHub repository that hosts the Ansible content.
git clone https://github.com/NetApp-Automation/na_astra_control_suite.git -
Log into the NetApp Support site and download the latest version of NetApp Astra Control Center. To do so requires a license attached to your NetApp account. After you download the tarball, transfer it to the workstation.
To get started with a trial license for Astra Control, visit the Astra registration site. -
Create or obtain the kubeconfig file with admin access to the OpenShift cluster on which Astra Control Center is to be installed.
-
Change the directory to the na_astra_control_suite.
cd na_astra_control_suite -
Edit the
vars/vars.ymlfile, and fill in the variables with the required information.#Define whether or not to push the Astra Control Center images to your private registry [Allowed values: yes, no] push_images: yes #The directory hosting the Astra Control Center installer installer_directory: /home/admin/ #Specify the ingress type. Allowed values - "AccTraefik" or "Generic" #"AccTraefik" if you want the installer to create a LoadBalancer type service to access ACC, requires MetalLB or similar. #"Generic" if you want to create or configure ingress controller yourself, installer just creates a ClusterIP service for traefik. ingress_type: "AccTraefik" #Name of the Astra Control Center installer (Do not include the extension, just the name) astra_tar_ball_name: astra-control-center-22.04.0 #The complete path to the kubeconfig file of the kubernetes/openshift cluster Astra Control Center needs to be installed to. hosting_k8s_cluster_kubeconfig_path: /home/admin/cluster-kubeconfig.yml #Namespace in which Astra Control Center is to be installed astra_namespace: netapp-astra-cc #Astra Control Center Resources Scaler. Leave it blank if you want to accept the Default setting. astra_resources_scaler: Default #Storageclass to be used for Astra Control Center PVCs, it must be created before running the playbook [Leave it blank if you want the PVCs to use default storageclass] astra_trident_storageclass: basic #Reclaim Policy for Astra Control Center Persistent Volumes [Allowed values: Retain, Delete] storageclass_reclaim_policy: Retain #Private Registry Details astra_registry_name: "docker.io" #Whether the private registry requires credentials [Allowed values: yes, no] require_reg_creds: yes #If require_reg_creds is yes, then define the container image registry credentials #Usually, the registry namespace and usernames are same for individual users astra_registry_namespace: "registry-user" astra_registry_username: "registry-user" astra_registry_password: "password" #Kuberenets/OpenShift secret name for Astra Control Center #This name will be assigned to the K8s secret created by the playbook astra_registry_secret_name: "astra-registry-credentials" #Astra Control Center FQDN acc_fqdn_address: astra-control-center.cie.netapp.com #Name of the Astra Control Center instance acc_account_name: ACC Account Name #Administrator details for Astra Control Center admin_email_address: admin@example.com admin_first_name: Admin admin_last_name: Admin -
Run the playbook to deploy Astra Control Center. The playbook requires root privileges for certain configurations.
If the user running the playbook is root or has passwordless sudo configured, then run the following command to run the playbook.
ansible-playbook install_acc_playbook.ymlIf the user has password-based sudo access configured, run the following command to run the playbook, and then enter the sudo password.
ansible-playbook install_acc_playbook.yml -K
Post Install Steps
-
It might take several minutes for the installation to complete. Verify that all the pods and services in the
netapp-astra-ccnamespace are up and running.[netapp-user@rhel7 ~]$ oc get all -n netapp-astra-cc
-
Check the
acc-operator-controller-managerlogs to ensure that the installation is completed.[netapp-user@rhel7 ~]$ oc logs deploy/acc-operator-controller-manager -n netapp-acc-operator -c manager -f
The following message indicates the successful installation of Astra Control Center. {"level":"info","ts":1624054318.029971,"logger":"controllers.AstraControlCenter","msg":"Successfully Reconciled AstraControlCenter in [seconds]s","AstraControlCenter":"netapp-astra-cc/astra","ae.Version":"[21.12.60]"} -
The username for logging into Astra Control Center is the email address of the administrator provided in the CRD file and the password is a string
ACC-appended to the Astra Control Center UUID. Run the following command:[netapp-user@rhel7 ~]$ oc get astracontrolcenters -n netapp-astra-cc NAME UUID astra 345c55a5-bf2e-21f0-84b8-b6f2bce5e95f
In this example, the password is ACC-345c55a5-bf2e-21f0-84b8-b6f2bce5e95f. -
Get the traefik service load balancer IP.
