Policies and permissions in StorageGRID
 Suggest changes
Suggest changes


Here are example Policies and permissions in StorageGRID S3.
The structure of a policy
In StorageGRID, group policies are the same as AWS user (IAM) S3 service policies.
Group policies are required in StorageGRID. A user with S3 access keys but not assigned to a user group, or assigned to a group without a policy granting some permissions, will not be able to access any data.
Bucket and group policies share most of the same elements. Policies are built in json format and can be generated using the AWS policy generator
All policies will define the effect, action(s), and resource(s). Bucket policies will also define a principal.
The Effect will be either to Allow or Deny the request.
The Principal
-
Only applies for bucket policies.
-
The principal is the account(s)/user(s) being granted or denied the permissions.
-
Can be defined as:
-
A wildcard "*"
"Principal":"*"
"Principal":{"AWS":"*"} -
A tenant ID for all users in a tenant (equivalent to AWS account)
"Principal": { "AWS": "27233906934684427525" } -
A user (local or federated from within the tenant the bucket resides, or another tenant in the grid)
"Principal": { "AWS": "arn:aws:iam::76233906934699427431:user/tenant1user1" }"Principal": { "AWS": "arn:aws:iam::27233906934684427525:federated-user/tenant2user1" } -
A group (local or federated from within the tenant the bucket resides, or another tenant in the grid).
"Principal": { "AWS": "arn:aws:iam::76233906934699427431:group/DevOps" }"Principal": { "AWS": "arn:aws:iam::27233906934684427525:federated-group/Managers" }
-
The Action is the set of S3 operations being granted or denied to the user(s).

|
For Group policies, the s3:ListBucket action Allowed is required for users to perform any S3 actions. |
The Resource is the bucket or buckets the principals being granted or denied the ability to perform the actions on.
Optionally there can be a Condition for when the policy action is valid.
The format of the Json policy will look like this:
{
"Statement": [
{
"Sid": "Custom name for this permission",
"Effect": "Allow or Deny",
"Principal": {
"AWS": [
"arn:aws:iam::tenant_ID::user/User_Name",
"arn:aws:iam::tenant_ID::federated-user/User_Name",
"arn:aws:iam::tenant_ID:group/Group_Name",
"arn:aws:iam::tenant_ID:federated-group/Group_Name",
"tenant_ID"
]
},
"Action": [
"s3:ListBucket",
"s3:Other_Action"
],
"Resource": [
"arn:aws:s3:::Example_Bucket",
"arn:aws:s3:::Example_Bucket/*"
],
}
]
}Using the AWS policy generator
The AWS policy generator is a great tool to assist with getting the json code with the correct format and information you are trying to implement.
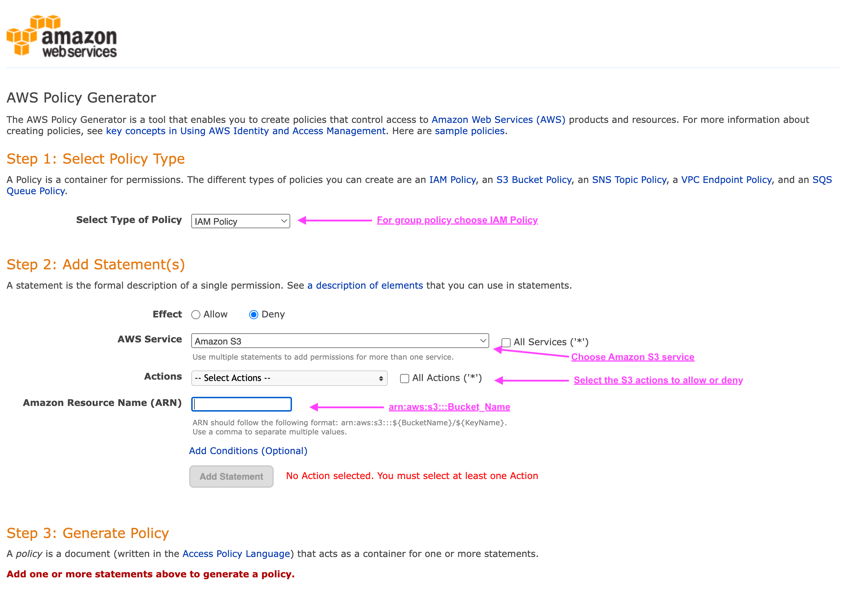
To generate the permissions for a StorageGRID group policy:
* choose the IAM policy for the type of policy.
