Integration with ONTAP Autonomous Ransomware Protection
 Suggest changes
Suggest changes


The ONTAP Autonomous Protection feature uses workload analysis in NAS (NFS and SMB) environments to proactively detect and warn about abnormal in-file activity that might indicate malicious attacks or unauthorized data modifications.
Additional details and license requirements about ARP can be found here.
Workload Security integrates with ONTAP to receive ARP events and provide an additional analytics and automatic responses layer.
Workload Security receives the ARP events from ONTAP and takes the following actions:
-
Correlates volume encryption events with user activity to identify who is causing the damage.
-
Implements automatic response policies (if defined)
-
Provides forensics capabilities:
-
Allow customers to conduct data breach investigations.
-
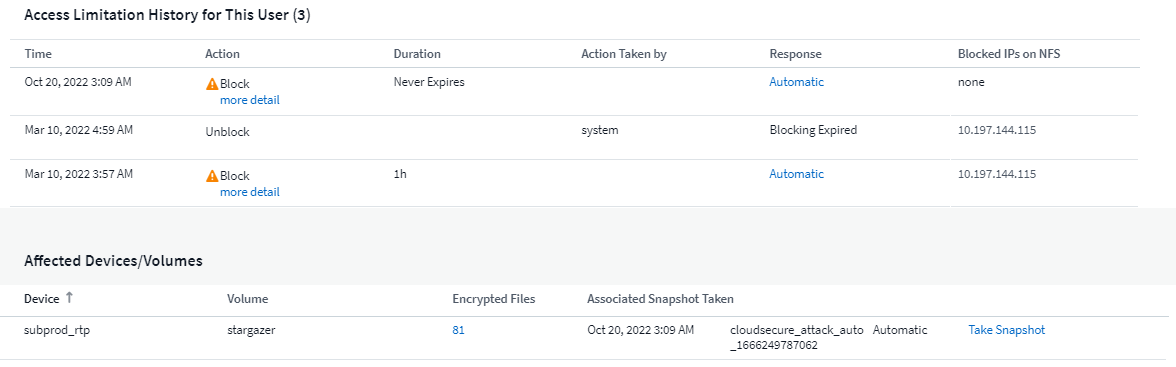
Identify what files were affected, helping to recover faster and conduct data breach investigations.
-
Prerequisites
-
Minimum ONTAP version: 9.11.1
-
ARP enabled volumes. Details on enabling ARP can be found here. ARP must be enabled via OnCommand System Manager. Workload Security cannot enable ARP.
-
Workload Security collector should be added via cluster IP.
-
Cluster level credentials are needed for this feature to work. In other words, cluster level credentials must be used when adding the SVM.
User permissions required
If you are using cluster administration credentials, no new permissions are needed.
If you are using a custom user (for example, csuser) with permissions given to the user, then follow the steps below to give permissions to Workload Security to collect ARP related information from ONTAP.
For csuser with cluster credentials, do the following from the ONTAP command line:
security login role create -role csrole -cmddirname "volume" -access readonly security login role create -role csrole -cmddirname "security anti-ransomware volume" -access readonly
Read more about configuring other ONTAP permissions.