[netapp-user@rhel7 ~]$ oc get svc -n netapp-astra-cc | egrep 'EXTERNAL|traefik' NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE traefik LoadBalancer 172.30.99.142 10.61.186.181 80:30343/TCP,443:30060/TCP 16m
-
Add an entry in the DNS server pointing the FQDN provided in the Astra Control Center CRD file to the
EXTERNAL-IPof the traefik service.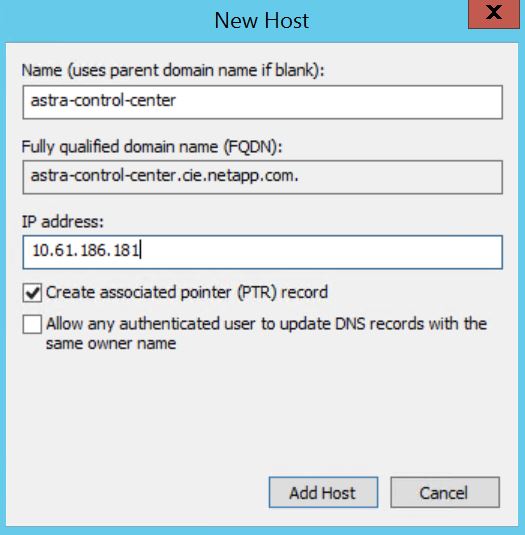
-
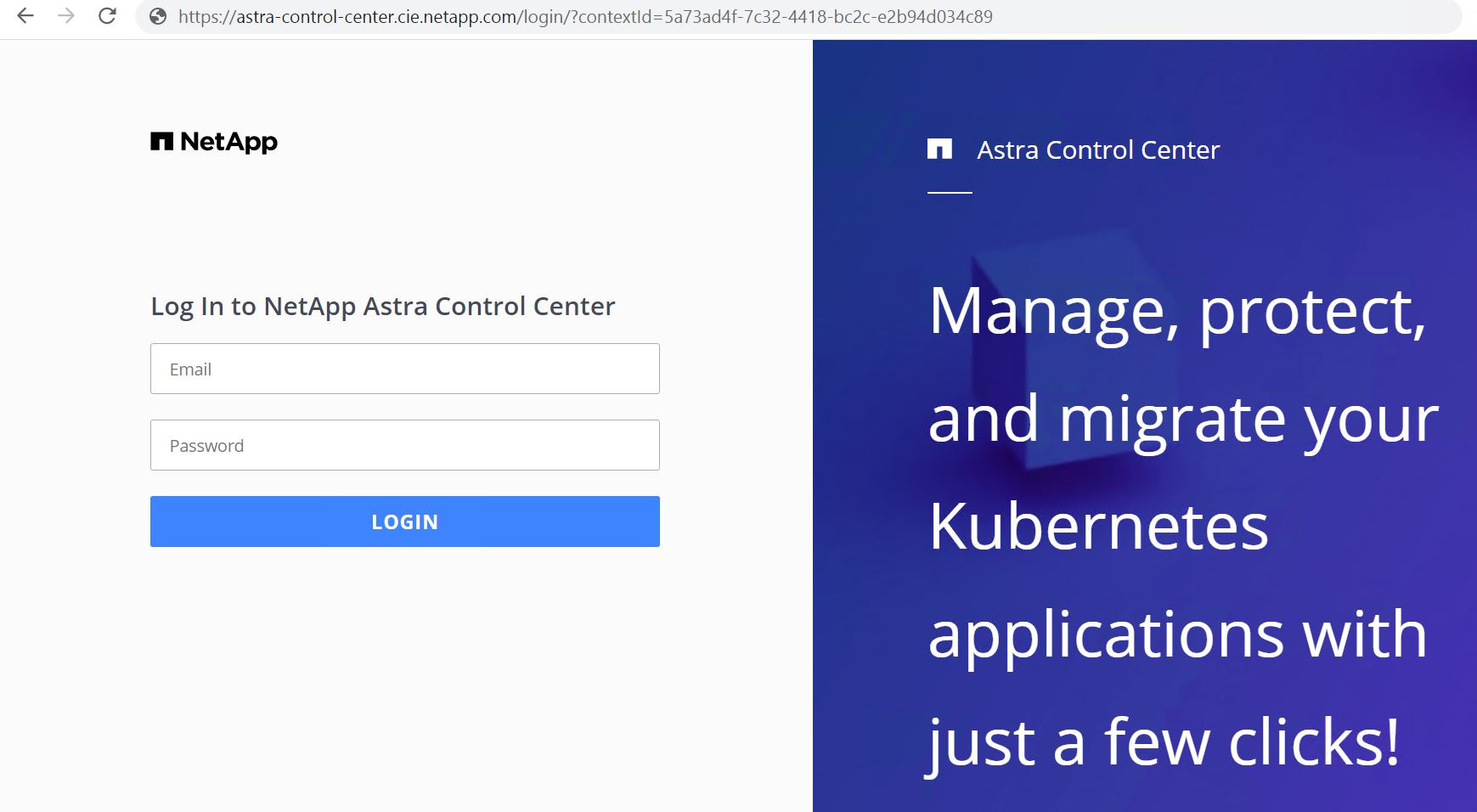
Log into the Astra Control Center GUI by browsing its FQDN.
-
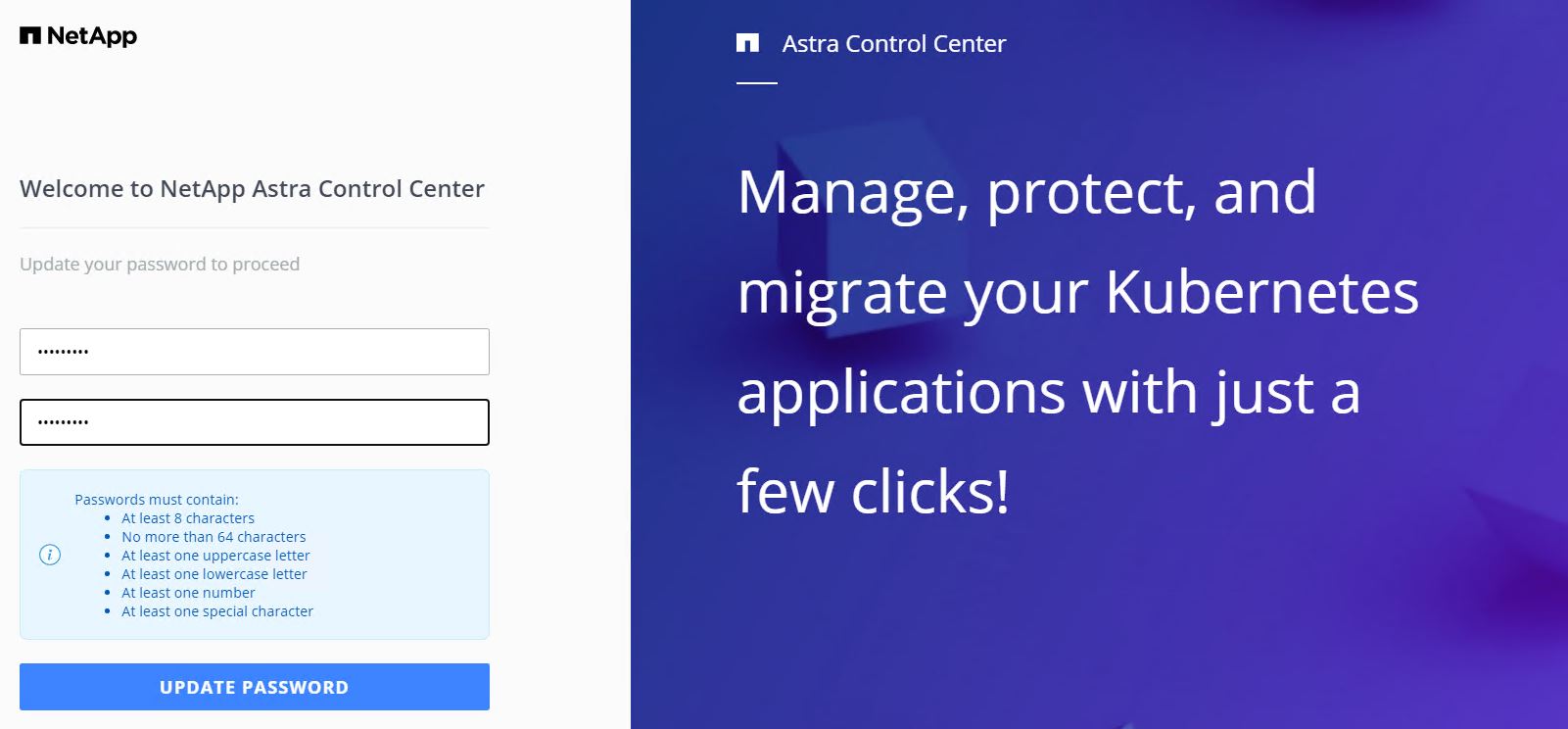
