Ransomware defense using replicated bucket with versioning
 Suggest changes
Suggest changes


Learn how to replicate objects to a secondary bucket using StorageGRID CloudMirror.
Not all applications and workloads are going to be compatible with object lock. Another option is to replicate the objects to a secondary bucket either in the same grid (preferably a different tenant with restricted access), or any other S3 endpoint with the StorageGRID platform service, CloudMirror.
StorageGRID CloudMirror is a component of StorageGRID that can be configured to replicate the objects of a bucket to a defined destination as they are ingested into the source bucket and does not replicate deletes. Because CloudMirror is an integrated component of StorageGRID, it cannot be turned off or manipulated by an S3 API-based attack. You can configure this replicated bucket with versioning enabled. In this scenario you need some automated cleanup of the replicated bucket's old versions that are safe to discard. For this, you can use the StorageGRID ILM policy engine. Create rules to manage the object placement based on non-current time for several days sufficient to have identified and recovered from an attack.
One downside to this approach is that it consumes more storage by having a complete second copy of the bucket plus multiple versions of the objects retained for some time. Additionally, the objects that were intentionally deleted from the primary bucket must be manually removed from the replicated bucket. There are other replication options outside of the product, such as NetApp CloudSync, that can replicate deletes for a similar solution. Another downside for the secondary bucket being versioning enabled and not object lock enabled is that there exists a number of privileged accounts that might be used to cause damage on the secondary location. The advantage is that it should be a unique account to that endpoint or tenant bucket and the compromise likely does not include access to accounts on the primary location or vice-versa.
After the source and destination buckets are created and the destination is configured with versioning, you can configure and enable replication, as follows:
-
To configure CloudMirror, create a platform services endpoint for the S3 destination.
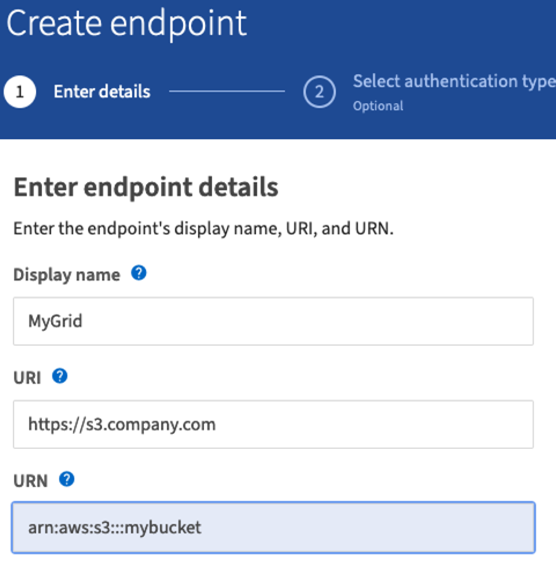
-
On the source bucket, configure replication to use the endpoint configured.
<ReplicationConfiguration> <Role></Role> <Rule> <Status>Enabled</Status> <Prefix></Prefix> <Destination> <Bucket>arn:aws:s3:::mybucket</Bucket> <StorageClass>STANDARD</StorageClass> </Destination> </Rule> </ReplicationConfiguration> -
Create ILM rules to manage the storage placement and version storage duration management. In this example, the non-current versions of the objects to store are configured.

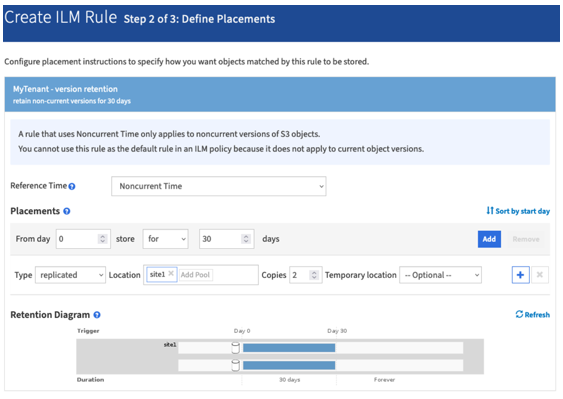
There are two copies in site 1 for 30 days. You also configure the rules for the current version of the objects based on using ingest time as reference time in the ILM rule to match the source bucket storage duration. The storage placement for the object versions can be erasure coded or replicated.