* Select the button for the desired effect - Allow or Deny. It is a good practice to start your policies with the deny permissions and then add the allow permissions
* In the actions drop-down click the box next to as many of the S3 actions you want to include in this permission or the "All Actions" box.
* type in the bucket paths in the Amazon Resource Name (ARN) box. include "arn:aws:s3:::" before the bucket name. ex. "arn:aws:s3:::example_bucket"
To generate the permissions for a bucket policy:
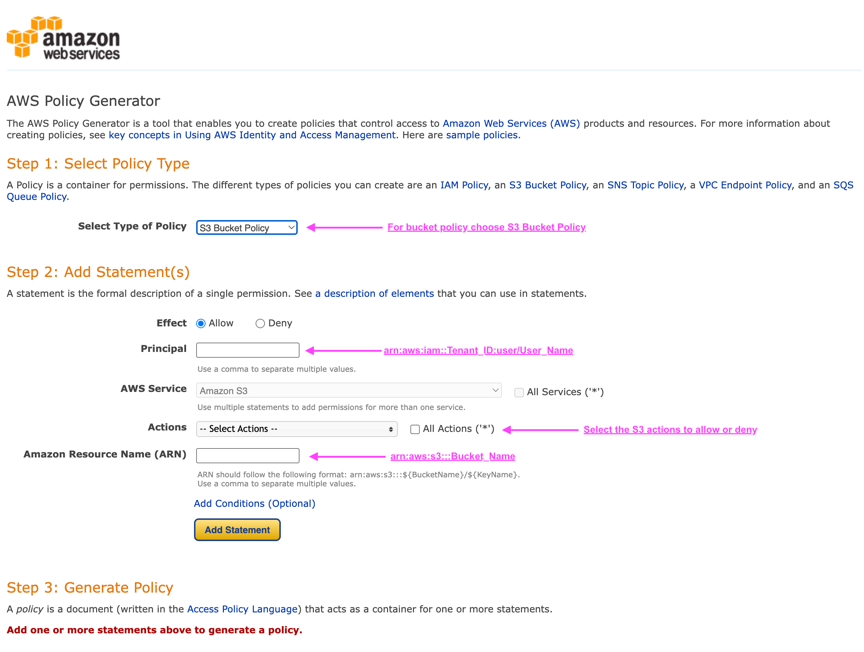
* choose the S3 Bucket Policy for the type of policy.
* Select the button for the desired effect - Allow or Deny. It is a good practice to start your policies with the deny permissions and then add the allow permissions
* Type in the user or group information for the Principal.
* In the actions drop-down click the box next to as many of the S3 actions you want to include in this permission or the "All Actions" box.
* type in the bucket paths in the Amazon Resource Name (ARN) box. include "arn:aws:s3:::" before the bucket name. ex. "arn:aws:s3:::example_bucket"
For an example, if you wanted to generate a bucket policy to allow all users to perform GetObject operations on all objects in the bucket, while only users belonging the group "Marketing" in the specified account are allowed full access.
-
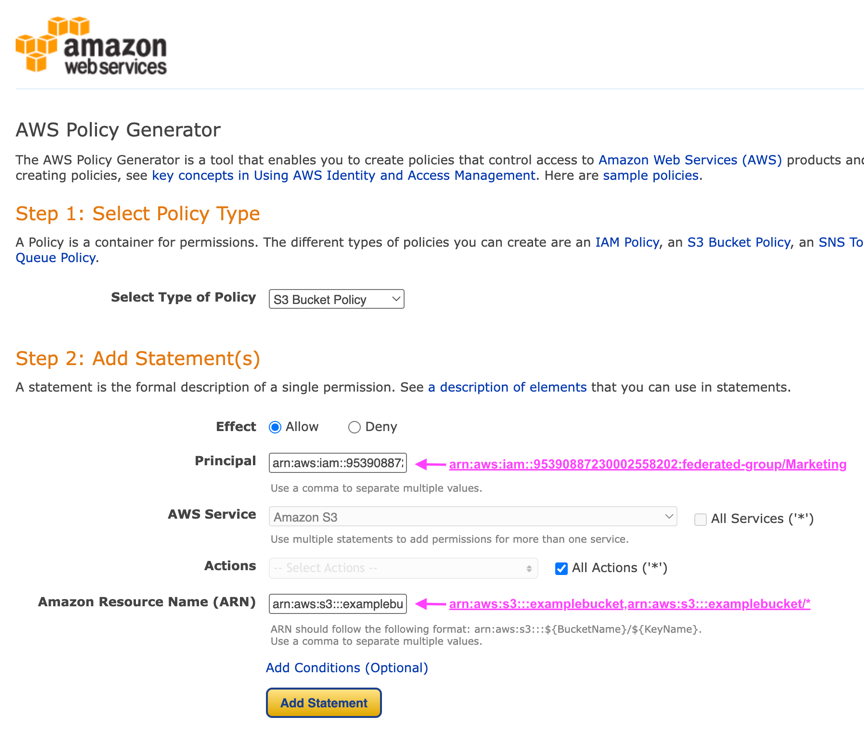
Select S3 Bucket Policy as the policy type.