When you log into Astra Control Center GUI for the first time using the admin email address provided in CRD, you need to change the password.
-
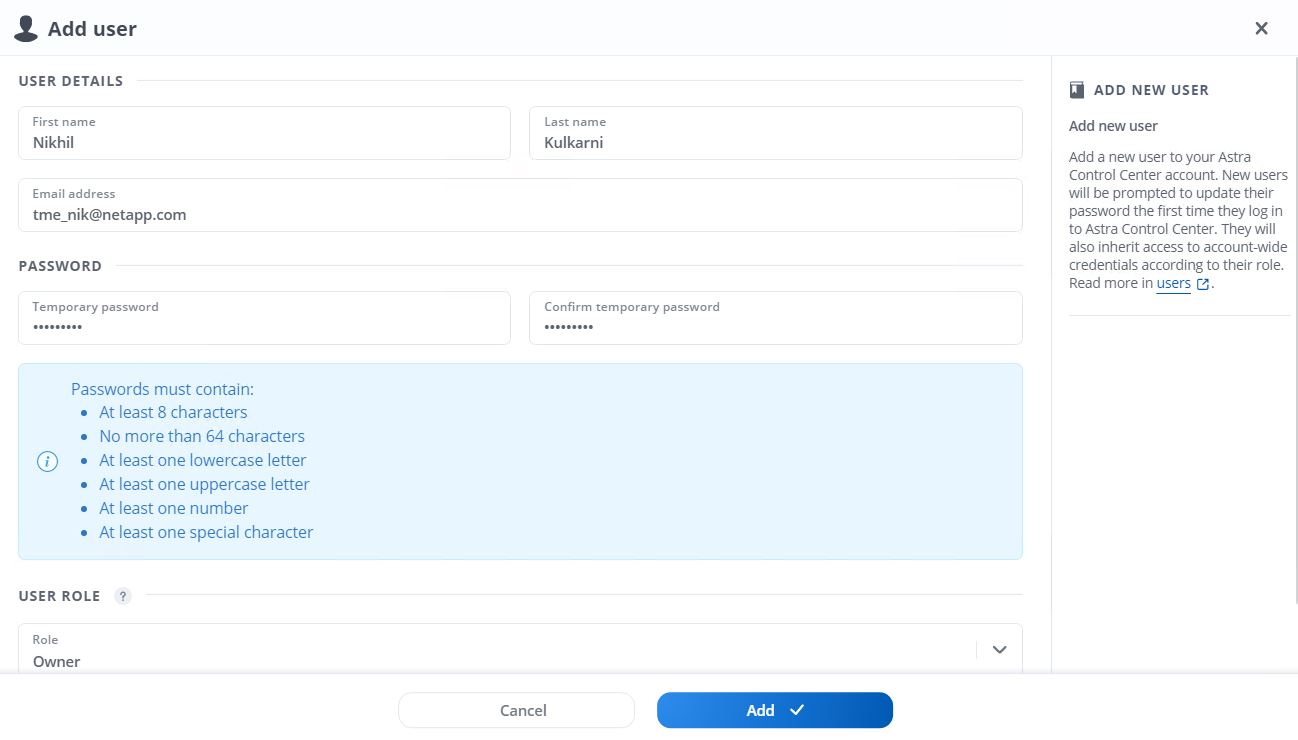
If you wish to add a user to Astra Control Center, navigate to Account > Users, click Add, enter the details of the user, and click Add.
