Cyber vault frequently asked questions
 Suggest changes
Suggest changes


This FAQ is intended for NetApp customers and partners. It answers frequently asked questions about the NetApp's ONTAP based cyber vault reference architecture.
What is a NetApp cyber vault?
Cyber vault is a specific data protection technique that involves storing data in an isolated environment, separate from the primary IT infrastructure.
Cyber vault is an "air-gapped", immutable, and indelible data repository that is immune to threats affecting the primary data, such as malware, ransomware, or insider threats. A cyber vault can be achieved with immutable NetApp ONTAP Snapshot copies and made indelible with NetApp SnapLock Compliance. While under SnapLock Compliance protection, data cannot be modified or deleted, not even by ONTAP administrators or NetApp Support.
Air-gapping backups using traditional methods involve creating space and physically separating the primary and secondary media. Air-gapping with cyber vault includes using a separate data replication network outside of standard data access networks to replicate Snapshot copies to an indelible destination.
Further steps beyond air-gapped networks involves disabling all data access and replication protocols on the cyber vault when they are not needed. This prevents data access or data exfiltration at the destination site. With SnapLock Compliance, physical separation is not required. SnapLock Compliance protects your vaulted, point-in-time, read-only Snapshot copies, resulting in rapid data recovery, thats safe from deletion, and immutable.
NetApp's approach to cyber vault
NetApp cyber vault, powered by SnapLock, provides organizations with a comprehensive and flexible solution for protecting their most critical data assets. By leveraging hardening technologies in ONTAP, NetApp enables you to create a secure, air-gapped, and isolated cyber vault that is immune against evolving cyber threats. With NetApp, you can ensure the confidentiality, integrity, and availability of your data while maintaining the agility and efficiency of your storage infrastructure.
Key features of the NetApp reference architecture for a cyber vault include:
-
Secure, isolated storage infrastructure (e.g., air-gapped storage systems)
-
Backup copies of your data are both immutable and indelible
-
Strict and separate access controls, multi-administrator verification and multi-factor authentication
-
Rapid data restoration capabilities
Cyber vault frequently asked questions
Is cyber vault a product from NetApp?
No, "cyber vault" is an industry wide term. NetApp has created a reference architecture to make it easy for customers to build their own cyber vaults and leverage the dozens of ONTAP security features to help protect their data from cyber threats. More information is available on the ONTAP documentation site.
Is cyber vault with NetApp just another name for LockVault or SnapVault?
LockVault was a feature of Data ONTAP 7-mode that is not available in the current versions of ONTAP.
SnapVault was a legacy term for what is now accomplished with SnapMirror's vault policy. This policy allows the destination to retain a different quantity of Snapshot copies than the source volume.
Cyber vault is using SnapMirror with the vault policy and SnapLock Compliance together to create an immutable and indelible copy of data.
Which NetApp hardware can I use for a cyber vault, FAS, capacity flash, or performance flash?
This reference architecture for cyber vaulting applies to the entire ONTAP hardware portfolio. Customers can use AFF A-Series, AFF C-Series or FAS platforms as the vault. Flash-based platforms will provide the fastest recovery times while disk-based platforms will provide the most cost-effective solution. Depending on how much data is being recovered and if multiple recoveries are happening in parallel, using disk-based systems (FAS) may take days to weeks to complete. Please consult with a NetApp or partner representative to properly size a cyber vault solution to meet the business requirements.
Can I use Cloud Volumes ONTAP as a cyber vault source?
Yes, however using CVO as a source requires the data to be replicated to an on-prem cyber vault destination as SnapLock Compliance is a requirement for an ONTAP cyber vault. The data replication from a hyperscaler based CVO instance may incur egress charges.
Can I use Cloud Volumes ONTAP as a cyber vault destination?
The Cyber Vault architecture relies on ONTAP's SnapLock Compliance's indelibility and is designed for on-prem implementations. Cloud-based Cyber Vault architectures are under investigation for future publication.
Can I use ONTAP Select as a cyber vault source?
Yes, ONTAP Select can be used as a source to an on-prem hardware based cyber vault destination.
Can I use ONTAP Select as a cyber vault destination?
No, ONTAP Select should not be used as a cyber vault destination as it does not have the ability to use SnapLock Compliance.
Is a cyber vault with NetApp just using SnapMirror?
No, a NetApp cyber vault architecture leverages many ONTAP features to create a secure, isolated, air-gapped and hardened copy of data. For more information on what additional technical can be used see the next question.
Is there any other technology or configurations used for cyber vault?
The foundation of a NetApp cyber vault is SnapMirror and SnapLock Compliance but using additional ONTAP features such as tamperproof Snapshot copies, Multi Factor Authentication (MFA), Multi Admin Verify, role-based access control, and remote and local audit logging, improves the security and safety of one's data.
What makes ONTAP Snapshot copies better than others for a cyber vault?
ONTAP Snapshot copies are immutable by default and can be made indelible with SnapLock Compliance. Not even NetApp support can delete the SnapLock Snapshot copies. The better question to ask is what makes NetApp cyber vault better than other cyber vaults in the industry. First, ONTAP is the most secure storage on the planet and has obtained CSfC validation which allows for the storage of secret and top-secret data at rest at both the hardware and software layers. More information on CSfC can be found here. In addition, ONTAP can be air-gapped at the storage layer, with the cyber vault system controlling the replication allowing for an air-gap to be created within the cyber vault network.
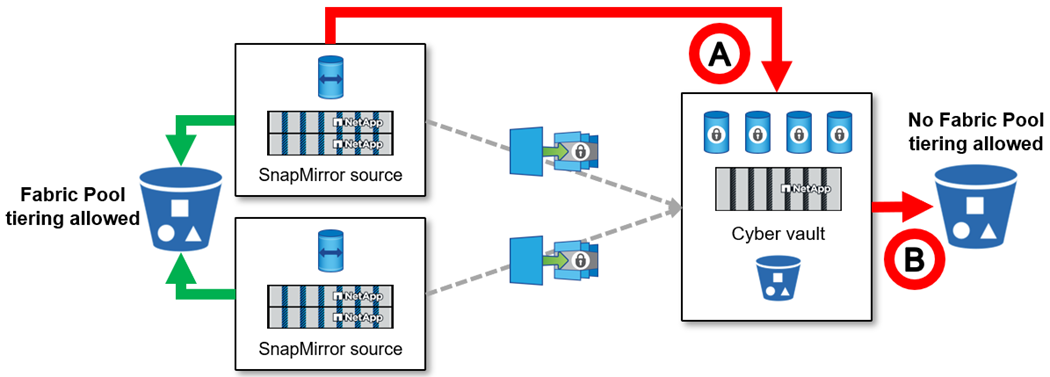
Can a volume on a cyber vault use ONTAP Fabric Pool?
No, a cyber vault volume (SnapLock Compliance SnapMirror destination), can not be tiered off using Fabric Pool, regardless of policy.

