Set up Google Cloud networking for Cloud Volumes ONTAP
 Suggest changes
Suggest changes


The NetApp Console handles the set up of networking components for Cloud Volumes ONTAP, such as IP addresses, netmasks, and routes. You need to make sure that outbound internet access is available, that enough private IP addresses are available, that the right connections are in place, and more.
If you want to deploy an HA pair, you should learn how HA pairs work in Google Cloud.
Requirements for Cloud Volumes ONTAP
The following requirements must be met in Google Cloud.
Requirements specific to single node systems
If you want to deploy a single node system, ensure that your networking meets the following requirements.
One VPC
One Virtual Private Cloud (VPC) is required for a single node system.
Private IP addresses
For a single node system in Google Cloud, the Console allocates private IP addresses to the following:
-
Node
-
Cluster
-
Storage VM
-
Data NAS LIF
-
Data iSCSI LIF
You can skip creation of the storage VM (SVM) management LIF if you deploy Cloud Volumes ONTAP using the API and specify the following flag:
skipSvmManagementLif: true

|
A LIF is an IP address associated with a physical port. A storage VM (SVM) management LIF is required for management tools like SnapCenter. |
Requirements specific to HA pairs
If you want to deploy an HA pair, ensure that your networking meets the following requirements.
One or multiple zones
You can ensure the high availability of your data by deploying an HA configuration across multiple or in a single zone. The Console prompts you to choose multiple zones or a single zone when you create the HA pair.
-
Multiple zones (recommended)
Deploying an HA configuration across three zones ensures continuous data availability if a failure occurs within a zone. Note that write performance is slightly lower compared to using a single zone, but it's minimal.
-
Single zone
When deployed in a single zone, a Cloud Volumes ONTAP HA configuration uses a spread placement policy. This policy ensures that an HA configuration is protected from a single point of failure within the zone, without having to use separate zones to achieve fault isolation.
This deployment model does lower your costs because there are no data egress charges between zones.
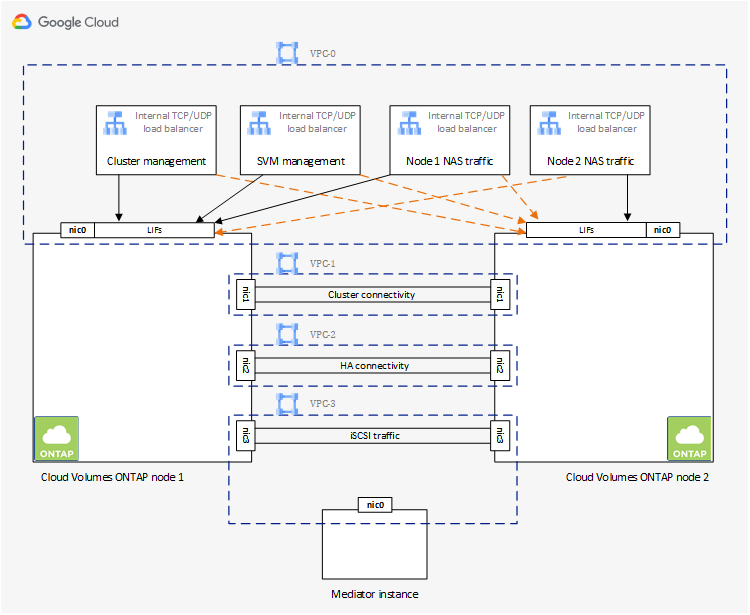
Four Virtual Private Clouds
Four Virtual Private Clouds (VPCs) are required for an HA configuration. Four VPCs are required because Google Cloud requires that each network interface resides in a separate VPC network.
The Console prompts you to choose four VPCs when you create the HA pair:
-
VPC-0 for inbound connections to the data and nodes
-
VPC-1, VPC-2, and VPC-3 for internal communication between the nodes and the HA mediator
Subnets
A private subnet is required for each VPC.
If you place the Console agent in VPC-0, then you will need to enable Private Google Access on the subnet to access the APIs and to enable data tiering.
The subnets in these VPCs must have distinct CIDR ranges. They can't have overlapping CIDR ranges.
Private IP addresses
The Console automatically allocates the required number of private IP addresses to Cloud Volumes ONTAP in Google Cloud. You need to make sure that your networking has enough private addresses available.
The number of LIFs allocated for Cloud Volumes ONTAP depends on whether you deploy a single node system or an HA pair. A LIF is an IP address associated with a physical port. An SVM management LIF is required for management tools like SnapCenter.
-
Single node
The Console allocates 4 IP addresses to a single node system:-
Node management LIF
-
Cluster management LIF
-
iSCSI data LIF
An iSCSI LIF provides client access over the iSCSI protocol and is used by the system for other important networking workflows. These LIFs are required and should not be deleted. -
NAS LIF
You can skip creation of the storage VM (SVM) management LIF if you deploy Cloud Volumes ONTAP using the API and specify the following flag:
skipSvmManagementLif: true
-
-
HA pair
The Console allocates 12-13 IP addresses to an HA pair:-
2 Node management LIFs (e0a)
-
1 Cluster management LIF (e0a)
-
2 iSCSI LIFs (e0a)
An iSCSI LIF provides client access over the iSCSI protocol and is used by the system for other important networking workflows. These LIFs are required and should not be deleted. -
1 or 2 NAS LIFs (e0a)
-
2 Cluster LIFs (e0b)
-
2 HA Interconnect IP addresses (e0c)
-
2 RSM iSCSI IP addresses (e0d)
You can skip creation of the storage VM (SVM) management LIF if you deploy Cloud Volumes ONTAP using the API and specify the following flag:
skipSvmManagementLif: true
-
Internal load balancers
The Console creates four Google Cloud internal load balancers (TCP/UDP) that manage incoming traffic to the Cloud Volumes ONTAP HA pair. No setup is required from your end. We've listed this as a requirement simply to inform you of the network traffic and to mitigate any security concerns.
One load balancer is for cluster management, one is for storage VM (SVM) management, one is for NAS traffic to node 1, and the last is for NAS traffic to node 2.
The setup for each load balancer is as follows:
-
One shared private IP address
-
One global health check
By default, the ports used by the health check are 63001, 63002, and 63003.
-
One regional TCP backend service
-
One regional UDP backend service
-
One TCP forwarding rule
-
One UDP forwarding rule
-
Global access is disabled
Even though global access is disabled by default, enabling it post deployment is supported. We disabled it because cross region traffic will have significantly higher latencies. We wanted to ensure that you didn't have a negative experience due to accidental cross region mounts. Enabling this option is specific to your business needs.
Shared VPCs
Cloud Volumes ONTAP and the Console agent are supported in a Google Cloud shared VPC and also in standalone VPCs.
For a single node system, the VPC can be either a shared VPC or a standalone VPC.
For an HA pair, four VPCs are required. Each of those VPCs can be either shared or standalone. For example, VPC-0 could be a shared VPC, while VPC-1, VPC-2, and VPC-3 could be standalone VPCs.
A shared VPC enables you to configure and centrally manage virtual networks across multiple projects. You can set up shared VPC networks in the host project and deploy the Console agent and Cloud Volumes ONTAP virtual machine instances in a service project.
Packet mirroring in VPCs
Packet mirroring must be disabled in the Google Cloud subnet in which you deploy Cloud Volumes ONTAP.
Outbound internet access
Cloud Volumes ONTAP systems require outbound internet access for accessing external endpoints for various functions. Cloud Volumes ONTAP can't operate properly if these endpoints are blocked in environments with strict security requirements.
The Console agent also contacts several endpoints for day-to-day operations. For information about the endpoints, refer to View endpoints contacted from the Console agent and Prepare networking for using the Console.
Cloud Volumes ONTAP endpoints
Cloud Volumes ONTAP uses these endpoints to communicate with various services.
| Endpoints | Applicable for | Purpose | Deployment mode | Impact if endpoint is not available |
|---|---|---|---|---|
https://netapp-cloud-account.auth0.com |
Authentication |
Used for authentication in the Console. |
Standard and restricted modes. |
User authentication fails and the following services remain unavailable:
|
https://api.bluexp.netapp.com/tenancy |
Tenancy |
Used to retrieve Cloud Volumes ONTAP resource from the Console to authorize resources and users. |
Standard and restricted modes. |
Cloud Volumes ONTAP resources and the users are not authorized. |
https://mysupport.netapp.com/aods/asupmessage |
AutoSupport |
Used to send AutoSupport telemetry data to NetApp support. |
Standard and restricted modes. |
AutoSupport information remains undelivered. |
https://cloudbuild.googleapis.com/v1 (for only private mode deployments) |
Google Cloud (Commercial use). |
Communication with Google Cloud services. |
Standard, restricted, and private modes. |
Cloud Volumes ONTAP cannot communicate with Google Cloud service to perform specific operations for the Console in Google Cloud. |
Connections to ONTAP systems in other networks
To replicate data between a Cloud Volumes ONTAP system in Google Cloud and ONTAP systems in other networks, you must have a VPN connection between the VPC and the other network—for example, your corporate network.
Firewall rules
The Console creates Google Cloud firewall rules that include the inbound and outbound rules that Cloud Volumes ONTAP needs to operate successfully. You might want to refer to the ports for testing purposes or if you prefer to use your own firewall rules.
The firewall rules for Cloud Volumes ONTAP requires both inbound and outbound rules. If you're deploying an HA configuration, these are the firewall rules for Cloud Volumes ONTAP in VPC-0.
Note that two sets of firewall rules are required for an HA configuration:
-
One set of rules for HA components in VPC-0. These rules enable data access to Cloud Volumes ONTAP.
-
Another set of rules for HA components in VPC-1, VPC-2, and VPC-3. These rules are open for inbound & outbound communication between the HA components. Learn more.

|
Looking for information about the Console agent? View firewall rules for the Console agent |
Inbound rules
When you add a Cloud Volumes ONTAP system, you can choose the source filter for the predefined firewall policy during deployment:
-
Selected VPC only: the source filter for inbound traffic is the subnet range of the VPC for the Cloud Volumes ONTAP system and the subnet range of the VPC where the Console agent resides. This is the recommended option.
-
All VPCs: the source filter for inbound traffic is the 0.0.0.0/0 IP range.
If you use your own firewall policy, ensure that you add all networks that need to communicate with Cloud Volumes ONTAP, but also ensure to add both address ranges to allow the internal Google Load Balancer to function correctly. These addresses are 130.211.0.0/22 and 35.191.0.0/16. For more information, refer to the Google Cloud documentation: Load Balancer Firewall Rules.
| Protocol | Port | Purpose |
|---|---|---|
All ICMP |
All |
Pinging the instance |
HTTP |
80 |
HTTP access to the ONTAP System Manager web console using the IP address of the cluster management LIF |
HTTPS |
443 |
Connectivity with the Console agent and HTTPS access to the ONTAP System Manager web console using the IP address of the cluster management LIF |
SSH |
22 |
SSH access to the IP address of the cluster management LIF or a node management LIF |
TCP |
111 |
Remote procedure call for NFS |
TCP |
139 |
NetBIOS service session for CIFS |
TCP |
161-162 |
Simple network management protocol |
TCP |
445 |
Microsoft SMB/CIFS over TCP with NetBIOS framing |
TCP |
635 |
NFS mount |
TCP |
749 |
Kerberos |
TCP |
2049 |
NFS server daemon |
TCP |
3260 |
iSCSI access through the iSCSI data LIF |
TCP |
4045 |
NFS lock daemon |
TCP |
4046 |
Network status monitor for NFS |
TCP |
10000 |
Backup using NDMP |
TCP |
11104 |
Management of intercluster communication sessions for SnapMirror |
TCP |
11105 |
SnapMirror data transfer using intercluster LIFs |
TCP |
63001-63050 |
Load balance probe ports to determine which node is healthy (required for HA pairs only) |
UDP |
111 |
Remote procedure call for NFS |
UDP |
161-162 |
Simple network management protocol |
UDP |
635 |
NFS mount |
UDP |
2049 |
NFS server daemon |
UDP |
4045 |
NFS lock daemon |
UDP |
4046 |
Network status monitor for NFS |
UDP |
4049 |
NFS rquotad protocol |
Outbound rules
The predefined security group for Cloud Volumes ONTAP opens all outbound traffic. If that is acceptable, follow the basic outbound rules. If you need more rigid rules, use the advanced outbound rules.
The predefined security group for Cloud Volumes ONTAP includes the following outbound rules.
| Protocol | Port | Purpose |
|---|---|---|
All ICMP |
All |
All outbound traffic |
All TCP |
All |
All outbound traffic |
All UDP |
All |
All outbound traffic |
If you need rigid rules for outbound traffic, you can use the following information to open only those ports that are required for outbound communication by Cloud Volumes ONTAP. The Cloud Volumes ONTAP clusters use the following ports for regulating nodes traffic.

|
The source is the interface (IP address) of the Cloud Volumes ONTAP system. |
| Service | Protocol | Port | Source | Destination | Purpose |
|---|---|---|---|---|---|
Active Directory |
TCP |
88 |
Node management LIF |
Active Directory forest |
Kerberos V authentication |
UDP |
137 |
Node management LIF |
Active Directory forest |
NetBIOS name service |
|
UDP |
138 |
Node management LIF |
Active Directory forest |
NetBIOS datagram service |
|
TCP |
139 |
Node management LIF |
Active Directory forest |
NetBIOS service session |
|
TCP & UDP |
389 |
Node management LIF |
Active Directory forest |
LDAP |
|
TCP |
445 |
Node management LIF |
Active Directory forest |
Microsoft SMB/CIFS over TCP with NetBIOS framing |
|
TCP |
464 |
Node management LIF |
Active Directory forest |
Kerberos V change & set password (SET_CHANGE) |
|
UDP |
464 |
Node management LIF |
Active Directory forest |
Kerberos key administration |
|
TCP |
749 |
Node management LIF |
Active Directory forest |
Kerberos V change & set Password (RPCSEC_GSS) |
|
TCP |
88 |
Data LIF (NFS, CIFS, iSCSI) |
Active Directory forest |
Kerberos V authentication |
|
UDP |
137 |
Data LIF (NFS, CIFS) |
Active Directory forest |
NetBIOS name service |
|
UDP |
138 |
Data LIF (NFS, CIFS) |
Active Directory forest |
NetBIOS datagram service |
|
TCP |
139 |
Data LIF (NFS, CIFS) |
Active Directory forest |
NetBIOS service session |
|
TCP & UDP |
389 |
Data LIF (NFS, CIFS) |
Active Directory forest |
LDAP |
|
TCP |
445 |
Data LIF (NFS, CIFS) |
Active Directory forest |
Microsoft SMB/CIFS over TCP with NetBIOS framing |
|
TCP |
464 |
Data LIF (NFS, CIFS) |
Active Directory forest |
Kerberos V change & set password (SET_CHANGE) |
|
UDP |
464 |
Data LIF (NFS, CIFS) |
Active Directory forest |
Kerberos key administration |
|
TCP |
749 |
Data LIF (NFS, CIFS) |
Active Directory forest |
Kerberos V change & set password (RPCSEC_GSS) |
|
AutoSupport |
HTTPS |
443 |
Node management LIF |
mysupport.netapp.com |
AutoSupport (HTTPS is the default) |
HTTP |
80 |
Node management LIF |
mysupport.netapp.com |
AutoSupport (only if the transport protocol is changed from HTTPS to HTTP) |
|
TCP |
3128 |
Node management LIF |
Console agent |
Sending AutoSupport messages through a proxy server on the Console agent, if an outbound internet connection isn't available |
|
Configuration backups |
HTTP |
80 |
Node management LIF |
http://<console-agent-IP-address>/occm/offboxconfig |
Send configuration backups to the Console agent. ONTAP documentation |
DHCP |
UDP |
68 |
Node management LIF |
DHCP |
DHCP client for first-time setup |
DHCPS |
UDP |
67 |
Node management LIF |
DHCP |
DHCP server |
DNS |
UDP |
53 |
Node management LIF and data LIF (NFS, CIFS) |
DNS |
DNS |
NDMP |
TCP |
18600–18699 |
Node management LIF |
Destination servers |
NDMP copy |
SMTP |
TCP |
25 |
Node management LIF |
Mail server |
SMTP alerts, can be used for AutoSupport |
SNMP |
TCP |
161 |
Node management LIF |
Monitor server |
Monitoring by SNMP traps |
UDP |
161 |
Node management LIF |
Monitor server |
Monitoring by SNMP traps |
|
TCP |
162 |
Node management LIF |
Monitor server |
Monitoring by SNMP traps |
|
UDP |
162 |
Node management LIF |
Monitor server |
Monitoring by SNMP traps |
|
SnapMirror |
TCP |
11104 |
Intercluster LIF |
ONTAP intercluster LIFs |
Management of intercluster communication sessions for SnapMirror |
TCP |
11105 |
Intercluster LIF |
ONTAP intercluster LIFs |
SnapMirror data transfer |
|
Syslog |
UDP |
514 |
Node management LIF |
Syslog server |
Syslog forward messages |
Rules for VPC-1, VPC-2, and VPC-3
In Google Cloud, an HA configuration is deployed across four VPCs. The firewall rules needed for the HA configuration in VPC-0 are listed above for Cloud Volumes ONTAP.
Meanwhile, the predefined firewall rules created for the instances in VPC-1, VPC-2, and VPC-3 enable ingress communication over all protocols and ports. These rules enable communication between HA nodes.
Communication from the HA nodes to the HA mediator takes place over port 3260 (iSCSI).

|
To enable high write speed for new Google Cloud HA pair deployments, a maximum transmission unit (MTU) of at least 8,896 bytes is required for VPC-1, VPC-2, and VPC-3. If you choose to upgrade existing VPC-1, VPC-2, and VPC-3 to an MTU of 8,896 bytes, you must shutdown all existing HA systems using these VPCs during the configuration process. |
Requirements for the Console agent
If you haven't created a Console agent yet, you should review networking requirements.
Network configurations to support Console agent proxy
You can use the proxy servers configured for the Console agent to enable outbound internet access from Cloud Volumes ONTAP. The Console supports two types of proxies:
-
Explicit proxy: The outbound traffic from Cloud Volumes ONTAP uses the HTTP address of the proxy server specified during the Console agent proxy configuration. The Console agent administrator might also have configured user credentials and root CA certificates for additional authentication. If a root CA certificate is available for the explicit proxy, make sure to obtain and upload the same certificate to your Cloud Volumes ONTAP system using the ONTAP CLI: security certificate install command.
-
Transparent proxy: The network is configured to automatically route outbound traffic from Cloud Volumes ONTAP through the Console agent proxy. When setting up a transparent proxy, the Console agent administrator needs to provide only a root CA certificate for connectivity from Cloud Volumes ONTAP, not the HTTP address of the proxy server. Make sure that you obtain and upload the same root CA certificate to your Cloud Volumes ONTAP system using the ONTAP CLI: security certificate install command.
For information about configuring proxy servers for the Console agent, refer to the Configure a Console agent to use a proxy server.
During the transparent proxy configuration of the Console agent, the administrator adds a network tag for Google Cloud. You need to obtain and manually add the same network tag for your Cloud Volumes ONTAP configuration. This tag is necessary for the proxy server to function correctly.
-
In the Google Cloud Console, locate your Cloud Volumes ONTAP system.
-
Go to Details > Networking > Network tags.
-
Add the tag used for the Console agent and save the configuration.


