Configuring an Active Directory (AD) User Directory Collector
 Suggest changes
Suggest changes


Workload Security can be configured to collect user attributes from Active Directory servers.
-
You must be a Data Infrastructure Insights Administrator or Account Owner to perform this task.
-
You must have the IP address of the server hosting the Active Directory server.
-
An Agent must be configured before you configure a User Directory connector.
-
In the Workload Security menu, click:
Collectors > User Directory Collectors > + User Directory Collector and select Active DirectoryThe system displays the Add User Directory screen.
Configure the User Directory Collector by entering the required data in the following tables:
Name |
Description |
Name |
Unique name for the user directory. For example GlobalADCollector |
Agent |
Select a configured agent from the list |
Server IP/Domain Name |
IP address or Fully-Qualified Domain Name (FQDN) of server hosting the active directory |
Forest Name |
Forest level of the directory structure. |
Bind DN |
User permitted to search the directory. For example: username@companyname.com or username@domainname.com |
BIND password |
Directory server password (i.e. password for username used in Bind DN) |
Protocol |
ldap, ldaps, ldap-start-tls |
Ports |
Select port |
Enter the following Directory Server required attributes if the default attribute names have been modified in Active Directory. Most often these attributes names are not modified in Active Directory, in which case you can simply proceed with the default attribute name.
Attributes |
Attribute name in Directory Server |
Display Name |
name |
SID |
objectsid |
User Name |
sAMAccountName |
Click Include Optional Attributes to add any of the following attributes:
Attributes |
Attribute Name in Directory Server |
Email Address |
|
Telephone Number |
telephonenumber |
Role |
title |
Country |
co |
State |
state |
Department |
department |
Photo |
thumbnailphoto |
ManagerDN |
manager |
Groups |
memberOf |
Testing Your User Directory Collector Configuration
You can validate LDAP User Permissions and Attribute Definitions using the following procedures:
-
Use the following command to validate Workload Security LDAP user permission:
ldapsearch -o ldif-wrap=no -LLL -x -b "dc=netapp,dc=com" -h 10.235.40.29 -p 389 -D Administrator@netapp.com -W -
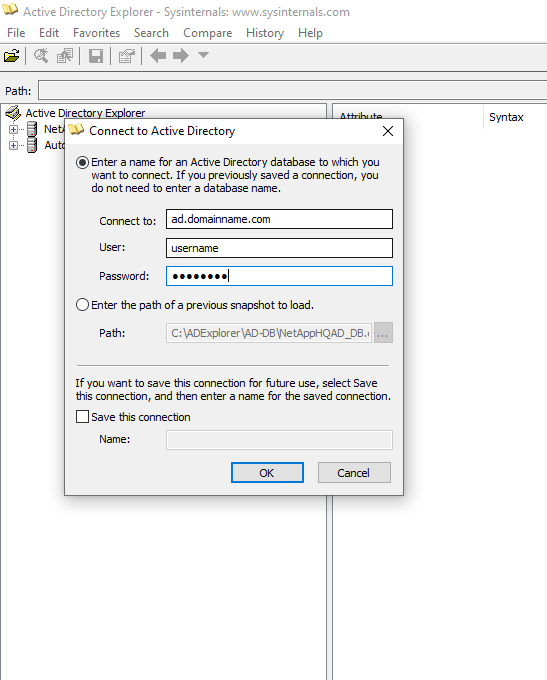
Use AD Explorer to navigate an AD database, view object properties and attributes, view permissions, view an object's schema, execute sophisticated searches that you can save and re-execute.
-
Install AD Explorer on any windows machine which can connect to the AD Server.
-
Connect to the AD server using the username/password of the AD directory server.
-
Troubleshooting User Directory Collector Configuration Errors
The following table describes known problems and resolutions that can occur during collector configuration:
| Problem: | Resolution: |
|---|---|
Adding a User Directory connector results in the ‘Error’ state. Error says, “Invalid credentials provided for LDAP server”. |
Incorrect username or password provided. Edit and provide the correct user name and password. |
Adding a User Directory connector results in the ‘Error’ state. Error says, “Failed to get the object corresponding to DN=DC=hq,DC=domainname,DC=com provided as forest name.” |
Incorrect forest name provided. Edit and provide the correct forest name. |
The optional attributes of domain user are not appearing in the Workload Security User Profile page. |
This is likely due to a mismatch between the names of optional attributes added in CloudSecure and the actual attribute names in Active Directory. Edit and provide the correct optional attribute name(s). |
Data collector in error state with "Failed to retrieve LDAP users. Reason for failure: Cannot connect on the server, the connection is null" |
Restart the collector by clicking on the Restart button. |
Adding a User Directory connector results in the ‘Error’ state. |
Ensure you have provided valid values for the required fields (Server, forest-name, bind-DN, bind-Password). |
Adding a User Directory connector results in the ‘RETRYING’ state. Shows error “Unable to define state of the collector,reason Tcp command [Connect(localhost:35012,None,List(),Some(,seconds),true)] failed because of java.net.ConnectionException:Connection refused.” |
Incorrect IP or FQDN provided for the AD Server. Edit and provide the correct IP address or FQDN. |
Adding a User Directory connector results in the ‘Error’ state. Error says, “Failed to establish LDAP connection”. |
Incorrect IP or FQDN provided for the AD Server. Edit and provide the correct IP address or FQDN. |
Adding a User Directory connector results in the ‘Error’ state. Error says, “Failed to load the settings. Reason: Datasource configuration has an error. Specific reason: /connector/conf/application.conf: 70: ldap.ldap-port has type STRING rather than NUMBER” |
Incorrect value for Port provided. Try using the default port values or the correct port number for the AD server. |
I started with the mandatory attributes, and it worked. After adding the optional ones, the optional attributes data is not getting fetched from AD. |
This is likely due to a mismatch between the optional attributes added in CloudSecure and the actual attribute names in Active Directory. Edit and provide the correct mandatory or optional attribute name. |
After restarting the collector, when will the AD sync happen? |
AD sync will happen immediately after the collector restarts. It will take approximately 15 minutes to fetch user data of approximately 300K users, and is refreshed every 12 hours automatically. |
User Data is synced from AD to CloudSecure. When will the data be deleted? |
User data is retained for 13months in case of no refresh. If the tenant is deleted then the data will be deleted. |
User Directory connector results in the ‘Error’ state. "Connector is in error state. Service name: usersLdap. Reason for failure: Failed to retrieve LDAP users. Reason for failure: 80090308: LdapErr: DSID-0C090453, comment: AcceptSecurityContext error, data 52e, v3839" |
Incorrect forest name provided. See above on how to provide the correct forest name. |
Telephone number is not getting populated in the user profile page. |
This is most likely due to an attribute mapping problem with the Active Directory. |
If encryption certificate (SSL) is enabled on the Active Directory (AD) Server, the Workload Security User Directory Collector can not connect to the AD Server. |
Disable AD Server encryption before Configuring a User Directory Collector. |
Data from Active Directory is present in CloudInsights Security. |
It is not possible to ONLY delete Active Directory user information from CloudInsights Security. In order to delete the user, the complete tenant needs to be deleted. |


