管理ONTAP调解器
 建议更改
建议更改


管理 ONTAP Mediator,包括更改用户凭据、停止和重新启用服务、验证其运行状况以及安装或卸载 SCST 以进行主机维护。您还可以管理证书、例如重新生成自签名证书、将其替换为受信任的第三方证书以及解决证书相关问题。
更改用户名
您可以使用以下操作步骤更改用户名。
在安装了 ONTAP Mediator 的 Linux 主机上执行此任务。
如果无法访问此命令,则可能需要使用完整路径运行此命令,如以下示例所示:
/usr/local/bin/mediator_username
通过选择以下选项之一更改用户名:
-
选项(A):运行命令
mediator_change_user并对提示进行响应、如以下示例所示:[root@mediator-host ~]# mediator_change_user Modify the Mediator API username by entering the following values: Mediator API User Name: mediatoradmin Password: New Mediator API User Name: mediator The account username has been modified successfully. [root@mediator-host ~]# -
选项(b):运行以下命令:
MEDIATOR_USERNAME=mediator MEDIATOR_PASSWORD=mediator2 MEDIATOR_NEW_USERNAME=mediatoradmin mediator_change_user[root@mediator-host ~]# MEDIATOR_USERNAME=mediator MEDIATOR_PASSWORD='mediator2' MEDIATOR_NEW_USERNAME=mediatoradmin mediator_change_user The account username has been modified successfully. [root@mediator-host ~]#
更改密码
您可以使用以下操作步骤更改密码。
在安装了 ONTAP Mediator 的 Linux 主机上执行此任务。
如果无法访问此命令,则可能需要使用完整路径运行此命令,如以下示例所示:
/usr/local/bin/mediator_change_password
通过选择以下选项之一更改密码:
-
选项(A):运行
mediator_change_password命令并对提示进行响应、如以下示例所示:[root@mediator-host ~]# mediator_change_password Change the Mediator API password by entering the following values: Mediator API User Name: mediatoradmin Old Password: New Password: Confirm Password: The password has been updated successfully. [root@mediator-host ~]# -
选项(b):运行以下命令:
MEDIATOR_USERNAME=mediatoradmin MEDIATOR_PASSWORD=mediator1 MEDIATOR_NEW_PASSWORD=mediator2 mediator_change_password此示例显示密码已从"mediator1"更改为"mediator2"。
[root@mediator-host ~]# MEDIATOR_USERNAME=mediatoradmin MEDIATOR_PASSWORD=mediator1 MEDIATOR_NEW_PASSWORD=mediator2 mediator_change_password The password has been updated successfully. [root@mediator-host ~]#
停止 ONTAP 调解器
要停止 ONTAP 调解器,请执行以下步骤:
-
停止 ONTAP 调解器:
systemctl stop ontap_mediator -
停止SCST:
systemctl stop mediator-scst -
禁用 ONTAP 调解器和 SCST:
systemctl disable ontap_mediator mediator-scst
重新启用 ONTAP 调解器
要重新启用 ONTAP 调解器,请执行以下步骤:
-
启用 ONTAP 调解器和 SCST:
systemctl enable ontap_mediator mediator-scst -
启动SCST:
systemctl start mediator-scst -
启动ONTAP调解器:
systemctl start ontap_mediator
验证 ONTAP 调解器是否正常运行
安装 ONTAP Mediator 后,请验证它是否成功运行。
-
查看 ONTAP 调解器的状态:
-
systemctl status ontap_mediator[root@scspr1915530002 ~]# systemctl status ontap_mediator ontap_mediator.service - ONTAP Mediator Loaded: loaded (/etc/systemd/system/ontap_mediator.service; enabled; vendor preset: disabled) Active: active (running) since Mon 2022-04-18 10:41:49 EDT; 1 weeks 0 days ago Process: 286710 ExecStop=/bin/kill -s INT $MAINPID (code=exited, status=0/SUCCESS) Main PID: 286712 (uwsgi) Status: "uWSGI is ready" Tasks: 3 (limit: 49473) Memory: 139.2M CGroup: /system.slice/ontap_mediator.service ├─286712 /opt/netapp/lib/ontap_mediator/pyenv/bin/uwsgi --ini /opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini ├─286716 /opt/netapp/lib/ontap_mediator/pyenv/bin/uwsgi --ini /opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini └─286717 /opt/netapp/lib/ontap_mediator/pyenv/bin/uwsgi --ini /opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini [root@scspr1915530002 ~]# -
