Learn about user activity detection in NetApp Ransomware Resilience
 Suggest changes
Suggest changes


With user activity detection, NetApp Ransomware Resilience enables you to address ransomware events at the user-level, stopping events such as data breaches and large-scale deletion.
NetApp Ransomware Resilience delivers an AI-driven data breach detection by monitoring for suspicious user activity. Sharp increases in read activity and read activity access patterns are used to determine malicious intent. Once detected, Ransomware Resilience automatically generates alerts in the NetApp Console, via e-mail, and in any configured security ecosystem (for example, SIEM).
With suspicious user behavior detection and alerting, Ransomware Resilience alerts you to data breach and destruction attempts and patterns that seem suspicious. In each alert, Ransomware Resilience identifies a user whom you can block.
Ransomware Resilience detects suspicious user activity by analyzing user activity events generated by FPolicy in ONTAP. To collect user activity data, you need to deploy one or more user activity agents. The user activity agent is a Linux server or VM with connectivity to devices on your tenant.

|
User activity detection is currently not supported for SAN workloads. You can use user activity detection with NAS workloads in Amazon FSxN for ONTAP, Cloud Volumes ONTAP, and ONTAP. |
Suspicious user activity forensics
Ransomware Resilience offers forensics for user behaviors: lists and graphs that show when suspicious activity occurred and when notifications were sent out. These detail the frequency of suspicious activity on files, directories, volumes, and workloads over time to help chart the events. You can also observe the appearance of new file extensions.
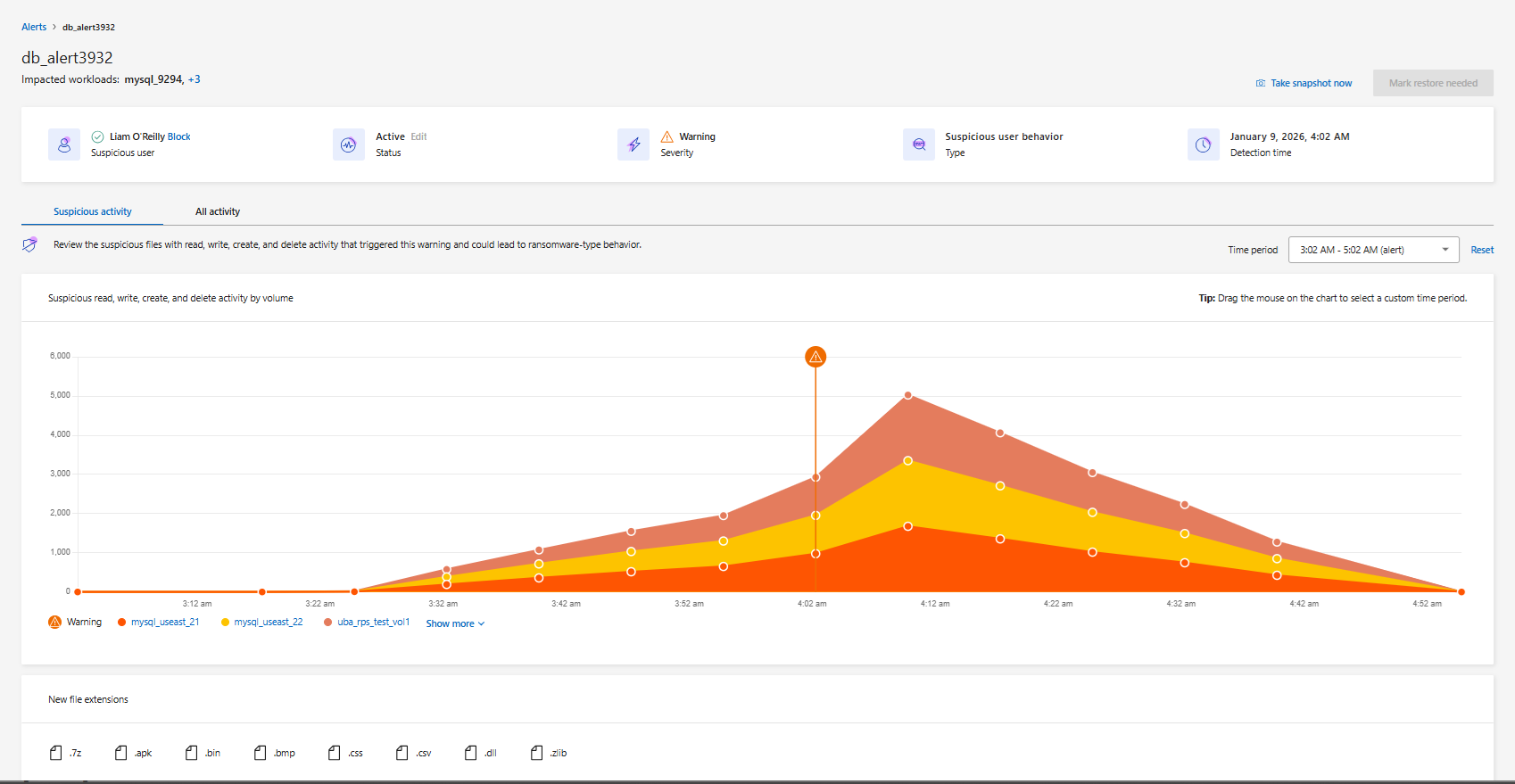 .
.
You can compare suspicious activity with a view of all activity. In the all activity view, you can observe read, write, rename, move, create, and delete events in addition to access change and access denied events.
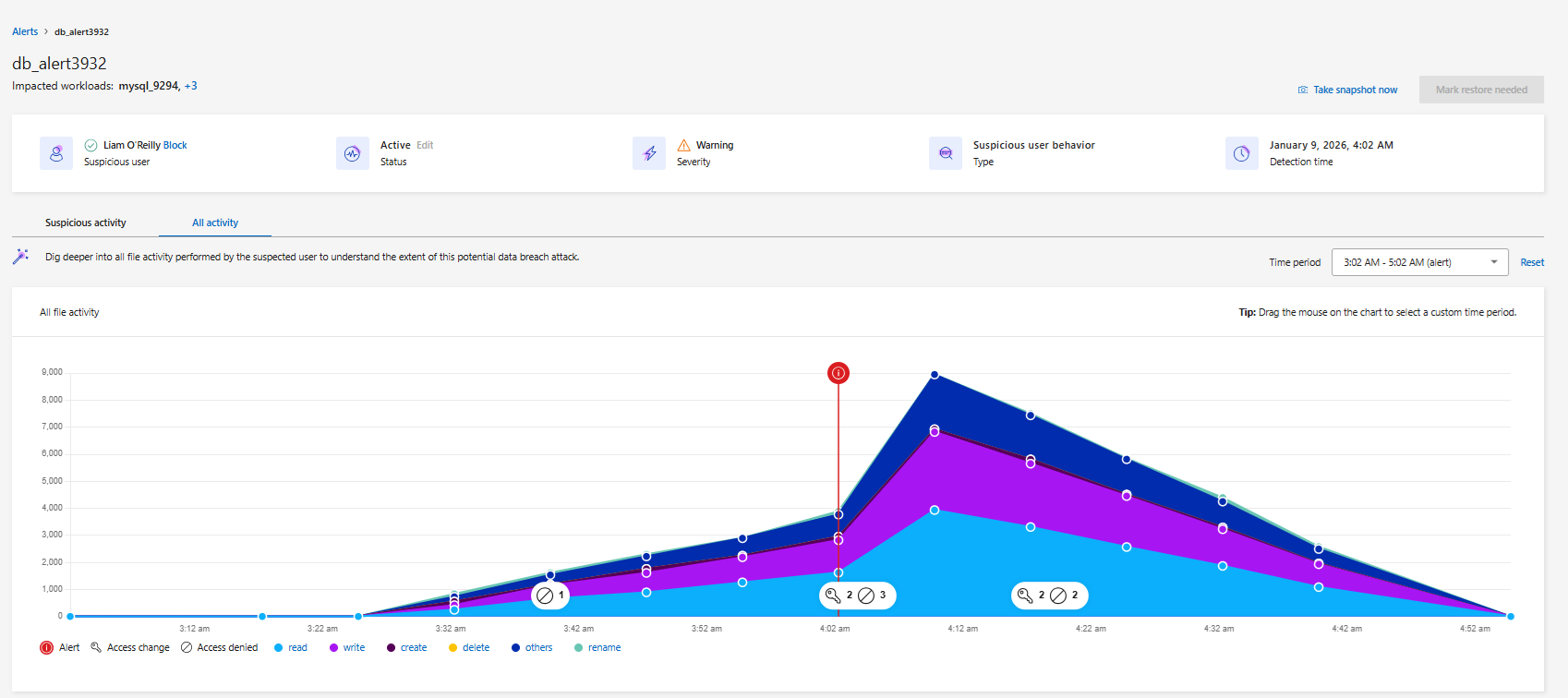 .
.
Components
There are three key components in Ransomware Resilience suspicious user behavior activity detection.
-
The user activity agent is an executable environment for data collectors. You must configure the user activity agent.
-
The data collector share user activity events with Ransomware Resilience. The data collector is created automatically when you enable a ransomware protection strategy with suspicious user activity detection.
-
The user directory connector enables mapping between usernames and user IDs, creating greater clarity when responding to suspicious user behavior. You must configure the user directory connector.
Ransomware Resilience and Data Infrastructure Insights
Ransomware Resilience's suspicious user behavior detection is an integration with Data Infrastructure Insights (DII) Workload Security and uses DII endpoints. You don't need any DII configuration to enable user behavior detection in Ransomware Resilience. To enable user behavior detection, create the required agent and collectors and enable the appropriate ransomware protection strategy.
If you're already using NetApp Data Infrastructure Insights (DII) Workload Security, it's recommended you use the same Workload Security agents for Ransomware Resilience. You don't need to deploy separate Workload Security agents for Ransomware Resilience, however, using the same Workload Security agents requires a pairing relationship between the Ransomware Resilience Console organization and DII Storage Workload Security tenant. Contact your account representative to enable this pairing.