Sample Alert
A sample alert generated due to ARP event is shown below:
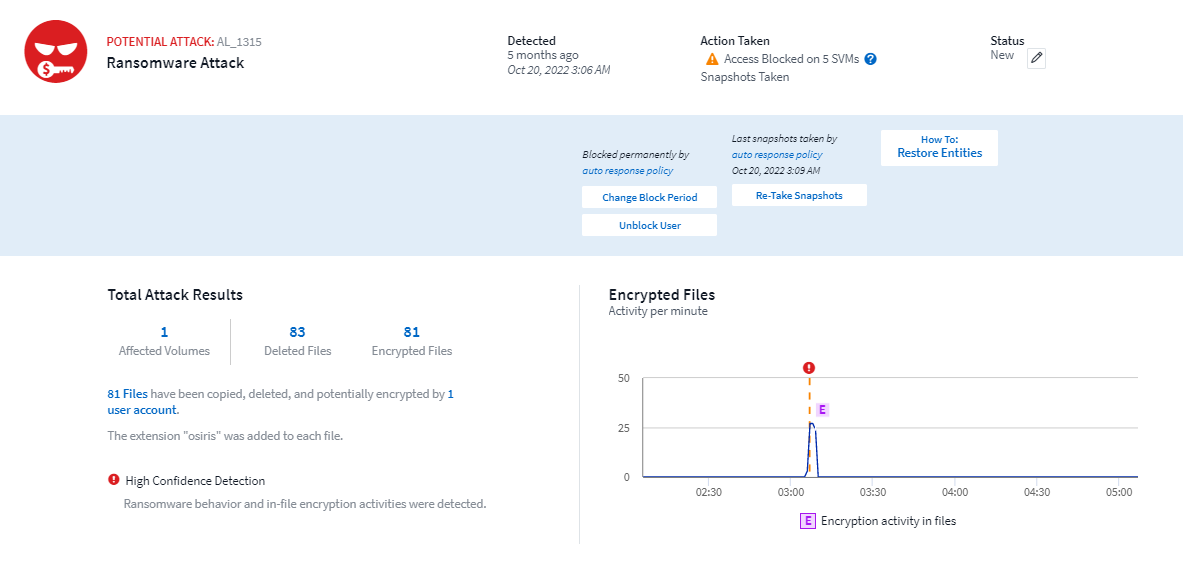
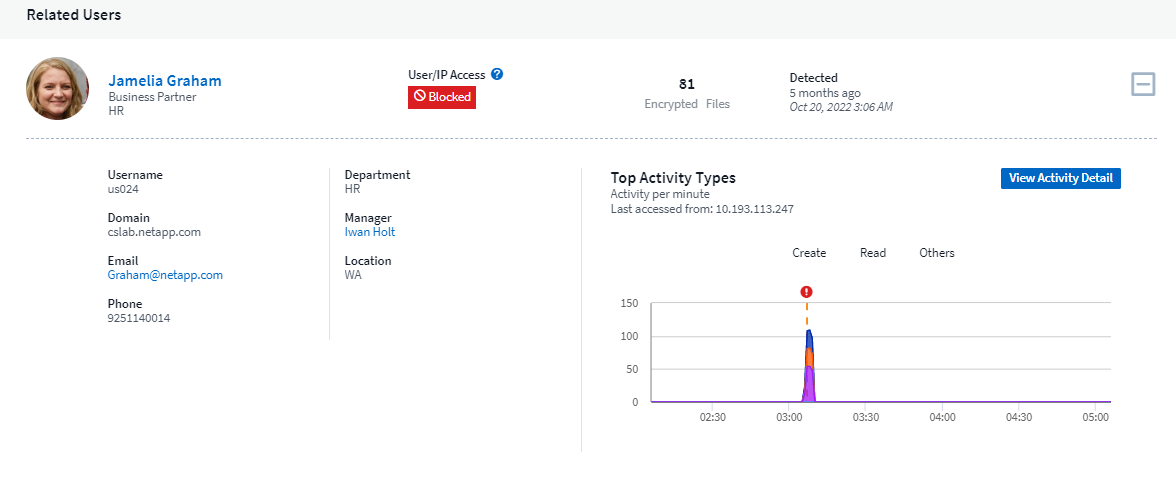
A high confidence banner indicates the attack has shown file tampering behavior along with file encryption activities.
The encrypted files graph indicates the timestamp at which the volume encryption activity was detected by the ARP solution.
Limitations
In the case where an SVM is not monitored by Workload Security, but there are ARP events generated by ONTAP, the events will still be received and displayed by Workload Security. However, Forensic information related to the alert, as well as user mapping, will not be captured or shown.
Troubleshooting
Known problems and their resolutions are described in the following table.
| Problem: | Resolution: |
|---|---|
Email alerts are received 24 hrs after an attack is detected. In the UI, the alerts are shown 24 hrs before that when the emails are received by Data Infrastructure Insights Workload Security. |
When ONTAP sends the Ransomware Detected Event to Data Infrastructure Insights Workload Security (i.e. Workload Security), the email is sent. The Event contains a list of attacks and its timestamps. The Workload Security UI displays the alert timestamp of the first file attacked. ONTAP sends the Ransomware Detected Event to Data Infrastructure Insights when a certain number of files are encoded. |


