Learn about NetApp Ransomware Resilience
 Suggest changes
Suggest changes


Ransomware attacks can block access to your data and attackers can ask for ransom in exchange for the release of data or decryption. According to the IDC, it is not uncommon for victims of ransomware to experience multiple ransomware attacks. The attack can disrupt access to your data for anywhere from one day to several weeks.
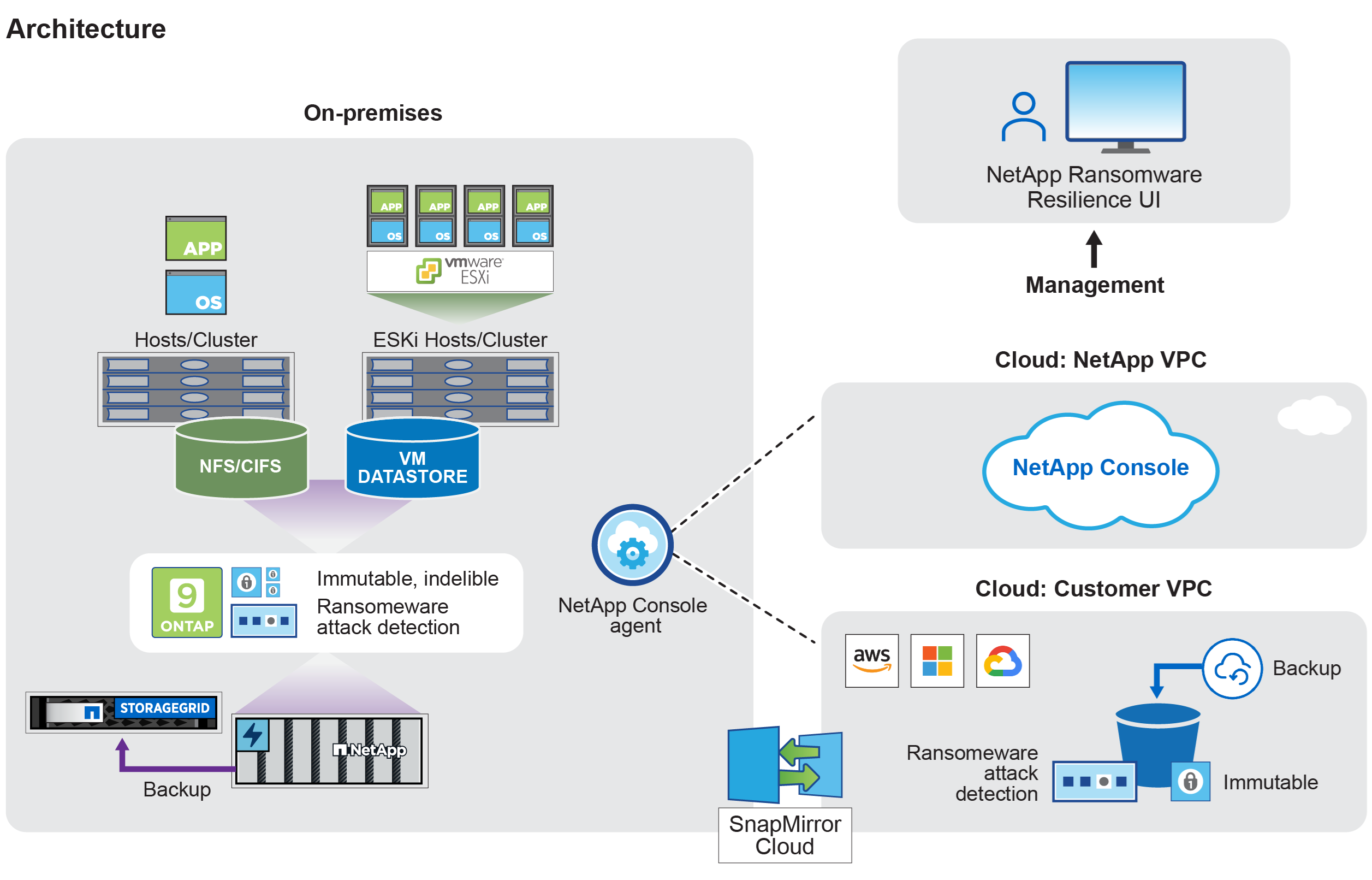
NetApp Ransomware Resilience protects your data from ransomware attacks. In Ransomware Resilience, protection is available for application-based workloads of Oracle, VM datastores, and file shares for NAS storage (NFS and CIFS protocols) and SAN storage (FC, iSCSI, and NVMe protocols). Ransomware Resilience is supported in on-premises storage as well as Cloud Volumes ONTAP for Amazon Web Services, Cloud Volumes ONTAP for Google Cloud, Cloud Volumes ONTAP for Microsoft Azure, Azure NetApp Files, and Amazon FSx for NetApp ONTAP across the NetApp Console. You can back up data to Amazon Web Services, Google Cloud, Microsoft Azure, and NetApp StorageGRID.