-
Choose the Allow effect
-
Enter the Marketing group information - arn:aws:iam::95390887230002558202:federated-group/Marketing
-
Click the box for "All Actions"
-
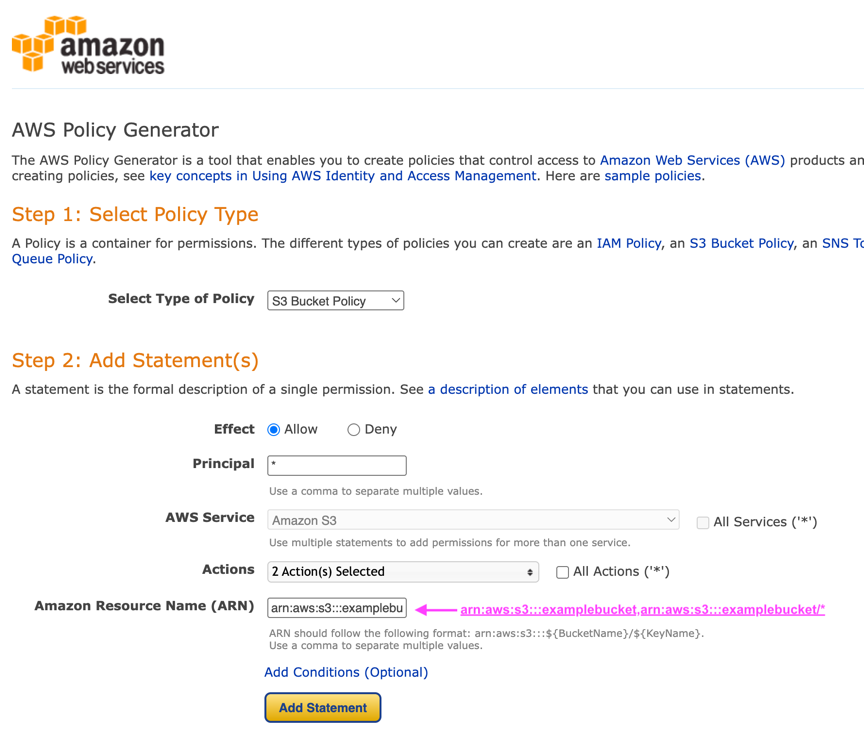
Enter the bucket information - arn:aws:s3:::example_bucket,arn:aws:s3:::example_bucket/*
-
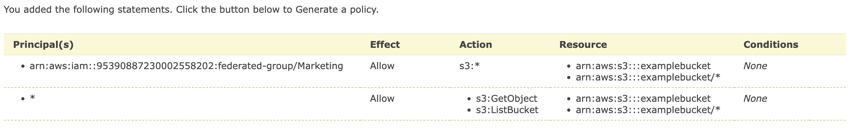
click the "Add Statement" button

-
Choose the Allow effect
-
Enter the asterisk * for everyone
-
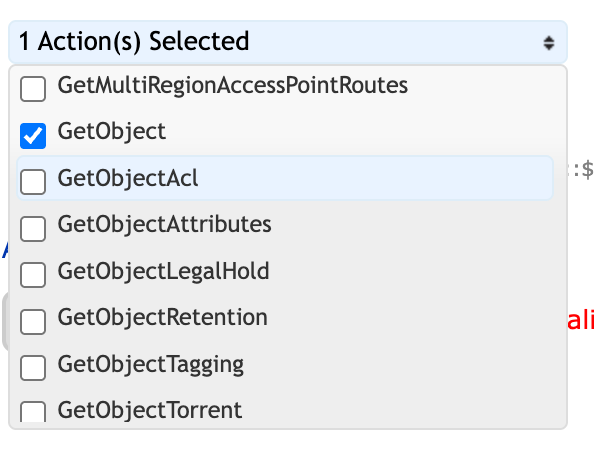
Click the box next to GetObject and ListBucket actions"
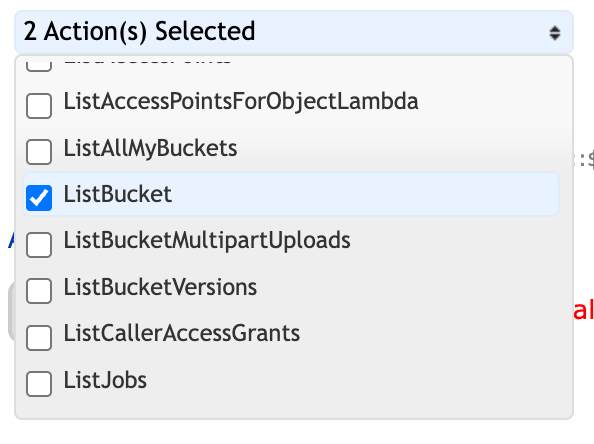
-
Enter the bucket information - arn:aws:s3:::example_bucket,arn:aws:s3:::example_bucket/*
-
click the "Add Statement" button
-
Click on the button "Generate Policy" and a pop-up window will appear with your generated policy.