|
There are multiple scenarios in which Fabric pool can not be used with a cyber vault. |
-
Fabric Pool cold tiers can not be using a cyber vault cluster. This is because enabling the S3 protocol invalidates the secure nature of the cyber vault reference architecture. Additionally, the S3 bucket used for Fabric pool can not be protected.
-
SnapLock Compliance volumes on the cyber vault can not be tiered to a S3 bucket as the data is locked in the volume.

Is ONTAP S3 Worm available on a cyber vault?
No, S3 is a data access protocol that invalidates the secure nature of the reference architecture.
Does NetApp cyber vault run on a different ONTAP personality or profile?
No, it's a reference architecture. Customers can use the reference architecture and build a cyber vault, or can use the PowerShell scripts to create, harden and validate a cyber vault.
Can I turn on data protocols such as NFS, SMB and S3 in a cyber vault?
By default, data protocols should be disabled on the cyber vault to make it secure. However, data protocols can be enabled on the cyber vault to access data for recovery or when needed. This should be done on a temporary basis and disabled after recovery has completed.
Can you convert an existing SnapVault environment to a cyber vault, or do you need to reseed everything?
Yes. One could take a system that is a SnapMirror destination (with vault policy), disable the data protocols, harden the system per the ONTAP hardening guide, isolate it a secure location, and follow the other procedures in the reference architecture to make it a cyber vault without having to reseed the destination.
Have additional questions?
Please email ng-cyber-vault@netapp.com with your questions! We will respond and add your questions to the FAQ.