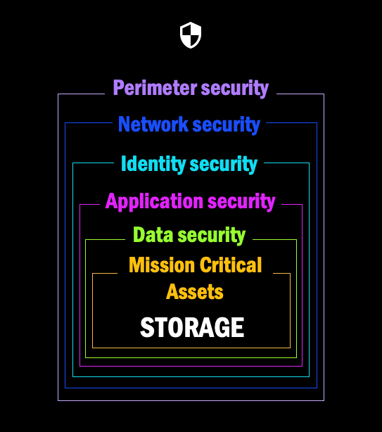
Ransomware Resilience at the data layer
Your security posture typically encompasses multiple layers of defense to protect against a range of cyber threats.
-
Outermost layer: This is your first line of defense using firewalls, intrusion detection systems, and virtual private networks to safeguard network boundaries.
-
Network security: This layer builds upon the foundation with network segmentation, traffic monitoring, and encryption.
-
Identity security: Uses authentication methods, access controls, and identity management to ensure only authorized users can access sensitive resources.
-
Application security: Protects software applications using secure coding practices, security testing, and runtime application self-protection.
-
Data security: Safeguards your data with data protection, backups, and recovery strategies. Ransomware Resilience operates on this layer.
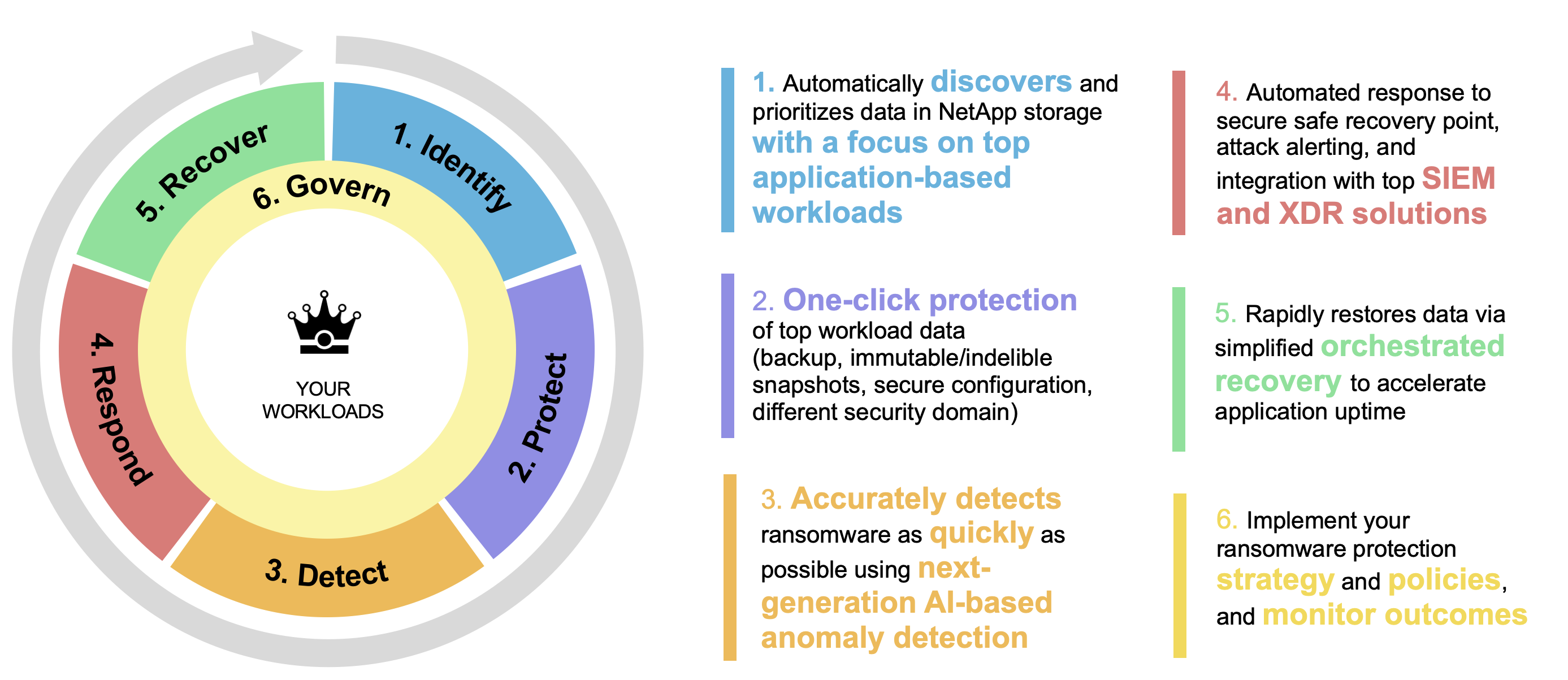
What you can do with Ransomware Resilience
Ransomware Resilience provides full use of several NetApp technologies so that your storage administrator, data security administrator, or security operations engineer can accomplish the following goals:
-
Identify application-based, file share, or VMware-managed workloads in NetApp on-premises NAS and SAN systems across the NetApp Console, projects, and Console agents. After discovering workloads, Ransomware Resilience identifies opportunities to improve ransomware resiliency.
-
Protect your workloads by enabling backups, snapshot copies, and ransomware protection strategies on your data.
-
Detect anomalies that might be ransomware attacks.[1]
-
Respond to potential ransomware attacks by automatically initiating a point-in-time snapshot that is locked so that the copy can't be deleted accidentally or maliciously. Your backup data will stay immutable and protected end-to-end from ransomware attacks at the source and in the destination.
-