systemctl status mediator-scst[root@scspr1915530002 ~]# systemctl status mediator-scst Loaded: loaded (/etc/systemd/system/mediator-scst.service; enabled; vendor preset: disabled) Active: active (running) since Mon 2022-04-18 10:41:47 EDT; 1 weeks 0 days ago Process: 286595 ExecStart=/etc/init.d/scst start (code=exited, status=0/SUCCESS) Main PID: 286662 (iscsi-scstd) Tasks: 1 (limit: 49473) Memory: 1.2M CGroup: /system.slice/mediator-scst.service └─286662 /usr/local/sbin/iscsi-scstd [root@scspr1915530002 ~]#
-
-
确认 ONTAP 调解器使用的端口:
netstat[root@scspr1905507001 ~]# netstat -anlt | grep -E '3260|31784' tcp 0 0 0.0.0.0:31784 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:3260 0.0.0.0:* LISTEN tcp6 0 0 :::3260 :::* LISTEN
卸载 ONTAP 调解器
如有必要,您可以删除 ONTAP Mediator。
您必须先断开 ONTAP 调解器与 ONTAP 之间的连接,然后才能将其移除。
在安装了 ONTAP Mediator 的 Linux 主机上执行此任务。
如果无法访问此命令,则可能需要使用完整路径运行此命令,如以下示例所示:
/usr/local/bin/uninstall_ontap_mediator
-
卸载 ONTAP 调解器:
uninstall_ontap_mediator[root@mediator-host ~]# uninstall_ontap_mediator ONTAP Mediator: Self Extracting Uninstaller + Removing ONTAP Mediator. (Log: /tmp/ontap_mediator.GmRGdA/uninstall_ontap_mediator/remove.log) + Remove successful. [root@mediator-host ~]#
重新生成临时自签名证书
从ONTAP调解器1.7开始、您可以使用以下过程重新生成临时自签名证书。

|
只有运行ONTAP调解器1.7或更高版本的系统才支持此过程。 |
-
在安装了 ONTAP Mediator 的 Linux 主机上执行此任务。
-
仅当安装 ONTAP 调解器后,由于主机的主机名或 IP 地址发生更改而导致生成的自签名证书已过时时,您才可以执行此任务。
-
在临时自签名证书被可信的第三方证书替换后、您不能使用此任务重新生成证书。如果没有自签名证书、则发生原因此操作步骤将失败。
要为当前主机重新生成新的临时自签名证书、请执行以下步骤:
-
重新启动 ONTAP 调解器:
./make_self_signed_certs.sh overwrite[root@xyz000123456 ~]# cd /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config [root@xyz000123456 server_config]# ./make_self_signed_certs.sh overwrite Adding Subject Alternative Names to the self-signed server certificate # # OpenSSL example configuration file. Generating self-signed certificates Generating RSA private key, 4096 bit long modulus (2 primes) ..................................................................................................................................................................++++ ........................................................++++ e is 65537 (0x010001) Generating a RSA private key ................................................++++ .............................................................................................................................................++++ writing new private key to 'ontap_mediator_server.key' ----- Signature ok subject=C = US, ST = California, L = San Jose, O = "NetApp, Inc.", OU = ONTAP Core Software, CN = ONTAP Mediator, emailAddress = support@netapp.com Getting CA Private Key
将自签名证书替换为受信任的第三方证书
如果支持、您可以将自签名证书替换为受信任的第三方证书。

|
|
-
在安装了 ONTAP Mediator 的 Linux 主机上执行此任务。
-
如果生成的自签名证书需要替换为从受信任的从属证书颁发机构(CA)获取的证书、则可以执行此任务。为此、您应有权访问可信的公共密钥基础架构(PKI)颁发机构。
