Verifying the integrity of the ONTAP tools for VMware vSphere 9.13 installation packages
 Suggest changes
Suggest changes


There are two methods available for customers to verify the integrity of their ONTAP tools installation packages.
-
Verifying the checksums
-
Verifying the signature
Checksums are provided on the download pages of OTV install packages. Users must verify the checksums of downloaded packages against the checksum provided on the download page.
Verifying the signature of the ONTAP tools OVA
The vApp install package is delivered in the form of a tarball. This tarball contains intermediate and root certificates for the virtual appliance along with a README file and an OVA package. The README file guides users on how to verify the integrity of vApp OVA package.
Customers must also upload the provided root and Intermediate certificate on vCenter version 7.0U3E and higher. For vCenter versions between 7.0.1 and 7.0.U3E the functionality of verifying certificate is not supported from VMware. Customers need not upload any certificate for vCenter versions 6.x.
Uploading the trusted root certificate to vCenter
-
Log in with the VMware vSphere Client to the vCenter Server.
-
Specify the username and password for administrator@vsphere.local or another member of the vCenter Single Sign-On Administrators group. If you specified a different domain during installation, log in as administrator@mydomain.
-
Navigate to the Certificate Management UI: a. From the Home menu, select Administration. b. Under Certificates, click Certificate Management.
-
If the system prompts you, enter the credentials of your vCenter Server.
-
Under Trusted Root Certificates, click Add.
-
Click browse and select the location of the certificate .pem file (OTV_OVA_INTER_ROOT_CERT_CHAIN.pem).
-
Click Add. The certificate is added to the store.
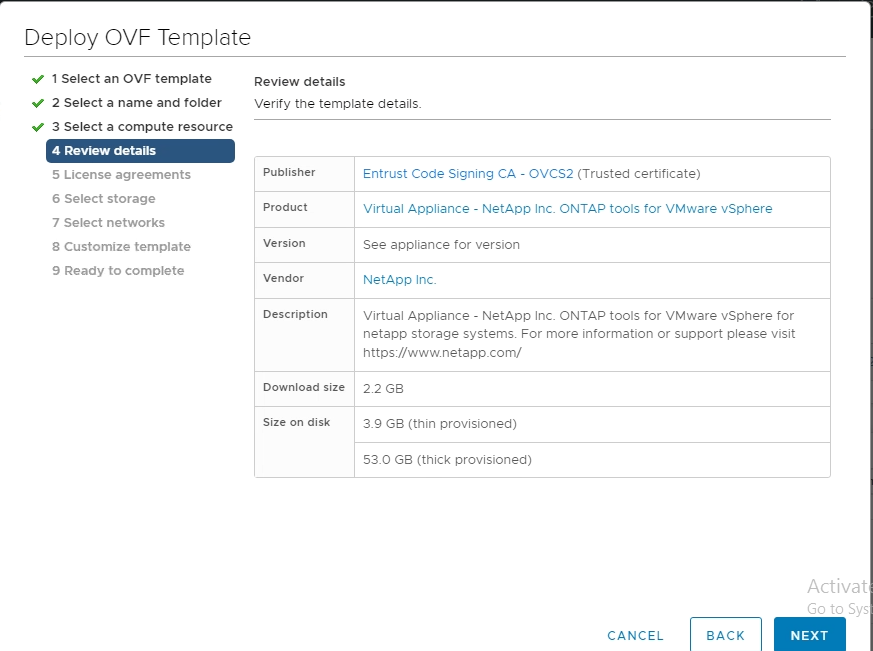
Refer to Add a Trusted Root Certificate to the Certificate Store for more information. While deploying a vApp (by using the OVA file), the digital signature for the vApp package can be verified on the 'Review details' page. If the downloaded vApp package is genuine, the 'Publisher' column displays 'Trusted Certificate' (As in the following screenshot).
Verifying the signature of the ONTAP tools ISO and SRA tar.gz
NetApp shares its code signing certificate with customers on the product download page, along with the product zip files for OTV-ISO and SRA.tgz.
From the code signing certificate users can extract the public key as below:
#> openssl x509 -in <code-sign-cert, pem file> -pubkey -noout > <public-key name>
Then public key should be used to verify the signature for iso and tgz product zip as below :
#> openssl dgst -sha256 -verify <public-key> -signature <signature-file> <binary-name>
Example:
#> openssl x509 -in OTV_ISO_CERT.pem -pubkey -noout > OTV_ISO.pub #> openssl dgst -sha256 -verify OTV_ISO.pub -signature netapp-ontap-tools-for-vmware-vsphere-9.12-upgrade-iso.sig netapp-ontap-tools-for-vmware-vsphere-9.12-upgrade.iso Verified OK => response