Recover your workloads that help accelerate workload uptime by orchestrating several NetApp technologies. You can choose to recover specific volumes. Ransomware Resilience provides recommendations on the best options.
-
Govern: Implement your ransomware protection strategy and monitor the outcomes.
Benefits of using Ransomware Resilience
Ransomware Resilience offers the following benefits:
-
Discovers workloads and their existing snapshot and backup schedules, and ranks their relative importance.
-
Evaluates your ransomware protection posture and displays it in an easy-to-understand dashboard while providing recommendations to improve protection.
-
Applies AI/ML-driven data protection recommendations with one-click access.
-
Protects data in application-based workloads such as Oracle, VMware datastores, and file shares.
-
Detects ransomware attacks on data in real time on primary storage using AI technology.
-
Initiates automated actions in response to detected potential attacks by creating snapshot copies and initiating alerts about abnormal activity.
-
Applies curated recovery to meet RPO policies. Ransomware Resilience orchestrates recovery from ransomware incidents by NetApp Backup and Recovery.
-
Uses role-based access control (RBAC) to govern access to features and operations.
Cost
New deployments of Ransomware Resilience offer a 30-day free trial. NetApp doesn't charge you for using the trial version of Ransomware Resilience.
If you have both Backup and Recovery and Ransomware Resilience, any common data protected by both products is billed by Ransomware Resilience only.
When a workload is classified as protected, it counts against purchased capacity or the PayGo subscription. Ransomware Resilience classifies a workload as protected when a detection policy is enabled with at least one snapshopt or backup policy. Workloads discovered with a detection policy but without backup or snapshot policies are classified as at risk. At risk workloads do not count against purchased capacity.