-
下图显示了每个ONTAP调解器证书的用途。
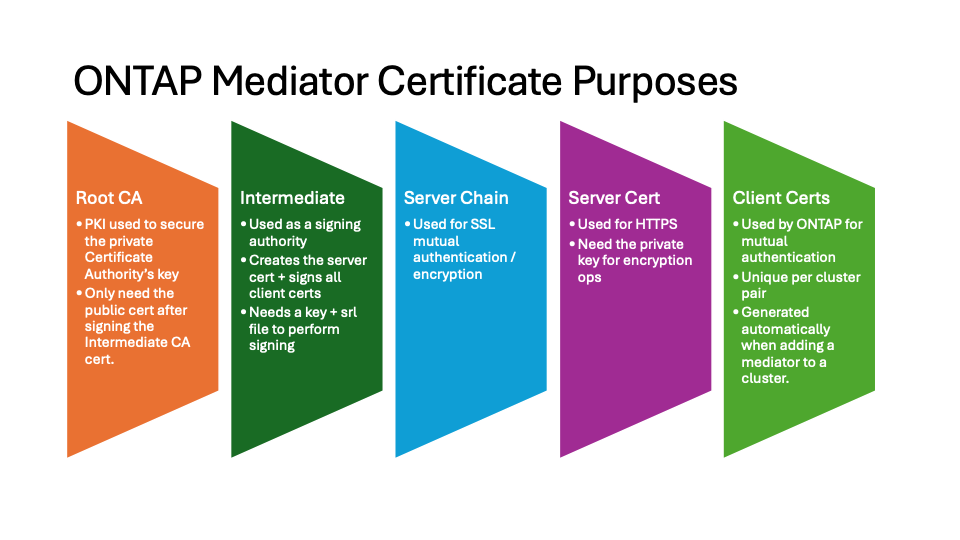
-
下图显示了 Web 服务器设置和 ONTAP Mediator 设置的配置。
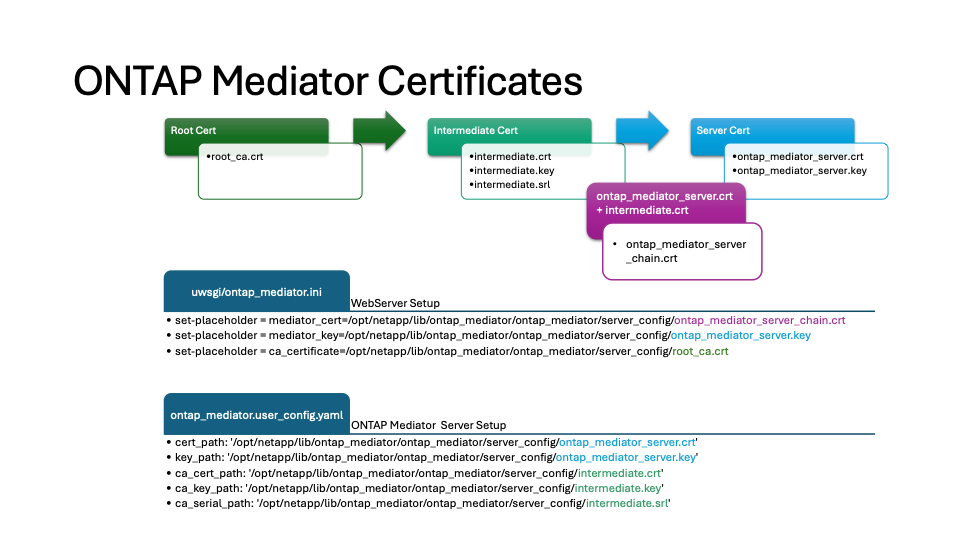
第1步:从颁发CA证书的第三方获取证书
您可以使用以下操作步骤从PKI颁发机构获取证书。
以下示例说明了如何将自签名证书角色替换为位于的第三方证书角色 /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/。

|
该示例说明了 ONTAP 调解器所需证书的必要标准。您可以通过与此操作步骤不同的方式从PKI颁发机构获取证书。根据您的业务需求调整此过程。 |
-
创建私钥和配置文件,PKI颁发机构将使用这些密钥 `intermediate.key`和配置文件 `openssl_ca.cnf`来生成证书。
-
生成私钥
intermediate.key:-
示例 *
-
openssl genrsa -aes256 -out intermediate.key 4096-
配置文件
openssl_ca.cnf(位于/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/openssl_ca.cnf)定义生成的证书必须具有的属性。
-
-
使用私钥和配置文件创建证书签名请求
intermediate.csr:-
示例: *
openssl req -key <private_key_name>.key -new -out <certificate_csr_name>.csr -config <config_file_name>.cnf
[root@scs000216655 server_config]# openssl req -key intermediate.key -new -config openssl_ca.cnf -out intermediate.csr Enter pass phrase for intermediate.key: [root@scs000216655 server_config]# cat intermediate.csr -----BEGIN CERTIFICATE REQUEST----- <certificate_value> -----END CERTIFICATE REQUEST-----
-
-
将证书签名请求发送 `intermediate.csr`到PKI颁发机构进行签名。
PKI 机构验证请求并签署
.csr,生成证书intermediate.crt。此外,您还需要获得 `root_ca.crt`签署的证书 `intermediate.crt`来自 PKI 机构的证书。对于SnapMirror业务连续性 (SM-BC) 集群,您必须添加 `intermediate.crt`和 `root_ca.crt`证书到ONTAP集群。看"为 SnapMirror 主动同步配置 ONTAP 调解器和集群"。
-
创建私钥和配置文件,PKI颁发机构将使用这些密钥 `ca.key`和配置文件 `openssl_ca.cnf`来生成证书。
-
生成私钥
ca.key:-
示例 *
-
openssl genrsa -aes256 -out ca.key 4096-
配置文件
openssl_ca.cnf(位于/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/openssl_ca.cnf)定义生成的证书必须具有的属性。
-
-
使用私钥和配置文件创建证书签名请求
ca.csr:-
示例: *
openssl req -key <private_key_name>.key -new -out <certificate_csr_name>.csr -config <config_file_name>.cnf
[root@scs000216655 server_config]# openssl req -key ca.key -new -config openssl_ca.cnf -out ca.csr Enter pass phrase for ca.key: [root@scs000216655 server_config]# cat ca.csr -----BEGIN CERTIFICATE REQUEST----- <certificate_value> -----END CERTIFICATE REQUEST-----
-
-
将证书签名请求发送 `ca.csr`到PKI颁发机构进行签名。
PKI授权机构验证请求并签署
.csr,生成证书ca.crt。此外、您还需要从PKI颁发机构获取 `root_ca.crt that signed the `ca.crt`证书。对于SnapMirror业务连续性(SM-BC)集群、必须将和证书添加 ca.crtroot_ca.crt到ONTAP集群。请参阅。 "为 SnapMirror 主动同步配置 ONTAP 调解器和集群"
第2步:使用第三方CA认证签名生成服务器证书
服务器证书必须由专用密钥和第三方证书 intermediate.crt`签名 `intermediate.key。此外、配置文件 `/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/openssl_server.cnf`还包含某些属性、用于指定OpenSSL颁发的服务器证书所需的属性。
以下命令可生成服务器证书。
-
要生成服务器证书签名请求(CSR)、请从文件夹运行以下命令
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config:openssl req -config openssl_server.cnf -extensions v3_req -nodes -newkey rsa:4096 -sha512 -keyout ontap_mediator_server.key -out ontap_mediator_server.csr -
要从 CSR 生成服务器证书,请从 `/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config`文件夹:
这些文件是从PKI颁发机构获得的。如果您使用的是其他证书名称、请将和 `intermediate.key`替换 `intermediate.crt`为相关文件名。 openssl x509 -extfile openssl_server.cnf -extensions v3_req -CA intermediate.crt -CAkey intermediate.key -CAcreateserial -sha512 -days 1095 -req -in ontap_mediator_server.csr -out ontap_mediator_server.crt-
