本繁體中文版使用機器翻譯,譯文僅供參考,若與英文版本牴觸,應以英文版本為準。
使用 PowerShell 驗證ONTAP網路保險庫
 建議變更
建議變更


強大的網路保險庫應該能夠抵禦複雜的攻擊,即使攻擊者擁有以提升的權限存取環境的憑證。
一旦規則到位,嘗試(假設攻擊者能夠以某種方式進入)刪除保險庫端的快照將會失敗。透過施加必要的限制和保護系統,所有強化設定均適用相同的規定。
PowerShell 程式碼範例,用於按計劃驗證配置。
function analyze {
for($i = 0; $i -lt $DESTINATION_VOLUME_NAMES.Length; $i++) {
try {
# checking if volume is of type SnapLock Compliance
logMessage -message "Checking if SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) exists in vServer $DESTINATION_VSERVER"
$volume = Get-NcVol -Vserver $DESTINATION_VSERVER -Volume $DESTINATION_VOLUME_NAMES[$i] | Select-Object -Property Name, State, TotalSize, Aggregate, Vserver, Snaplock | Where-Object { $_.Snaplock.Type -eq "compliance" }
if($volume) {
$volume
logMessage -message "SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) exists in vServer $DESTINATION_VSERVER" -type "SUCCESS"
} else {
handleError -errorMessage "SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) does not exist in vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to create and configure the cyber vault SnapLock Compliance volume"
}
# checking SnapMirror relationship
logMessage -message "Checking if SnapMirror relationship exists between source volume $($SOURCE_VOLUME_NAMES[$i]) and destination SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i])"
$snapmirror = Get-NcSnapmirror | Select-Object SourceCluster, SourceLocation, DestinationCluster, DestinationLocation, Status, MirrorState | Where-Object { $_.SourceCluster -eq $SOURCE_ONTAP_CLUSTER_NAME -and $_.SourceLocation -eq "$($SOURCE_VSERVER):$($SOURCE_VOLUME_NAMES[$i])" -and $_.DestinationCluster -eq $DESTINATION_ONTAP_CLUSTER_NAME -and $_.DestinationLocation -eq "$($DESTINATION_VSERVER):$($DESTINATION_VOLUME_NAMES[$i])" -and $_.Status -eq "snapmirrored" }
if($snapmirror) {
$snapmirror
logMessage -message "SnapMirror relationship successfully configured and in healthy state" -type "SUCCESS"
} else {
handleError -errorMessage "SnapMirror relationship does not exist between the source volume $($SOURCE_VOLUME_NAMES[$i]) and destination SnapLock Compliance volume $($DESTINATION_VOLUME_NAMES[$i]) (or) SnapMirror status uninitialized/unhealthy. Recommendation: Run the script with SCRIPT_MODE `"configure`" to create and configure the cyber vault SnapLock Compliance volume and configure the SnapMirror relationship"
}
}
catch {
handleError -errorMessage $_.Exception.Message
}
}
try {
# checking NFS service is disabled
logMessage -message "Checking if NFS service is disabled on vServer $DESTINATION_VSERVER"
$nfsService = Get-NcNfsService
if($nfsService) {
handleError -errorMessage "NFS service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable NFS on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "NFS service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking CIFS/SMB server is disabled
logMessage -message "Checking if CIFS/SMB server is disabled on vServer $DESTINATION_VSERVER"
$cifsServer = Get-NcCifsServer
if($cifsServer) {
handleError -errorMessage "CIFS/SMB server running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable CIFS/SMB on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "CIFS/SMB server is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking iSCSI service is disabled
logMessage -message "Checking if iSCSI service is disabled on vServer $DESTINATION_VSERVER"
$iscsiService = Get-NcIscsiService
if($iscsiService) {
handleError -errorMessage "iSCSI service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable iSCSI on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "iSCSI service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking FCP service is disabled
