Azure marketplace image signature verfication for Cloud Volumes ONTAP
 Suggest changes
Suggest changes


The Azure image verification process generates a digest file from the VHD file by stripping 1 MB at the beginning and 512 bytes at the end, then applying a hash function. To match the signing procedure, sha256 is used for hashing.
File signature verification workflow summary
The following is an overview of the file signature verification workflow process.
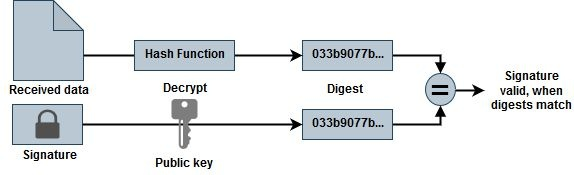
-
Downloading the Azure image from the NetApp Support Site and extracting the digest (.sig) file, public key certificate (.pem) file, and chain certificate (.pem) file. Refer to Download the Azure image digest file for more information.
-
Verification of the chain of trust.
-
Extracting the public key (.pub) from the public key certificate (.pem).
-
Decrypting the digest file by using the extracted public key.
-
Comparing the result against a newly generated digest of a temporary file created from the image file after removing 1 MB at the beginning and 512 bytes at the end. This step is performed by using the OpenSSL command line tool. The OpenSSL CLI tool displays appropriate messaging on success or failure in matching the files.
openssl dgst -verify <public_key> -keyform <form> <hash_function> -signature <digest_file> -binary <temporary_file>