`-CAcreateserial`选项用于生成 `intermediate.srl`文件。
-
服务器证书必须由专用密钥和第三方证书 ca.crt`签名 `ca.key。此外、配置文件 `/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/openssl_server.cnf`还包含某些属性、用于指定OpenSSL颁发的服务器证书所需的属性。
以下命令可生成服务器证书。
-
要生成服务器证书签名请求(CSR)、请从文件夹运行以下命令
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config:openssl req -config openssl_server.cnf -extensions v3_req -nodes -newkey rsa:4096 -sha512 -keyout ontap_mediator_server.key -out ontap_mediator_server.csr -
要从 CSR 生成服务器证书,请从 `/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config`文件夹:
这些文件是从PKI颁发机构获得的。如果您使用的是其他证书名称、请将和 `ca.key`替换 `ca.crt`为相关文件名。 openssl x509 -extfile openssl_server.cnf -extensions v3_req -CA ca.crt -CAkey ca.key -CAcreateserial -sha512 -days 1095 -req -in ontap_mediator_server.csr -out ontap_mediator_server.crt-
`-CAcreateserial`选项用于生成 `ca.srl`文件。
-
第3步:在ONTAP调解器配置中替换新的第三方CA证书和服务器证书
证书配置通过位于以下位置的配置文件提供给 ONTAP 调解器 /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.config.yaml 。此文件包含以下属性:
cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.srl'
-
cert_path和key_path是服务器证书变量。 -
ca_cert_path,ca_key_path,和ca_serial_path是CA证书变量。
-
将所有文件替换
intermediate.*为第三方证书。 -
从和证书创建证书链
intermediate.crtontap_mediator_server.crt:cat ontap_mediator_server.crt intermediate.crt > ontap_mediator_server_chain.crt -
更新 `/opt/netapp/lib/ontap_mediator/uvicorn/config.json`文件。
更新
ssl_keyfile,ssl_certfile, 和ssl_ca_certs:ssl_keyfile:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyssl_certfile:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtssl_ca_certs:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
这
ssl_keyfile`值是关键路径 `ontap_mediator_server.crt`文件,即 `ontap_mediator_server.key。 -
这 `ssl_certfile`值是 `ontap_mediator_server_chain.crt`文件。
-
这 `ssl_ca_certs`值是 `root_ca.crt`文件。
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
证书配置通过位于以下位置的配置文件提供给 ONTAP 调解器 /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.config.yaml 。此文件包含以下属性:
cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.srl'
-
cert_path和key_path是服务器证书变量。 -
ca_cert_path,ca_key_path,和ca_serial_path是CA证书变量。
-
将所有文件替换
intermediate.*为第三方证书。 -
从和证书创建证书链
intermediate.crtontap_mediator_server.crt:cat ontap_mediator_server.crt intermediate.crt > ontap_mediator_server_chain.crt -
更新
/opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini文件。更新、和的值
mediator_certmediator_keyca_certificate:set-placeholder = mediator_cert = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtset-placeholder = mediator_key = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyset-placeholder = ca_certificate = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
mediator_cert`值是文件的路径 `ontap_mediator_server_chain.crt。 -
mediator_key value`是文件中的密钥路径 `ontap_mediator_server.crt,即ontap_mediator_server.key。 -
ca_certificate`值是文件的路径 `root_ca.crt。
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
证书配置通过位于以下位置的配置文件提供给 ONTAP 调解器 /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.config.yaml 。此文件包含以下属性:
cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.srl'
-
cert_path和key_path是服务器证书变量。 -
ca_cert_path,ca_key_path,和ca_serial_path是CA证书变量。
-
将所有文件替换
ca.*为第三方证书。 -
从和证书创建证书链
ca.crtontap_mediator_server.crt:cat ontap_mediator_server.crt ca.crt > ontap_mediator_server_chain.crt -
更新
/opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini文件。更新、和的值
mediator_certmediator_keyca_certificate:set-placeholder = mediator_cert = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtset-placeholder = mediator_key = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyset-placeholder = ca_certificate = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
mediator_cert`值是文件的路径 `ontap_mediator_server_chain.crt。 -
mediator_key value`是文件中的密钥路径 `ontap_mediator_server.crt,即ontap_mediator_server.key。 -
ca_certificate`值是文件的路径 `root_ca.crt。
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
第4步:(可选)为第三方证书使用其他路径或名称
您可以使用与以外的其他名称的第三方证书、也可以 `intermediate.*`将第三方证书存储在其他位置。
-
配置
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.user_config.yaml文件以覆盖文件中的默认变量值ontap_mediator.config.yaml。如果您是从PKI颁发机构获得
intermediate.crt的,并且将其私钥存储intermediate.key在该位置/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config,则该ontap_mediator.user_config.yaml文件应类似于以下示例:如果您曾 intermediate.crt对证书签名ontap_mediator_server.crt、则会生成此intermediate.srl文件。有关详细信息、请参见 第2步:使用第三方CA认证签名生成服务器证书 。[root@scs000216655 server_config]# cat ontap_mediator.user_config.yaml # This config file can be used to override the default settings in ontap_mediator.config.yaml # To override a setting, copy the property key from ontap_mediator.config.yaml to this file and # set the property to the desired value. e.g., # # The default value for 'default_mailboxes_per_target' is 4 in ontap_mediator.config.yaml # # To override this value with 6 mailboxes per target, add the following key/value pair # below this comment: # # 'default_mailboxes_per_target': 6 # cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.srl'
-
如果您使用的证书结构 `root_ca.crt`证书提供了 `intermediate.crt`签署证书 `ontap_mediator_server.crt`证书,从创建证书链 `intermediate.crt`和 `ontap_mediator_server.crt`证书:
您应已在此过程的前面部分从PKI颁发机构获取 intermediate.crt和ontap_mediator_server.crt证书。cat ontap_mediator_server.crt intermediate.crt > ontap_mediator_server_chain.crt -
更新 `/opt/netapp/lib/ontap_mediator/uvicorn/config.json`文件。
更新
ssl_keyfile,ssl_certfile, 和ssl_ca_certs:ssl_keyfile:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyssl_certfile:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtssl_ca_certs:/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
这
ssl_keyfile`值是关键路径 `ontap_mediator_server.crt`文件,即 `ontap_mediator_server.key。 -
这 `ssl_certfile`值是 `ontap_mediator_server_chain.crt`文件。
-
这 `ssl_ca_certs`值是 `root_ca.crt`文件。
对于SnapMirror业务连续性 (SM-BC) 集群,您必须添加 `intermediate.crt`和 `root_ca.crt`证书到ONTAP集群。看"为 SnapMirror 主动同步配置 ONTAP 调解器和集群"。
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
-
