Learn about AWS credentials and permissions in NetApp Console
 Suggest changes
Suggest changes


You manage AWS credentials and marketplace subscriptions directly from NetApp Console to ensure secure deployment of Cloud Volumes ONTAP and other data services by providing appropriate IAM credentials during Console agent deployment and associating them with AWS Marketplace subscriptions for billing.
Initial AWS credentials
When you deploy an Console agent from the Console, you need to provide the ARN of an IAM role or access keys for an IAM user. The authentication method must have permissions to deploy the Console agent in AWS. The required permissions are listed in the Agent deployment policy for AWS.
When the Console launches the Console agent in AWS, it creates an IAM role and a profile for the agent. It also attaches a policy that provides the Console agent with permissions to manage resources and processes within that AWS account. Review how the Agent uses the permissions.
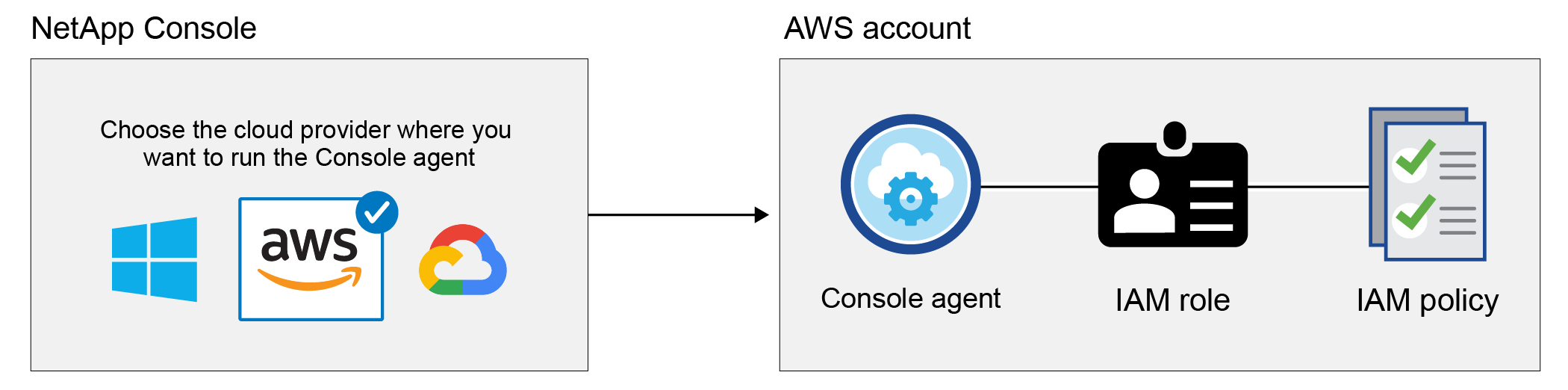
If you add a new Cloud Volumes ONTAP system, the Console selects these AWS credentials by default:
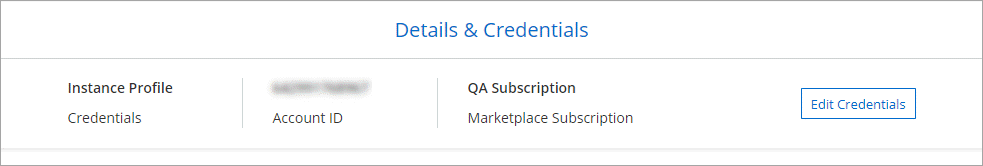
Deploy all of your Cloud Volumes ONTAP systems using the initial AWS credentials, or you can add additional credentials.
Additional AWS credentials
You might add additional AWS credentials to the Console in the following cases:
-
To use your existing Console agent with an additional AWS account
-
To create a new agent in a specific AWS account
-
To create and manage FSx for ONTAP file systems
Review the sections below for more details.