-
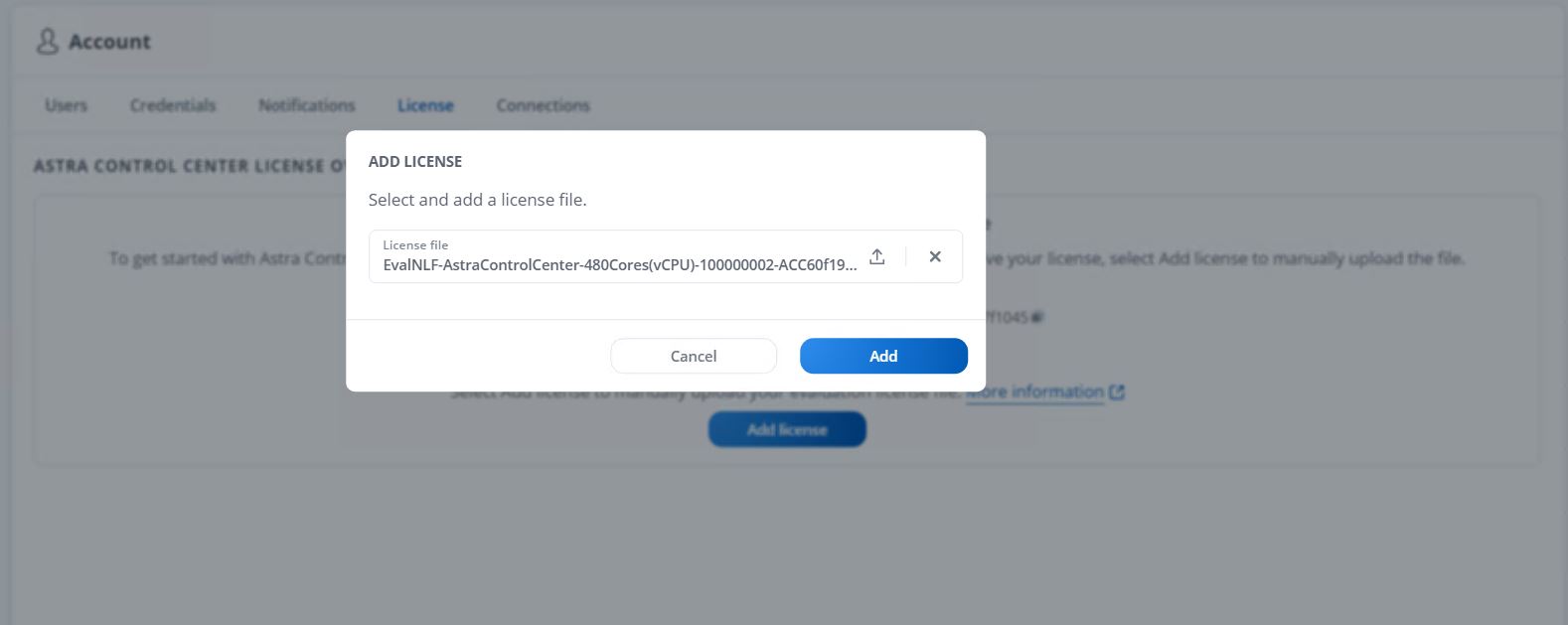
Astra Control Center requires a license for all of it’s functionalities to work. To add a license, navigate to Account > License, click Add License, and upload the license file.
If you encounter issues with the install or configuration of NetApp Astra Control Center, the knowledge base of known issues is available here.