当配置文件中的证书更新后,重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
您可以使用与以外的其他名称的第三方证书、也可以 `intermediate.*`将第三方证书存储在其他位置。
-
配置
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.user_config.yaml文件以覆盖文件中的默认变量值ontap_mediator.config.yaml。如果您是从PKI颁发机构获得
intermediate.crt的,并且将其私钥存储intermediate.key在该位置/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config,则该ontap_mediator.user_config.yaml文件应类似于以下示例:如果您曾 intermediate.crt对证书签名ontap_mediator_server.crt、则会生成此intermediate.srl文件。有关详细信息、请参见 第2步:使用第三方CA认证签名生成服务器证书 。[root@scs000216655 server_config]# cat ontap_mediator.user_config.yaml # This config file can be used to override the default settings in ontap_mediator.config.yaml # To override a setting, copy the property key from ontap_mediator.config.yaml to this file and # set the property to the desired value. e.g., # # The default value for 'default_mailboxes_per_target' is 4 in ontap_mediator.config.yaml # # To override this value with 6 mailboxes per target, add the following key/value pair # below this comment: # # 'default_mailboxes_per_target': 6 # cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/intermediate.srl'
-
如果您使用的证书结构 `root_ca.crt`证书提供了 `intermediate.crt`签署证书 `ontap_mediator_server.crt`证书,从创建证书链 `intermediate.crt`和 `ontap_mediator_server.crt`证书:
您应已在此过程的前面部分从PKI颁发机构获取 intermediate.crt和ontap_mediator_server.crt证书。cat ontap_mediator_server.crt intermediate.crt > ontap_mediator_server_chain.crt -
更新
/opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini文件。更新、和的值
mediator_certmediator_keyca_certificate:set-placeholder = mediator_cert = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtset-placeholder = mediator_key = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyset-placeholder = ca_certificate = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
mediator_cert`值是文件的路径 `ontap_mediator_server_chain.crt。 -
mediator_key`值是文件中的密钥路径 `ontap_mediator_server.crt,即ontap_mediator_server.key。 -
ca_certificate`值是文件的路径 `root_ca.crt。对于SnapMirror业务连续性 (SM-BC) 集群,您必须添加 `intermediate.crt`和 `root_ca.crt`证书到ONTAP集群。看"为 SnapMirror 主动同步配置 ONTAP 调解器和集群"。
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
-
当配置文件中的证书更新后,重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
您可以使用与以外的其他名称的第三方证书、也可以 `ca.*`将第三方证书存储在其他位置。
-
配置
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator.user_config.yaml文件以覆盖文件中的默认变量值ontap_mediator.config.yaml。如果您是从PKI颁发机构获得
ca.crt的,并且将其私钥存储ca.key在该位置/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config,则该ontap_mediator.user_config.yaml文件应类似于以下示例:如果您曾 ca.crt对证书签名ontap_mediator_server.crt、则会生成此ca.srl文件。有关详细信息、请参见 第2步:使用第三方CA认证签名生成服务器证书 。