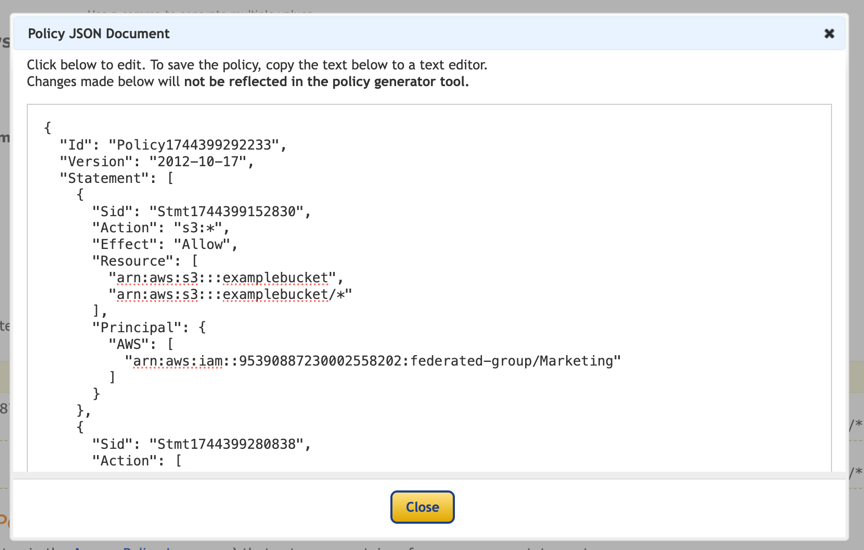
-
Copy out the complete json text that should look like this:
{
"Id": "Policy1744399292233",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1744399152830",
"Action": "s3:*",
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::example_bucket",
"arn:aws:s3:::example_bucket/*"
],
"Principal": {
"AWS": [
"arn:aws:iam::95390887230002558202:federated-group/Marketing"
]
}
},
{
"Sid": "Stmt1744399280838",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::example_bucket",
"arn:aws:s3:::example_bucket/*"
],
"Principal": "*"
}
]
}This json can be used as is, or you can remove the ID and Version lines above the "Statement" line and you can customize the Sid for each permission with a more meaningful title for each permission or these can be removed as well.
For example:
{
"Statement": [
{
"Sid": "MarketingAllowFull",
"Action": "s3:*",
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::example_bucket",
"arn:aws:s3:::example_bucket/*"
],
"Principal": {
"AWS": [
"arn:aws:iam::95390887230002558202:federated-group/Marketing"
]
}
},
{
"Sid": "EveryoneReadOnly",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::example_bucket",
"arn:aws:s3:::example_bucket/*"
],
"Principal": "*"
}
]
}Group Policies (IAM)
Home Directory style bucket access
This group policy will only allow users to access objects in the bucket named the users username.
{
"Statement": [
{
"Sid": "AllowListBucketOfASpecificUserPrefix",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::home",
"Condition": {
"StringLike": {
"s3:prefix": "${aws:username}/*"
}
}
},
{
"Sid": "AllowUserSpecificActionsOnlyInTheSpecificUserPrefix",
"Effect": "Allow",
"Action": "s3:*Object",
"Resource": "arn:aws:s3:::home/?/?/${aws:username}/*"
}
]
}Deny object lock bucket creation
This group policy will restrict users from creating a bucket with object lock enabled on the bucket.

|
This policy is not enforced in the StorageGRID UI, it is only enforced by S3 API. |
{
"Statement": [
{
"Action": "s3:*",
"Effect": "Allow",
"Resource": "arn:aws:s3:::*"
},
{
"Action": [
"s3:PutBucketObjectLockConfiguration",
"s3:PutBucketVersioning"
],
"Effect": "Deny",
"Resource": "arn:aws:s3:::*"
}
]
}Object lock retention limit
This Bucket policy will restrict Object-Lock retention duration to 10 days or less
{
"Version":"2012-10-17",
"Id":"CustSetRetentionLimits",
"Statement": [
{
"Sid":"CustSetRetentionPeriod",
"Effect":"Deny",
"Principal":"*",
"Action": [
"s3:PutObjectRetention"
],
"Resource":"arn:aws:s3:::testlock-01/*",
"Condition": {
"NumericGreaterThan": {
"s3:object-lock-remaining-retention-days":"10"
}
}
}
]
}Restrict users from deleting objects by versionID
This group policy will restrict users from deleting versioned objects by versionID
{
"Statement": [
{
"Action": [
"s3:DeleteObjectVersion"
],
"Effect": "Deny",
"Resource": "arn:aws:s3:::*"
},
{
"Action": "s3:*",
"Effect": "Allow",
"Resource": "arn:aws:s3:::*"
}
]
}Restrict a group to single subdirectory (prefix) with read-only access
This policy allows members of the group to have read-only access to a subdirectory (prefix) within a bucket. The bucket name is "study" and the subdirectory is "study01".
{
"Statement": [
{
"Sid": "AllowUserToSeeBucketListInTheConsole",
"Action": [
"s3:ListAllMyBuckets"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Sid": "AllowRootAndstudyListingOfBucket",
"Action": [
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3::: study"
],
"Condition": {
"StringEquals": {
"s3:prefix": [
"",
"study01/"
],
"s3:delimiter": [
"/"
]
}
}
},
{
"Sid": "AllowListingOfstudy01",
"Action": [
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::study"
],
"Condition": {
"StringLike": {
"s3:prefix": [
"study01/*"
]
}
}
},
{
"Sid": "AllowAllS3ActionsInstudy01Folder",
"Effect": "Allow",
"Action": [
"s3:Getobject"
],
"Resource": [
"arn:aws:s3:::study/study01/*"
]
}
]
}Bucket Policies
Restrict bucket to single user with read-only access
This policy allows a single user to have read-only access to a bucket and explicitly denys access to all other users. Grouping the Deny statements at the top of the policy is a good practice for faster evaluation.
{
"Statement": [
{
"Sid": "Deny non user1",
"Effect": "Deny",
"NotPrincipal": {
"AWS": "arn:aws:iam::34921514133002833665:user/user1"
},
"Action": [
"s3:*"
],
"Resource": [
"arn:aws:s3:::bucket1",
"arn:aws:s3:::bucket1/*"
]
},
{
"Sid": "Allow user1 read access to bucket bucket1",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::34921514133002833665:user/user1"
},
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::bucket1",
"arn:aws:s3:::bucket1/*"
]
}
]
}restrict a bucket to a few users with read-only access.
{
"Statement": [
{
"Sid": "Deny all S3 actions to employees 002-005",
"Effect": "deny",
"Principal": {
"AWS": [
"arn:aws:iam::46521514133002703882:user/employee-002",
"arn:aws:iam::46521514133002703882:user/employee-003",
"arn:aws:iam::46521514133002703882:user/employee-004",
"arn:aws:iam::46521514133002703882:user/employee-005"
]
},
"Action": "*",
"Resource": [
"arn:aws:s3:::databucket1",
"arn:aws:s3:::databucket1/*"
]
},
{
"Sid": "Allow read-only access for employees 002-005",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::46521514133002703882:user/employee-002",
"arn:aws:iam::46521514133002703882:user/employee-003",
"arn:aws:iam::46521514133002703882:user/employee-004",
"arn:aws:iam::46521514133002703882:user/employee-005"
]
},
"Action": [
"s3:GetObject",
"s3:GetObjectTagging",
"s3:GetObjectVersion"
],
"Resource": [
"arn:aws:s3:::databucket1",
"arn:aws:s3:::databucket1/*"
]
}
]
}Restrict user deletes of versioned objects in a bucket
This bucket policy will restrict a user(identified by userID "56622399308951294926") from deleting versioned objects by versionID
{
"Statement": [
{
"Action": [
"s3:DeleteObjectVersion"
],
"Effect": "Deny",
"Resource": "arn:aws:s3:::verdeny/*",
"Principal": {
"AWS": [
"56622399308951294926"
]
}
},
{
"Action": "s3:*",
"Effect": "Allow",
"Resource": "arn:aws:s3:::verdeny/*",
"Principal": {
"AWS": [
"56622399308951294926"
]
}
}
]
}

