Set up AWS networking for Cloud Volumes ONTAP
 Suggest changes
Suggest changes


The NetApp Console handles the set up of networking components for Cloud Volumes ONTAP, such as IP addresses, netmasks, and routes. You need to make sure that outbound internet access is available, that enough private IP addresses are available, that the right connections are in place, and more.
General requirements
Ensure that you have fulfilled the following requirements in AWS.
Outbound internet access for Cloud Volumes ONTAP nodes
Cloud Volumes ONTAP systems require outbound internet access for accessing external endpoints for various functions. Cloud Volumes ONTAP can't operate properly if these endpoints are blocked in environments with strict security requirements.
The Console agent contacts several endpoints for day-to-day operations. For information about the endpoints used, refer to View endpoints contacted from the Console agent and Prepare networking for using the Console.
Cloud Volumes ONTAP endpoints
Cloud Volumes ONTAP uses these endpoints to communicate with various services.
| Endpoints | Applicable for | Purpose | Deployment modes | Impact if endpoint is not available |
|---|---|---|---|---|
https://netapp-cloud-account.auth0.com |
Authentication |
Used for authentication in the Console. |
Standard and restricted modes. |
User authentication fails and the following services remain unavailable:
|
https://api.bluexp.netapp.com/tenancy |
Tenancy |
Used to retrieve Cloud Volumes ONTAP resource from the Console to authorize resources and users. |
Standard and restricted modes. |
Cloud Volumes ONTAP resources and the users are not authorized. |
https://mysupport.netapp.com/aods/asupmessage |
AutoSupport |
Used to send AutoSupport telemetry data to NetApp support. |
Standard and restricted modes. |
AutoSupport information remains undelivered. |
The exact commercial endpoint for AWS service (suffixed with |
|
Communication with AWS services. |
Standard and private modes. |
Cloud Volumes ONTAP cannot communicate with AWS service to perform specific operations in AWS. |
The exact government endpoint for AWS service depends on the AWS region that you are using. The endpoints are suffixed with |
|
Communication with AWS services. |
Restricted mode. |
Cloud Volumes ONTAP cannot communicate with AWS service to perform specific operations in AWS. |
Outbound internet access for the HA mediator
The HA mediator instance must have an outbound connection to the AWS EC2 service so it can assist with storage failover. To provide the connection, you can add a public IP address, specify a proxy server, or use a manual option.
The manual option can be a NAT gateway or an interface VPC endpoint from the target subnet to the AWS EC2 service. For details about VPC endpoints, refer to the AWS Documentation: Interface VPC Endpoints (AWS PrivateLink).
Network proxy configuration of NetApp Console agent
You can use the proxy servers configuration of the NetApp Console agent to enable outbound internet access from Cloud Volumes ONTAP. The Console supports two types of proxies:
-
Explicit proxy: The outbound traffic from Cloud Volumes ONTAP uses the HTTP address of the proxy server specified during the proxy configuration of the Console agent. The administrator might also have configured user credentials and root CA certificates for additional authentication. If a root CA certificate is available for the explicit proxy, make sure to obtain and upload the same certificate to your Cloud Volumes ONTAP system using the ONTAP CLI: security certificate install command.
-
Transparent proxy: The network is configured to automatically route outbound traffic from Cloud Volumes ONTAP through the proxy for the Console agent. When setting up a transparent proxy, the administrator needs to provide only a root CA certificate for connectivity from Cloud Volumes ONTAP, not the HTTP address of the proxy server. Make sure that you obtain and upload the same root CA certificate to your Cloud Volumes ONTAP system using the ONTAP CLI: security certificate install command.
For information about configuring proxy servers, refer to the Configure the Console agent to use a proxy server.
Private IP addresses
The Console automatically allocates the required number of private IP addresses to Cloud Volumes ONTAP. You need to ensure that your networking has enough private IP addresses available.
The number of LIFs that the Console allocates for Cloud Volumes ONTAP depends on whether you deploy a single node system or an HA pair. A LIF is an IP address associated with a physical port.
IP addresses for a single node system
The Console allocates 6 IP addresses to a single node system.
The following table provides details about the LIFs that are associated with each private IP address.
| LIF | Purpose |
|---|---|
Cluster management |
Administrative management of the entire cluster (HA pair). |
Node management |
Administrative management of a node. |
Intercluster |
Cross-cluster communication, backup, and replication. |
NAS data |
Client access over NAS protocols. |
iSCSI data |
Client access over the iSCSI protocol. Also used by the system for other important networking workflows. This LIF is required and should not be deleted. |
Storage VM management |
A storage VM management LIF is used with management tools like SnapCenter. |
IP addresses for HA pairs
HA pairs require more IP addresses than a single node system does. These IP addresses are spread across different ethernet interfaces, as shown in the following image:
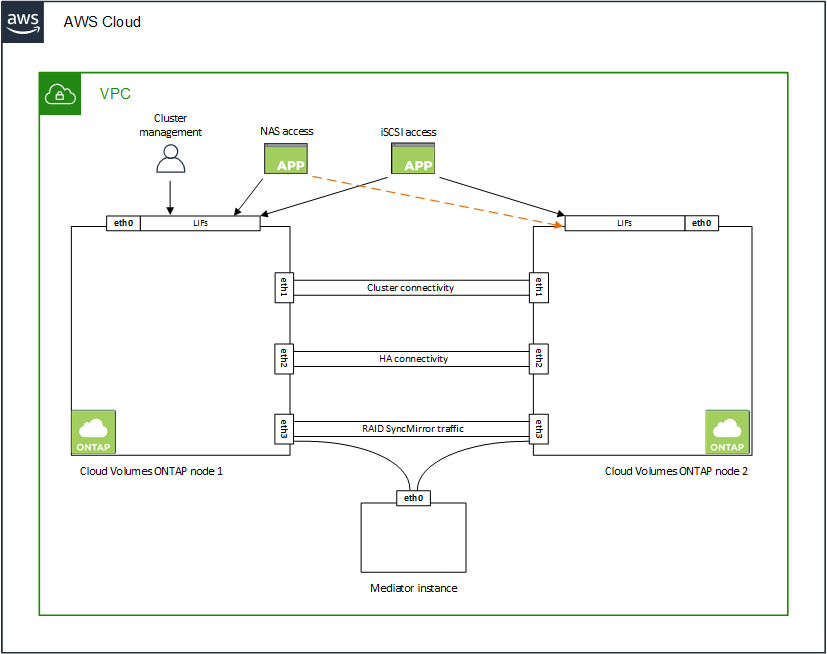
The number of private IP addresses required for an HA pair depends on which deployment model you choose. An HA pair deployed in a single AWS Availability Zone (AZ) requires 15 private IP addresses, while an HA pair deployed in multiple AZs requires 13 private IP addresses.
The following tables provide details about the LIFs that are associated with each private IP address.
| LIF | Interface | Node | Purpose |
|---|---|---|---|
Cluster management |
eth0 |
node 1 |
Administrative management of the entire cluster (HA pair). |
Node management |
eth0 |
node 1 and node 2 |
Administrative management of a node. |
Intercluster |
eth0 |
node 1 and node 2 |
Cross-cluster communication, backup, and replication. |
NAS data |
eth0 |
node 1 |
Client access over NAS protocols. |
iSCSI data |
eth0 |
node 1 and node 2 |
Client access over the iSCSI protocol. Also used by the system for other important networking workflows. These LIFs are required and should not be deleted. |
Cluster connectivity |
eth1 |
node 1 and node 2 |
Enables the nodes to communicate with each other and to move data within the cluster. |
HA connectivity |
eth2 |
node 1 and node 2 |
Communication between the two nodes in case of failover. |
RSM iSCSI traffic |
eth3 |
node 1 and node 2 |
RAID SyncMirror iSCSI traffic, as well as communication between the two Cloud Volumes ONTAP nodes and the mediator. |
Mediator |
eth0 |
Mediator |
A communication channel between the nodes and the mediator to assist in storage takeover and giveback processes. |
| LIF | Interface | Node | Purpose |
|---|---|---|---|
Node management |
eth0 |
node 1 and node 2 |
Administrative management of a node. |
Intercluster |
eth0 |
node 1 and node 2 |
Cross-cluster communication, backup, and replication. |
iSCSI data |
eth0 |
node 1 and node 2 |
Client access over the iSCSI protocol. |
Cluster connectivity |
eth1 |
node 1 and node 2 |
Enables the nodes to communicate with each other and to move data within the cluster. |
HA connectivity |
eth2 |
node 1 and node 2 |
Communication between the two nodes in case of failover. |
RSM iSCSI traffic |
eth3 |
node 1 and node 2 |
RAID SyncMirror iSCSI traffic, as well as communication between the two Cloud Volumes ONTAP nodes and the mediator. |
Mediator |
eth0 |
Mediator |
A communication channel between the nodes and the mediator to assist in storage takeover and giveback processes. |

|
When deployed in multiple Availability Zones, several LIFs are associated with floating IP addresses, which don't count against the AWS private IP limit. |
Security groups
You don't need to create security groups because the Console does that for you. If you need to use your own, refer to Security group rules.

|
Looking for information about the Console agent? View security group rules for the Console agent |
Connection for data tiering
If you want to use EBS as a performance tier and Amazon S3 as a capacity tier, you must ensure that Cloud Volumes ONTAP has a connection to S3. The best way to provide that connection is by creating a VPC Endpoint to the S3 service. For instructions, refer to the AWS Documentation: Creating a Gateway Endpoint.
When you create the VPC Endpoint, be sure to select the region, VPC, and route table that corresponds to the Cloud Volumes ONTAP instance. You must also modify the security group to add an outbound HTTPS rule that enables traffic to the S3 endpoint. Otherwise, Cloud Volumes ONTAP cannot connect to the S3 service.
If you experience any issues, refer to the AWS Support Knowledge Center: Why can’t I connect to an S3 bucket using a gateway VPC endpoint?
Connections to ONTAP systems
To replicate data between a Cloud Volumes ONTAP system in AWS and ONTAP systems in other networks, you must have a VPN connection between the AWS VPC and the other network—for example, your corporate network. For instructions, refer to the AWS Documentation: Setting Up an AWS VPN Connection.
DNS and Active Directory for CIFS
If you want to provision CIFS storage, you must set up DNS and Active Directory in AWS or extend your on-premises setup to AWS.
The DNS server must provide name resolution services for the Active Directory environment. You can configure DHCP option sets to use the default EC2 DNS server, which must not be the DNS server used by the Active Directory environment.
For instructions, refer to the AWS Documentation: Active Directory Domain Services on the AWS Cloud: Quick Start Reference Deployment.
VPC sharing
Starting with the 9.11.1 release, Cloud Volumes ONTAP HA pairs are supported in AWS with VPC sharing. VPC sharing enables your organization to share subnets with other AWS accounts. To use this configuration, you must set up your AWS environment and then deploy the HA pair using the API.
Requirements for HA pairs in multiple AZs
Additional AWS networking requirements apply to Cloud Volumes ONTAP HA configurations that use multiple Availability Zones (AZs). You should review these requirements before you launch an HA pair because you must enter the networking details in the Console when you add a Cloud Volumes ONTAP system.
To understand how HA pairs work, refer to High-availability pairs.
- Availability Zones
-
This HA deployment model uses multiple AZs to ensure high availability of your data. You should use a dedicated AZ for each Cloud Volumes ONTAP instance and the mediator instance, which provides a communication channel between the HA pair.
A subnet should be available in each Availability Zone.
- Floating IP addresses for NAS data and cluster/SVM management
-
HA configurations in multiple AZs use floating IP addresses that migrate between nodes if failures occur. They are not natively accessible from outside the VPC, unless you set up an AWS transit gateway.
One floating IP address is for cluster management, one is for NFS/CIFS data on node 1, and one is for NFS/CIFS data on node 2. A fourth floating IP address for SVM management is optional.
A floating IP address is required for the SVM management LIF if you use SnapDrive for Windows or SnapCenter with the HA pair. You need to enter the floating IP addresses when you add a Cloud Volumes ONTAP HA system. The Console allocates the IP addresses to the HA pair when it launches the system.
The floating IP addresses must be outside of the CIDR blocks for all VPCs in the AWS region in which you deploy the HA configuration. Think of the floating IP addresses as a logical subnet that's outside of the VPCs in your region.
The following example shows the relationship between floating IP addresses and the VPCs in an AWS region. While the floating IP addresses are outside the CIDR blocks for all VPCs, they're routable to subnets through route tables.