[root@scs000216655 server_config]# cat ontap_mediator.user_config.yaml # This config file can be used to override the default settings in ontap_mediator.config.yaml # To override a setting, copy the property key from ontap_mediator.config.yaml to this file and # set the property to the desired value. e.g., # # The default value for 'default_mailboxes_per_target' is 4 in ontap_mediator.config.yaml # # To override this value with 6 mailboxes per target, add the following key/value pair # below this comment: # # 'default_mailboxes_per_target': 6 # cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.crt' key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.key' ca_cert_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.crt' ca_key_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.key' ca_serial_path: '/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ca.srl'
-
如果您使用的证书结构中的
root_ca.crt证书提供了ca.crt用于对证书签名的证书ontap_mediator_server.crt、请从和证书创建证书链ca.crtontap_mediator_server.crt:您应已在此过程的前面部分从PKI颁发机构获取 ca.crt和ontap_mediator_server.crt证书。cat ontap_mediator_server.crt ca.crt > ontap_mediator_server_chain.crt -
更新
/opt/netapp/lib/ontap_mediator/uwsgi/ontap_mediator.ini文件。更新、和的值
mediator_certmediator_keyca_certificate:set-placeholder = mediator_cert = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server_chain.crtset-placeholder = mediator_key = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/ontap_mediator_server.keyset-placeholder = ca_certificate = /opt/netapp/lib/ontap_mediator/ontap_mediator/server_config/root_ca.crt-
mediator_cert`值是文件的路径 `ontap_mediator_server_chain.crt。 -
mediator_key`值是文件中的密钥路径 `ontap_mediator_server.crt,即ontap_mediator_server.key。 -
ca_certificate`值是文件的路径 `root_ca.crt。对于SnapMirror业务连续性(SM-BC)集群、必须将和证书添加 ca.crtroot_ca.crt到ONTAP集群。请参阅。 "为 SnapMirror 主动同步配置 ONTAP 调解器和集群"
-
-
验证新生成的证书的以下属性是否设置正确:
-
Linux组所有者:
netapp:netapp -
Linux权限:
600
-
-
-
当配置文件中的证书更新后,重新启动 ONTAP 调解器:
systemctl restart ontap_mediator
对证书相关问题进行故障排除
您可以检查证书的某些属性。
验证证书到期时间
使用以下命令确定证书有效期范围。
[root@mediator_host server_config]# openssl x509 -in intermediate.crt -text -noout
Certificate:
Data:
...
Validity
Not Before: Feb 22 19:57:25 2024 GMT
Not After : Feb 15 19:57:25 2029 GMT
[root@mediator_host server_config]# openssl x509 -in ca.crt -text -noout
Certificate:
Data:
...
Validity
Not Before: Feb 22 19:57:25 2024 GMT
Not After : Feb 15 19:57:25 2029 GMT
验证CA认证中的X509v3扩展
使用以下命令验证CA认证中的X509v3扩展。
在中定义的属性 v3_ca`将显示为 `X509v3 extensions`中 `intermediate.crt`的 `openssl_ca.cnf。
[root@mediator_host server_config]# pwd
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config
[root@mediator_host server_config]# cat openssl_ca.cnf
...
[ v3_ca ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, cRLSign, digitalSignature, keyCertSign
[root@mediator_host server_config]# openssl x509 -in intermediate.crt -text -noout
Certificate:
Data:
...
X509v3 extensions:
X509v3 Subject Key Identifier:
9F:06:FA:47:00:67:BA:B2:D4:82:70:38:B8:48:55:B5:24:DB:FC:27
X509v3 Authority Key Identifier:
keyid:9F:06:FA:47:00:67:BA:B2:D4:82:70:38:B8:48:55:B5:24:DB:FC:27
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
在中定义的属性 v3_ca`将显示为 `X509v3 extensions`中 `ca.crt`的 `openssl_ca.cnf。
[root@mediator_host server_config]# pwd
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config
[root@mediator_host server_config]# cat openssl_ca.cnf
...
[ v3_ca ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, cRLSign, digitalSignature, keyCertSign
[root@mediator_host server_config]# openssl x509 -in ca.crt -text -noout
Certificate:
Data:
...
X509v3 extensions:
X509v3 Subject Key Identifier:
9F:06:FA:47:00:67:BA:B2:D4:82:70:38:B8:48:55:B5:24:DB:FC:27
X509v3 Authority Key Identifier:
keyid:9F:06:FA:47:00:67:BA:B2:D4:82:70:38:B8:48:55:B5:24:DB:FC:27
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
验证服务器证书和使用者Alt名称中的X509v3扩展
。 v3_req 中定义的属性 openssl_server.cnf 配置文件显示为 X509v3 extensions 在证书中。
在下面的例子中,你可以获取 `alt_names`通过运行命令 `hostname -A`和 `hostname -I`在安装了 ONTAP Mediator 的 Linux VM 上。
请与网络管理员联系、了解变量的正确值。
[root@mediator_host server_config]# pwd
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config
[root@mediator_host server_config]# cat openssl_server.cnf
...
[ v3_req ]
basicConstraints = CA:false
extendedKeyUsage = serverAuth
keyUsage = keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = abc.company.com
DNS.2 = abc-v6.company.com
IP.1 = 1.2.3.4
IP.2 = abcd:abcd:abcd:abcd:abcd:abcd
[root@mediator_host server_config]# openssl x509 -in intermediate.crt -text -noout
Certificate:
Data:
...
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Key Usage:
Key Encipherment, Data Encipherment
X509v3 Subject Alternative Name:
DNS:abc.company.com, DNS:abc-v6.company.com, IP Address:1.2.3.4, IP Address:abcd:abcd:abcd:abcd:abcd:abcd
[root@mediator_host server_config]# pwd
/opt/netapp/lib/ontap_mediator/ontap_mediator/server_config
[root@mediator_host server_config]# cat openssl_server.cnf
...
[ v3_req ]
basicConstraints = CA:false
extendedKeyUsage = serverAuth
keyUsage = keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = abc.company.com
DNS.2 = abc-v6.company.com
IP.1 = 1.2.3.4
IP.2 = abcd:abcd:abcd:abcd:abcd:abcd
[root@mediator_host server_config]# openssl x509 -in ca.crt -text -noout
Certificate:
Data:
...
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Key Usage:
Key Encipherment, Data Encipherment
X509v3 Subject Alternative Name:
DNS:abc.company.com, DNS:abc-v6.company.com, IP Address:1.2.3.4, IP Address:abcd:abcd:abcd:abcd:abcd:abcd
验证专用密钥是否与证书匹配
您可以验证特定专用密钥是否与证书匹配。
对密钥和证书分别使用以下OpenSSL命令。
[root@mediator_host server_config]# openssl rsa -noout -modulus -in intermediate.key | openssl md5 Enter pass phrase for intermediate.key: (stdin)= 14c6b98b0c7c59012b1de89eee4a9dbc [root@mediator_host server_config]# openssl x509 -noout -modulus -in intermediate.crt | openssl md5 (stdin)= 14c6b98b0c7c59012b1de89eee4a9dbc
[root@mediator_host server_config]# openssl rsa -noout -modulus -in ca.key | openssl md5 Enter pass phrase for ca.key: (stdin)= 14c6b98b0c7c59012b1de89eee4a9dbc [root@mediator_host server_config]# openssl x509 -noout -modulus -in ca.crt | openssl md5 (stdin)= 14c6b98b0c7c59012b1de89eee4a9dbc
如果 -modulus 属性、表示专用密钥和证书对兼容且可相互配合使用。
验证是否已从特定CA证书创建服务器证书
您可以使用以下命令验证服务器证书是否是从特定CA证书创建的。
[root@mediator_host server_config]# openssl verify -CAfile root_ca.crt --untrusted intermediate.crt ontap_mediator_server.crt ontap_mediator_server.crt: OK [root@mediator_host server_config]#
[root@mediator_host server_config]# openssl verify -CAfile ca.crt ontap_mediator_server.crt ontap_mediator_server.crt: OK
如果正在使用联机证书状态协议(OCSP)验证,请使用命令 "OpenSSL验证"。