logMessage -message "Checking if FCP service is disabled on vServer $DESTINATION_VSERVER"
$fcpService = Get-NcFcpService
if($fcpService) {
handleError -errorMessage "FCP service running on vServer $DESTINATION_VSERVER. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable FCP on vServer $DESTINATION_VSERVER"
} else {
logMessage -message "FCP service is disabled on vServer $DESTINATION_VSERVER" -type "SUCCESS"
}
# checking if all data lifs are disabled on vServer
logMessage -message "Finding all data lifs on vServer : $DESTINATION_VSERVER"
$dataLifs = Get-NcNetInterface -Vserver $DESTINATION_VSERVER | Where-Object { $_.Role -contains "data_core" }
$dataLifs | Select-Object -Property InterfaceName, OpStatus, DataProtocols, Vserver, Address
logMessage -message "Checking if all data lifs are disabled for vServer : $DESTINATION_VSERVER"
# Disable the filtered data LIFs
foreach ($lif in $dataLifs) {
$checkLif = Get-NcNetInterface -Vserver $DESTINATION_VSERVER -Name $lif.InterfaceName | Where-Object { $_.OpStatus -eq "down" }
if($checkLif) {
logMessage -message "Data lif $($lif.InterfaceName) disabled for vServer $DESTINATION_VSERVER" -type "SUCCESS"
} else {
handleError -errorMessage "Data lif $($lif.InterfaceName) is enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable Data lifs for vServer $DESTINATION_VSERVER"
}
}
logMessage -message "All data lifs are disabled for vServer : $DESTINATION_VSERVER" -type "SUCCESS"
# check if multi-admin verification is enabled
logMessage -message "Checking if multi-admin verification is enabled"
$maaConfig = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; security multi-admin-verify show"
if ($maaConfig.Value -match "Enabled" -and $maaConfig.Value -match "true") {
$maaConfig
logMessage -message "Multi-admin verification is configured and enabled" -type "SUCCESS"
} else {
handleError -errorMessage "Multi-admin verification is not configured or not enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to enable and configure Multi-admin verification"
}
# check if telnet is disabled
logMessage -message "Checking if telnet is disabled"
$telnetConfig = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; security protocol show -application telnet"
if ($telnetConfig.Value -match "enabled" -and $telnetConfig.Value -match "false") {
logMessage -message "Telnet is disabled" -type "SUCCESS"
} else {
handleError -errorMessage "Telnet is enabled. Recommendation: Run the script with SCRIPT_MODE `"configure`" to disable telnet"
}
# check if network https is restricted to allowed IP addresses
logMessage -message "Checking if HTTPS is restricted to allowed IP addresses $ALLOWED_IPS"
$networkServicePolicy = Invoke-NcSsh -Name $DESTINATION_ONTAP_CLUSTER_MGMT_IP -Credential $DESTINATION_ONTAP_CREDS -Command "set -privilege advanced; network interface service-policy show"
if ($networkServicePolicy.Value -match "management-https: $($ALLOWED_IPS)") {
logMessage -message "HTTPS is restricted to allowed IP addresses $ALLOWED_IPS" -type "SUCCESS"
} else {
handleError -errorMessage "HTTPS is not restricted to allowed IP addresses $ALLOWED_IPS. Recommendation: Run the script with SCRIPT_MODE `"configure`" to restrict allowed IP addresses for HTTPS management"
}
}
catch {
handleError -errorMessage $_.Exception.Message
}
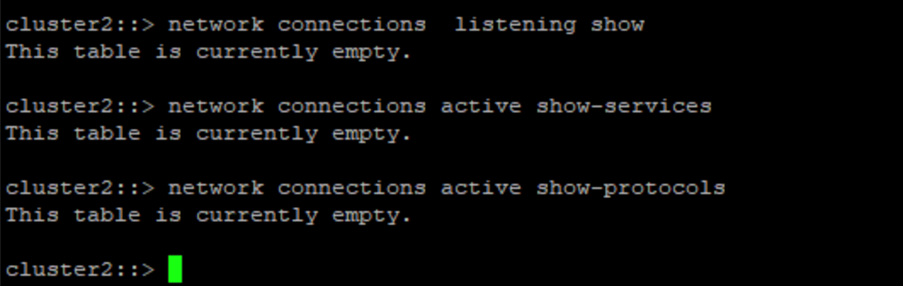
}此螢幕截圖顯示保險庫控制器上沒有連線。
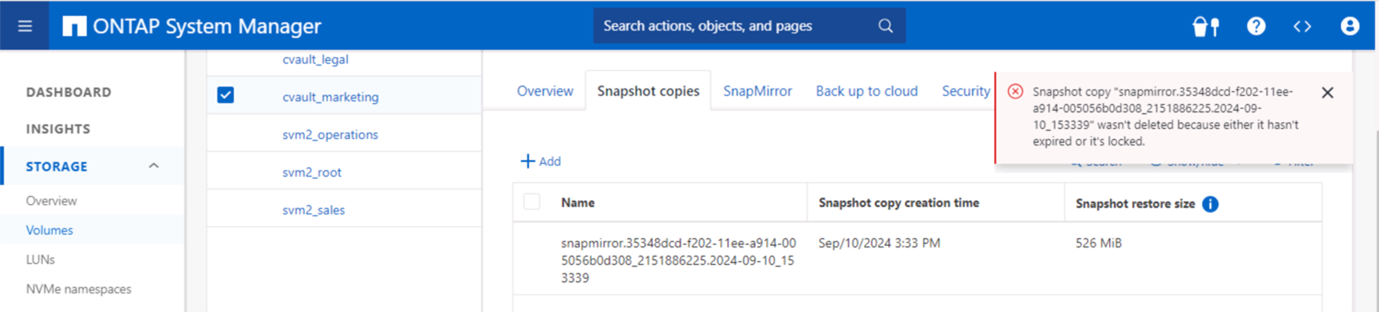
該螢幕截圖顯示快照無法被竄改。
若要驗證並確認氣隙功能,請依照下列步驟操作:
-
測試網路隔離功能以及在未傳輸資料時停止連線的能力。
-
驗證管理介面不能從允許的 IP 位址之外的任何實體存取。
-
驗證多管理員驗證是否到位以提供額外的批准層。
-
驗證透過 CLI 和 REST API 存取的能力
-
從源頭觸發保險庫的傳輸操作,並確保保險庫副本無法被修改。
-
嘗試刪除傳輸到保管庫的不可變快照副本。
-
嘗試透過竄改系統時鐘來修改保留期。