Protected workloads count against purchased capacity or the subscription after the free trial period ends. Ransomware Resilience is charged on a per GB basis for the data associated with protected workloads before efficiencies.
Licensing
With Ransomware Resilience, you can use different licensing plans including a free trial, a pay-as-you-go subscription, or bring your own license.
Ransomware Resilience requires a NetApp ONTAP One license.
The Ransomware Resilience license does not include additional NetApp products. Ransomware Resilience can use Backup and Recovery even if you don't have a license for it.
To detect anomalous user behavior, Ransomware Resilience uses NetApp Autonomous Ransomware Protection, a machine learning (ML) model within ONTAP that detects malicious file activity. This model is included in the Ransomware Resilience license.
For details, see Set up licensing.
NetApp Console
Ransomware Resilience is accessible through the NetApp Console.
The NetApp Console provides centralized management of NetApp storage and data services across on-premises and cloud environments at enterprise grade. The Console is required to access and use NetApp data services. As a management interface, it enables you to manage many storage resources from one interface. Console administrators can control access to storage and services for all systems within the enterprise.
You don't need a license or subscription to start using NetApp Console and you only incur charges when you deploy Console agents in your cloud to ensure connectivity to your storage systems or NetApp data services. However, some NetApp data services accessible from the Console are licensed or subscription-based.
Learn more about the NetApp Console.
How Ransomware Resilience works
Ransomware Resilience uses NetApp Backup and Recovery to discover and set snapshot and backup policies for file share workloads.
| Feature | Description |
|---|---|
IDENTIFY |
|
PROTECT |
|
DETECT |
|
RESPOND |
|
RECOVER |
|
GOVERN |
|
Supported backup targets, systems, and workload data sources
Ransomware Resilience supports the following backup targets, systems, and data sources:
Supported backup targets
-
Amazon Web Services (AWS) S3
-
Google Cloud Platform
-
Microsoft Azure Blob
-
NetApp StorageGRID
Supported systems
| Environment | Protocol | Supported versions |
|---|---|---|
Amazon FSx for NetApp ONTAP* |
CIFS, NFS, and SAN |
N/A |
Azure NetApp Files |
CIFS & NFS |
N/A |
Cloud Volumes ONTAP for AWS |
CIFS & NFS |
9.11.1 and later |
SAN (iSCSI & NVMe) |
9.17.1 and later |
|
Cloud Volumes ONTAP for Google Cloud Platform |
CIFS & NFS |
9.11.1 and later |
SAN (iSCSI & NVMe) |
9.17.1 and later |
|
Cloud Volumes ONTAP for Microsoft Azure |
CIFS & NFS |
9.12.1 and later |
SAN (iSCSI & NVMe) |
9.17.1 and later |
|
ONTAP (on-premises) |
CIFS & NFS |
9.11.1 and later |
SAN (FC, iSCSI, & NVMe) |
9.17.1 and later |
* Amazon FSx for NetApp ONTAP uses Autonomous Ransomware Protection (ARP) and not ARP/AI. For more information about the difference, see ARP/AI.

|
Using ARP/AI in ONTAP requires ONTAP 9.16 or greater. ONTAP doesn't provide ransomware protection support for FabricPool FlexCache, FlexGroup volumes, consistency groups mount point volumes, mount path volumes, offline volumes, and Data protection (DP) volumes. Ensure you review supported and unsupported configurations in ONTAP. |
Supported workload data sources
Ransomware Resilience protects the following application-based workloads on primary data volumes:
-
Block storage
-
Databases:
-
Microsoft SQL Server
-
Oracle
-
PostgreSQL
-
-
NetApp file shares
-
VMware datastores
Key terms
You might benefit by understanding some terminology related to ransomware protection.
-
Protection: Protection in Ransomware Resilience means ensuring that snapshots and immutable backups occur on a regular basis to a different security domain using protection policies.
-
Workload: A workload in Ransomware Resilience can include Oracle databases, VMware datastores, or file shares.


