Integration with ONTAP Access Denied
 Suggest changes
Suggest changes


The ONTAP Access Denied feature uses workload analysis in NAS environments (NFS and SMB) to proactively detect and warn about failed file operations (i.e., a user trying to perform an operation for which they do not have permission). These failed file operation notifications—especially in cases of security-related failures—will further help in blocking insider attacks at early stages.
Data Infrastructure Insights Workload Security integrates with ONTAP to receive Access Denied events and provide an additional analytic and automatic response layer.
Prerequisites
-
Minimum ONTAP version: 9.13.0.
-
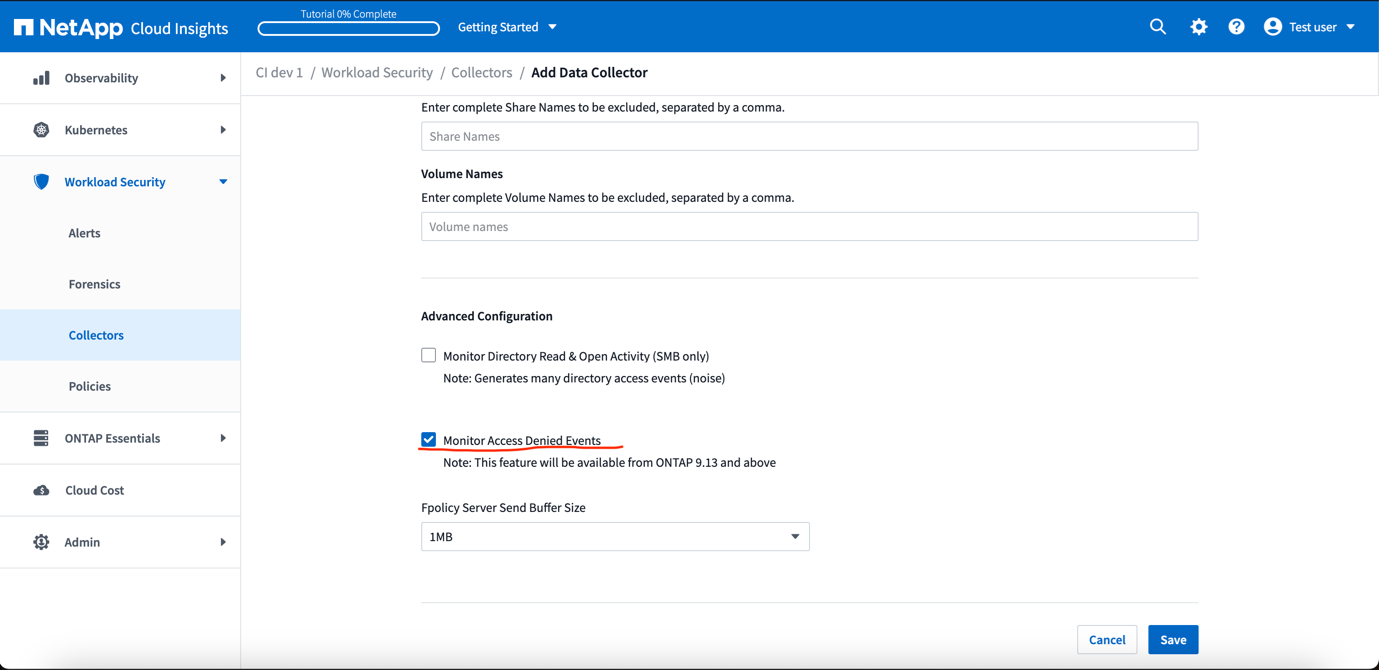
A Workload Security administrator must enable the Access Denied feature while adding a new collector or editing existing collector, by selecting the Monitor Access Denied Events checkbox under Advanced Configuration.
User permissions required
If the Data Collector is added using cluster administration credentials, no new permissions are needed.
If the Collector is added using a custom user (for example, csuser) with permissions given to the user, follow the steps below to give Workload Security the necessary permission to register for Access Denied events with ONTAP.
For csuser with cluster credentials, execute the following commands from the ONTAP command line. Note that this permission may already exist.
security login role create -role csrole -cmddirname "vserver fpolicy" -access all
For csuser with SVM credentials, execute the following commands from the ONTAP command line. Note that this permission may already exist.
security login role create -vserver <vservername> -role csrole -cmddirname "vserver fpolicy" -access all
Read more about configuring other ONTAP permissions.
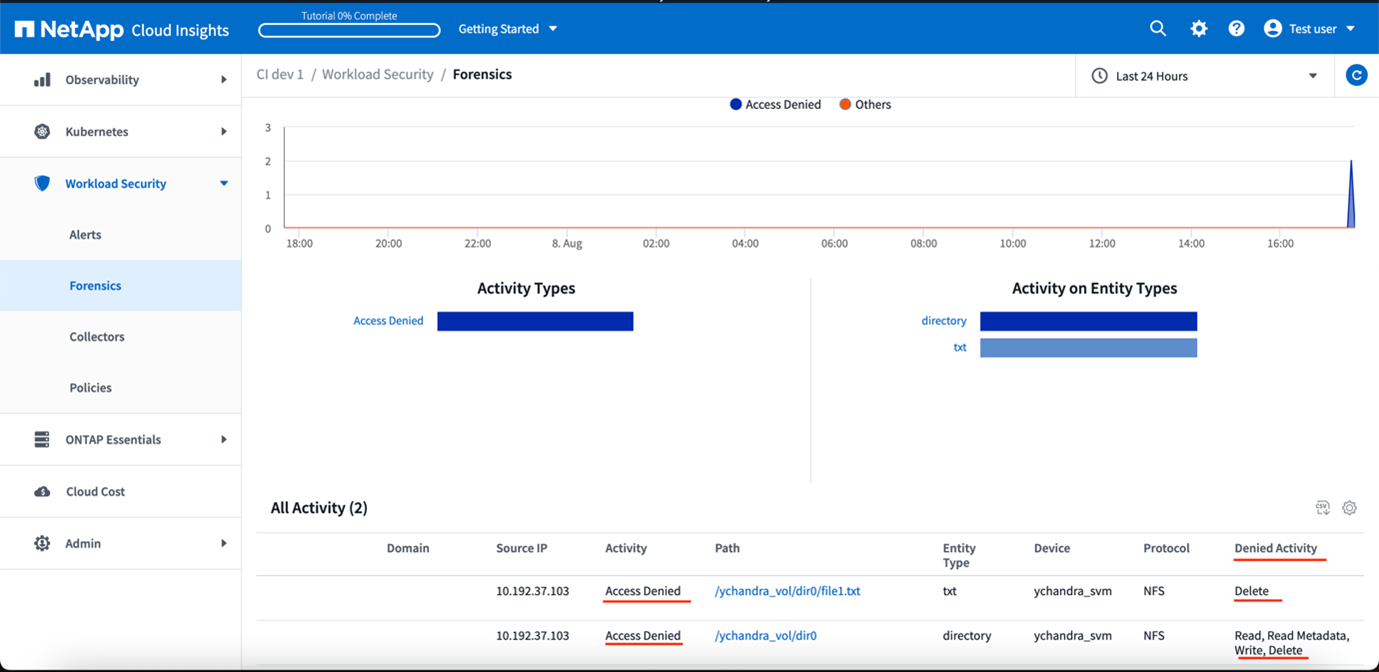
Access Denied events
Once events have been acquired from the ONTAP system, the Workload Security Forensics page will show Access Denied events. In addition to the information displayed, you can view the missing user permissions for a particular operation by adding the Desired Activity column to the table from the gear icon.