Add AWS credentials to use a Console agent with another AWS account
To use the Console with additional AWS accounts, provide AWS keys or the ARN of a role in a trusted account. The following image shows two additional accounts, one providing permissions through an IAM role in a trusted account and another through the AWS keys of an IAM user:
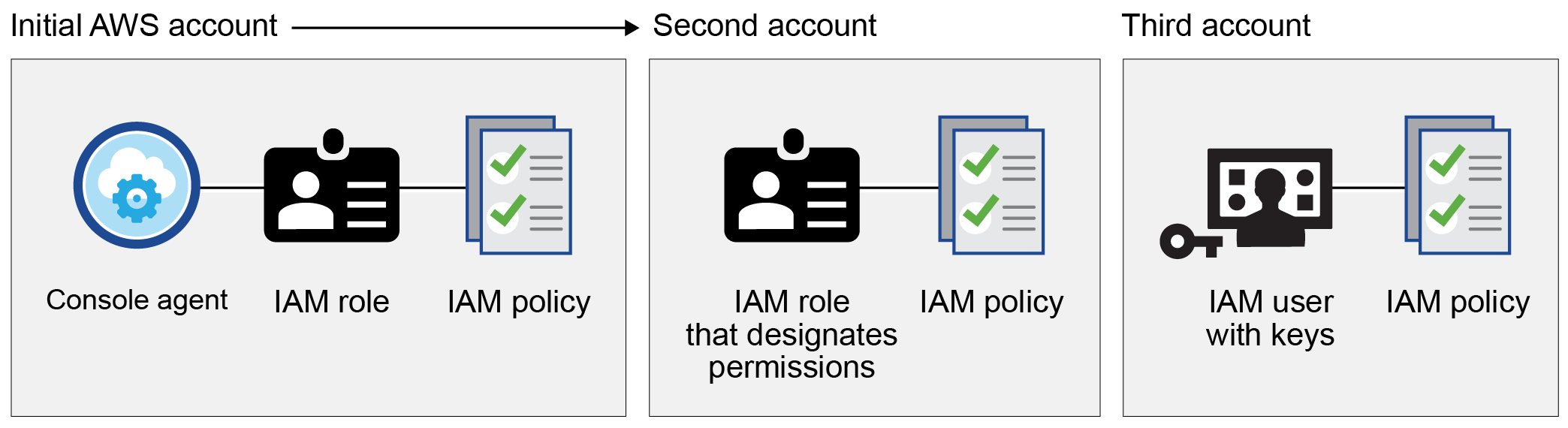
You add account credentials to the Console by specifying the Amazon Resource Name (ARN) of IAM role or the AWS keys for the IAM user.
For example, you can switch between credentials when creating a new Cloud Volumes ONTAP system:
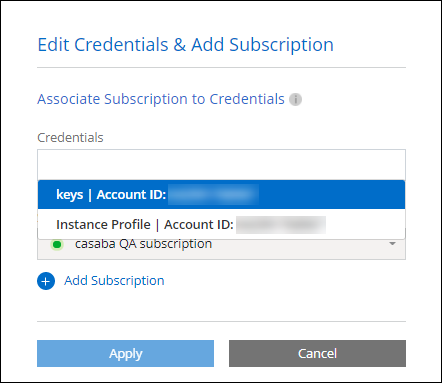
Add AWS credentials to create a Console agent
Adding AWS credentials provides permissions to create a Console agent.
Add AWS credentials for FSx for ONTAP
Add AWS credentials to the Console to provide the necessary permissions to create and manage an FSx for ONTAP system.
Credentials and marketplace subscriptions
You must associate the credentials that you add to a Console agent with an AWS Marketplace subscription to pay for Cloud Volumes ONTAP at an hourly rate (PAYGO) and other NetApp data services or through an annual contract.
Learn how to associate an AWS subscription.
Note the following about AWS credentials and marketplace subscriptions:
-
You can associate only one AWS Marketplace subscription with a set of AWS credentials
-
You can replace an existing marketplace subscription with a new subscription
FAQ
The following questions are related to credentials and subscriptions.
How can I securely rotate my AWS credentials?
As described in the sections above, the Console enables you to provide AWS credentials in a few ways: an IAM role associated with the Console agent, by assuming an IAM role in a trusted account, or by providing AWS access keys.
With the first two options, the Console uses the AWS Security Token Service to obtain temporary credentials that rotate constantly. This process is the best practice—it's automatic and secure.
If you provide the Console with AWS access keys, you should rotate the keys by updating them in the Console at a regular interval. This is a completely manual process.
Can I change the AWS Marketplace subscription for Cloud Volumes ONTAP systems?
Yes, you can. When you change the AWS Marketplace subscription that's associated with a set of credentials, all existing and new Cloud Volumes ONTAP systems are charged against the new subscription.
Can I add multiple AWS credentials, each with different marketplace subscriptions?
All AWS credentials that belong to the same AWS account will be associated with the same AWS Marketplace subscription.
If you have multiple AWS credentials that belong to different AWS accounts, then those credentials can be associated with the same AWS Marketplace subscription or with different subscriptions.
Can I move existing Cloud Volumes ONTAP systems to a different AWS account?
No, it's not possible to move the AWS resources associated with your Cloud Volumes ONTAP system to a different AWS account.
How do credentials work for marketplace deployments and on-premises deployments?
The sections above describe the recommended deployment method for the Console agent, which is from the Console. You can also deploy an agent in AWS from the AWS Marketplace and you can manually install the Console agent software on your own Linux host or in your VCenter.
If you use the Marketplace, permissions are provided in the same way. You just need to manually create and set up the IAM role, and then provide permissions for any additional accounts.
For on-premises deployments, you can't set up an IAM role for the Console, but you can provide permissions using AWS access keys.
To learn how to set up permissions, refer to the following pages:


