Overview of ONTAP cyber vault with PowerShell
 Suggest changes
Suggest changes


In today's digital landscape, safeguarding an organization's critical data assets is not just a best practice - it is a business imperative. Cyber threats are evolving at an unprecedented pace, and traditional data protection measures are no longer sufficient to keep sensitive information secure. That is where a cyber vault comes in. NetApp's cutting-edge ONTAP based solution combines advanced air-gapping techniques with robust data protection measures to create an impenetrable barrier against cyber threats. By isolating the most valuable data with secure hardening technology, a cyber vault minimizes the attack surface so that the most critical data remains confidential, intact, and readily available when needed.
A cyber vault is a secure storage facility that consists of multiple layers of protection, such as firewalls, networking, and storage. These components safeguard vital recovery data necessary for crucial business operations. The cyber vault's components regularly synchronize with the essential production data based on the vault policy, but otherwise remain inaccessible. This isolated and disconnected setup ensures that in the event of a cyber-attack compromising the production environment, a reliable and final recovery can easily be carried out from the cyber vault.
NetApp enables easy creation of an air-gap for cyber vault by configuring the network, disabling LIFs, updating firewall rules, and isolating the system from external networks and the internet. This robust approach effectively disconnects the system from external networks and the internet, providing unparalleled protection against remote cyber-attacks and unauthorized access attempts, making the system immune to network-based threats and intrusion.
Combining this with SnapLock Compliance protection, data cannot be modified or deleted, not even by ONTAP administrators or NetApp Support. SnapLock is regularly audited against SEC and FINRA regulations, ensuring that data resiliency meets these stringent WORM and data retention regulations of the banking industry. NetApp is the only enterprise storage validated by NSA CSfC to store top-secret data.
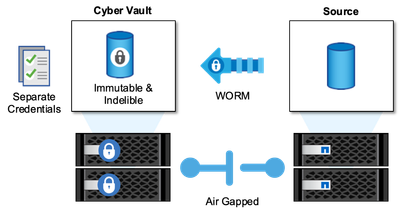
This document describes the automated configuration of NetApp's cyber vault for on-premises ONTAP storage to another designated ONTAP storage with immutable snapshots adding an extra layer of protection from increasing cyber-attacks for rapid recovery. As part of this architecture, the entire configuration is applied as per ONTAP best practices. The last section has instructions for performing a recovery in case of an attack.

|
The same solution is applicable to create the designated cyber vault in AWS using FSx ONTAP. |
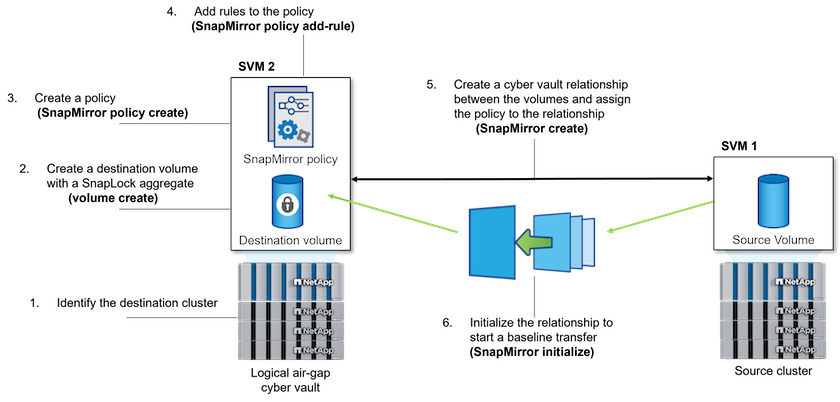
High level steps to create a ONTAP cyber vault
-
Create peering relationship
-
Production site using ONTAP storage is peered with designated cyber vault ONTAP storage
-
-
Create SnapLock Compliance volume
-
Setup SnapMirror relationship and rule to set label
-
SnapMirror relationship and appropriate schedules are configured
-
-
Set retentions prior to initiating the SnapMirror (vault) transfer
-
Retention lock is applied on the copied data, which further prevents the data from any insider or data failure. Using this, the data cannot be deleted before the retention period expires
-
Organizations can keep this data for few weeks/months depending upon their requirements
-
-
Initialize the SnapMirror relationship based on labels
-
Initial seeding and incremental forever transfer happens based on the SnapMirror schedule
-
Data is protected (immutable and indelible) with SnapLock compliance, and that the data is available for recovery
-
-
Implement strict data transfer controls
-
Cyber vault is unlocked for a limited period with data from the production site and is synced with data in the vault. Once the transfer is complete, the connection is disconnected, closed, and locked again
-
-
Quick recovery
-
If primary is affected in the production site, the data from the cyber vault is securely recovered to the original production or to another chosen environment
-
Solution components
NetApp ONTAP running 9.15.1 on source and destination clusters.
ONTAP One: NetApp ONTAP's all-in-one license.
Capabilities used from ONTAP One license:
-
SnapLock Compliance
-
SnapMirror
-
Multi-admin verification
-
All hardening capabilities exposed by ONTAP
-
Separate RBAC credentials for cyber vault

|
All ONTAP unified physical arrays can be used for a cyber vault, however AFF C-series capacity based flash systems and FAS hybrid flash systems are the most cost-effective ideal platforms for this purpose. Please consult the ONTAP cyber vault sizing for sizing guidance. |


