Manage the TLS and SSH policy
 Suggest changes
Suggest changes


The TLS and SSH policy determines which protocols and ciphers are used to establish secure TLS connections with client applications and secure SSH connections to internal StorageGRID services.
The security policy controls how TLS and SSH encrypt data in motion. In general, use the Modern compatibility (default) policy, unless your system needs to be Common Criteria-compliant or you need to use other ciphers.

|
Some StorageGRID services have not been updated to use the ciphers in these policies. |
-
You are signed in to the Grid Manager using a supported web browser.
-
You have the Root access permission.
Select a security policy
-
Select Configuration > Security > Security settings.
The TLS and SSH policies tab shows the available policies. The currently active policy is noted by a green check mark on the policy tile.
-
Review the tabs to learn about the available policies.
Modern compatibility (default)Use the default policy if you need strong encryption and you don't have special requirements. This policy is compatible with most TLS and SSH clients.
Legacy compatibilityUse the Legacy compatibility policy if you need additional compatibility options for older clients. The additional options in this policy might make it less secure than the Modern compatibility policy.
Common CriteriaUse the Common Criteria policy if you require Common Criteria certification.
FIPS strictUse the FIPS strict policy if you require Common Criteria certification and need to use the NetApp Cryptographic Security Module (NCSM) 3.0.8 or NetApp StorageGRID Kernel Crypto API 6.1.129-1-ntap1-amd64 module for external client connections to load balancer endpoints, Tenant Manager, and Grid Manager. Using this policy might reduce performance.
The NCSM 3.0.8 and NetApp StorageGRID Kernel Crypto API 6.1.129-1-ntap1-amd64 module are used in the following operations:
-
NCSM
-
TLS connections between the following services: ADC, AMS, CMN, DDS, LDR, SSM, NMS, mgmt-api, nginx, nginx-gw, and cache-svc
-
TLS connections between clients and the nginx-gw service (load balancer endpoints)
-
TLS connections between clients and the LDR service
-
Object content encryption for SSE-S3, SSE-C, and the Stored object encryption setting
-
SSH connections
For more information, refer to NIST Cryptographic Algorithm Validation Program Certificate #4838.
-
-
NetApp StorageGRID Kernel Crypto API module
The NetApp StorageGRID Kernel Crypto API module is present only on VM and StorageGRID appliance platforms.
-
Entropy collection
-
Node encryption
For more information, refer to NIST Cryptographic Algorithm Validation Program Certificates #A6242 through #A6257 and Entropy Certificate #E223.
-
Note: After you select this policy, perform a rolling reboot for all nodes to activate the NCSM. Use Maintenance > Rolling reboot to initiate and monitor reboots.
CustomCreate a custom policy if you need to apply your own ciphers.
Optionally, if your StorageGRID has FIPS 140 cryptography requirements, enable the FIPS mode feature to use the NCSM 3.0.8 and NetApp StorageGRID Kernel Crypto API 6.1.129-1-ntap1-amd64 module:
-
Set the
fipsModeparameter totrue. -
When prompted, perform a rolling reboot for all nodes to activate the cryptography modules. Use Maintenance > Rolling reboot to initiate and monitor reboots.
-
Select Support > Diagnostics to view the active FIPS module versions.
-
-
To see details about each policy's ciphers, protocols, and algorithms, select View details.
-
To change the current policy, select Use policy.
A green check mark appears next to Current policy on the policy tile.
Create a custom security policy
You can create a custom policy if you need to apply your own ciphers.
-
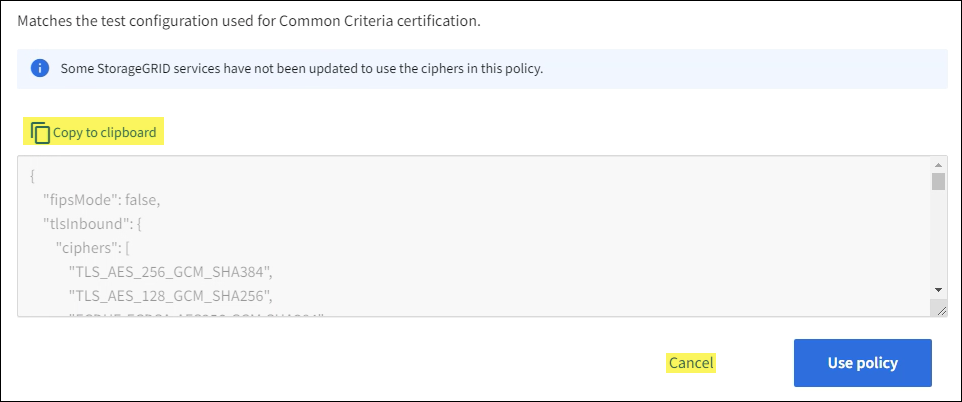
From the tile of the policy that is the most similar to the custom policy you want to create, select View details.
-
Select Copy to clipboard, and then select Cancel.
-
From the Custom policy tile, select Configure and use.
-
Paste the JSON you copied and make any changes required.
-
Select Use policy.
A green check mark appears next to Current policy on the Custom policy tile.
-
Optionally, select Edit configuration to make more changes to the new custom policy.
Temporarily revert to the default security policy
If you configured a custom security policy, you might not be able to sign in to the Grid Manager if the configured TLS policy is incompatible with the configured server certificate.
You can temporarily revert to the default security policy.
-
Log in to an Admin Node:
-
Enter the following command:
ssh admin@Admin_Node_IP -
Enter the password listed in the
Passwords.txtfile. -
Enter the following command to switch to root:
su - -
Enter the password listed in the
Passwords.txtfile.When you are logged in as root, the prompt changes from
$to#.
-
-
Run the following command:
restore-default-cipher-configurations -
From a web browser, access the Grid Manager on the same Admin Node.
-
Follow the steps in Select a security policy to configure the policy again.