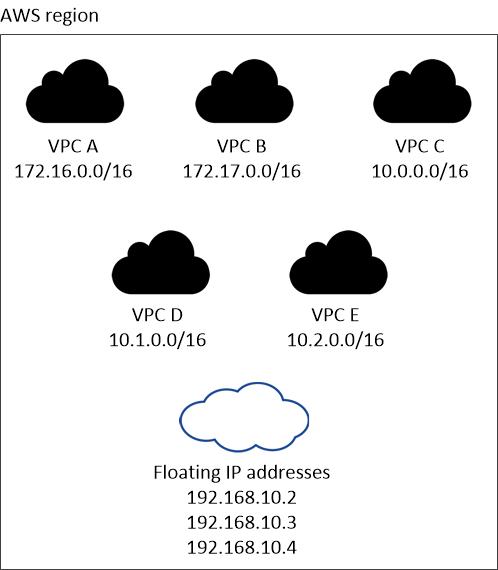
The Console automatically creates static IP addresses for iSCSI access and for NAS access from clients outside the VPC. You don't need to meet any requirements for these types of IP addresses. - Transit gateway to enable floating IP access from outside the VPC
-
If needed, set up an AWS transit gateway to enable access to an HA pair's floating IP addresses from outside the VPC where the HA pair resides.
- Route tables
-
After you specify the floating IP addresses, you are then prompted to select the route tables that should include routes to the floating IP addresses. This enables client access to the HA pair.
If you have just one route table for the subnets in your VPC (the main route table), then the Console automatically adds the floating IP addresses to that route table. If you have more than one route table, it's very important to select the correct route tables when launching the HA pair. Otherwise, some clients might not have access to Cloud Volumes ONTAP.
For example, you might have two subnets that are associated with different route tables. If you select route table A, but not route table B, then clients in the subnet associated with route table A can access the HA pair, but clients in the subnet associated with route table B can't.
For more information about route tables, refer to the AWS Documentation: Route Tables.
- Connection to NetApp management tools
-
To use NetApp management tools with HA configurations that are in multiple AZs, you have two connection options:
-
Deploy the NetApp management tools in a different VPC and set up an AWS transit gateway. The gateway enables access to the floating IP address for the cluster management interface from outside the VPC.
-
Deploy the NetApp management tools in the same VPC with a similar routing configuration as NAS clients.
-
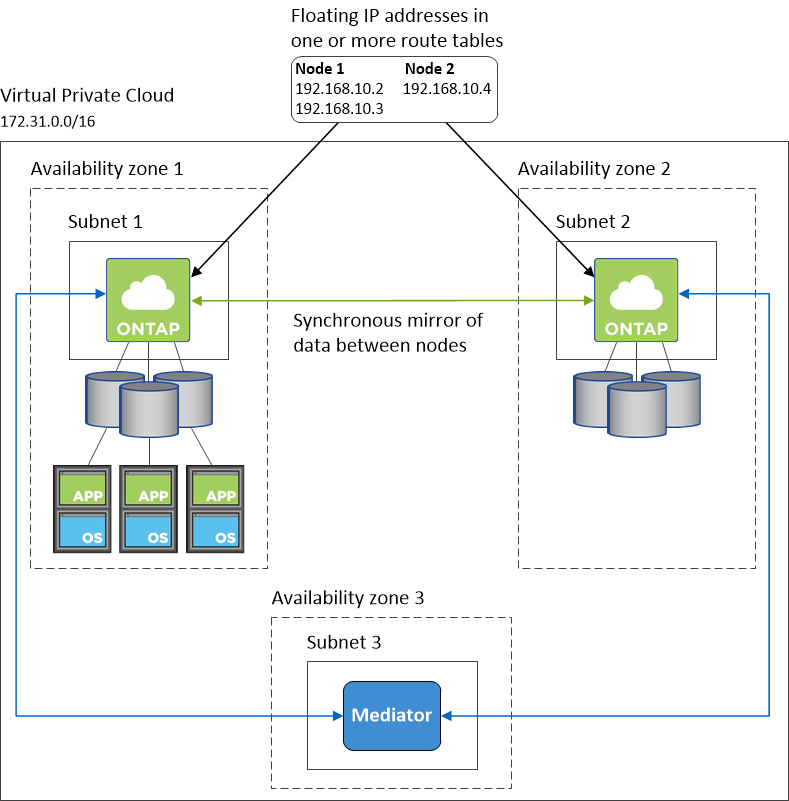
Example HA configuration
The following image illustrates the networking components specific to an HA pair in multiple AZs: three Availability Zones, three subnets, floating IP addresses, and a route table.
Requirements for the Console agent
If you haven't created a Console agent yet, you should review networking requirements.



