ONTAP cyber vault overview
 Suggest changes
Suggest changes


The primary driving threat that necessitates the implementation of a cyber vault is the growing prevalence and evolving sophistication of cyber-attacks, particularly ransomware and data breaches. With a rise in phishing and ever more sophisticated methods of credential stealing, credentials used to begin a ransomware attack could then be used to access infrastructure systems. In these cases, even hardened infrastructure systems are at risk of attack. The only defense to a compromised system is to have your data protected and isolated in a cyber vault.
NetApp's ONTAP based cyber vault provides organizations with a comprehensive and flexible solution for protecting their most critical data assets. By leveraging logical air-gapping with robust hardening methodologies, ONTAP enables you to create secure, isolated storage environments that are resilient against evolving cyber threats. With ONTAP, you can ensure the confidentiality, integrity, and availability of your data while maintaining the agility and efficiency of your storage infrastructure.

|
Beginning in July 2024, content from technical reports previously published as PDFs has been integrated with ONTAP product documentation. In addition, new technical reports (TRs) such as this document will no longer be getting TR numbers. |
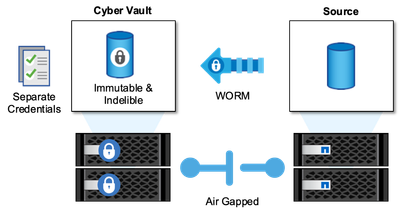
What is a cyber vault?
A cyber vault is a specific data protection technique that involves storing critical data in an isolated environment, separate from the primary IT infrastructure.
"Air-gapped", immutable and indelible data repository that is immune to threats affecting the main network, such as malware, ransomware, or even insider threats. A cyber vault can be achieved with immutable and indelible snapshots.
Air-gapping backups that use traditional methods involve creating space and physically separating the primary and secondary media. By moving the media offsite and/or severing connectivity, bad actors have no access to the data. This protects the data but can lead to slower recovery times.
NetApp's approach to cyber vault
Key features of NetApp reference architecture for a cyber vault include:
-
Secure, isolated storage infrastructure (e.g., air-gapped storage systems)
-
Copies of the data must be both immutable and indelible without exception
-
Strict access controls and multi-factor authentication
-
Rapid data restoration capabilities
You can use NetApp storage with ONTAP as an air-gapped cyber vault by leveraging SnapLock Compliance to WORM-protect Snapshot copies. You can perform all the basic SnapLock Compliance tasks on the Cyber vault. Once configured, Cyber vault volumes are automatically protected, eliminating the need to manually commit the Snapshot copies to WORM. More information on logical air-gapping can be found in this blog
SnapLock Compliance is used to comply with the Banking and Financial regulations SEC 70-a-4(f), FINRA 4511(c), and CFTC 1.31(c)-(d). It has been certified by Cohasset Associates to adhere to these regulations (audit report available upon request). By using SnapLock Compliance with this certification you get a hardened mechanism for air-gapping of your data that is relied upon by the largest financial institutions in the world to ensure both retention and retrieval of banking records.