Using identity federation
 Suggest changes
Suggest changes


Using identity federation makes setting up groups and users faster, and it allows users to sign in to StorageGRID using familiar credentials.
Configuring identity federation
You can configure identity federation if you want admin groups and users to be managed in another system such as Active Directory, OpenLDAP, or Oracle Directory Server.
-
You must be signed in to the Grid Manager using a supported browser.
-
You must have specific access permissions.
-
If you plan to enable single sign-on (SSO), you must use Active Directory as the federated identity source and AD FS as the identity provider. See “Requirements for using single sign-on.”
-
You must be using Active Directory, OpenLDAP, or Oracle Directory Server as the identity provider.
If you want to use an LDAP v3 service that is not listed, you must contact technical support. -
If you plan to use Transport Layer Security (TLS) for communications with the LDAP server, the identity provider must be using TLS 1.2 or 1.3.
You must configure an identity source for the Grid Manager if you want to import the following types of federated groups:
-
Administration groups. The users in admin groups can sign in to the Grid Manager and perform tasks, based on the management permissions assigned to the group.
-
Tenant user groups for tenants that do not use their own identity source. Users in tenant groups can sign in to the Tenant Manager and perform tasks, based on the permissions assigned to the group in the Tenant Manager.
-
Select Configuration > Access Control > Identity Federation.
-
Select Enable identity federation.
The fields for configuring the LDAP server appear.
-
In the LDAP service type section, select the type of LDAP service you want to configure.
You can select Active Directory, OpenLDAP, or Other.
If you select OpenLDAP, you must configure the OpenLDAP server. See the guidelines for configuring an OpenLDAP server. Select Other to configure values for an LDAP server that uses Oracle Directory Server. -
If you selected Other, complete the fields in the LDAP Attributes section.
-
User Unique Name: The name of the attribute that contains the unique identifier of an LDAP user. This attribute is equivalent to
sAMAccountNamefor Active Directory anduidfor OpenLDAP. If you are configuring Oracle Directory Server, enteruid. -
User UUID: The name of the attribute that contains the permanent unique identifier of an LDAP user. This attribute is equivalent to
objectGUIDfor Active Directory andentryUUIDfor OpenLDAP. If you are configuring Oracle Directory Server, enternsuniqueid. Each user's value for the specified attribute must be a 32-digit hexadecimal number in either 16-byte or string format, where hyphens are ignored. -
Group unique name: The name of the attribute that contains the unique identifier of an LDAP group. This attribute is equivalent to
sAMAccountNamefor Active Directory andcnfor OpenLDAP. If you are configuring Oracle Directory Server, entercn. -
Group UUID: The name of the attribute that contains the permanent unique identifier of an LDAP group. This attribute is equivalent to
objectGUIDfor Active Directory andentryUUIDfor OpenLDAP. If you are configuring Oracle Directory Server, enternsuniqueid. Each group's value for the specified attribute must be a 32-digit hexadecimal number in either 16-byte or string format, where hyphens are ignored.
-
-
In the Configure LDAP server section, enter the required LDAP server and network connection information.
-
Hostname: The server hostname or IP address of the LDAP server.
-
Port: The port used to connect to the LDAP server.
The default port for STARTTLS is 389, and the default port for LDAPS is 636. However, you can use any port as long as your firewall is configured correctly. -
Username: The full path of the distinguished name (DN) for the user that will connect to the LDAP server.
For Active Directory, you can also specify the Down-Level Logon Name or the User Principal Name. The specified user must have permission to list groups and users and to access the following attributes:
-
sAMAccountNameoruid -
objectGUID,entryUUID, ornsuniqueid -
cn -
memberOforisMemberOf
-
-
Password: The password associated with the username.
-
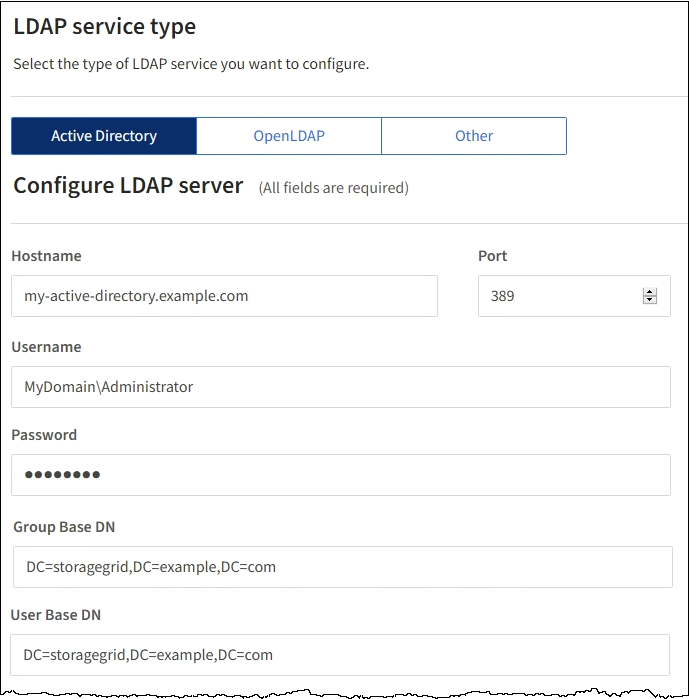
Group base DN: The full path of the distinguished name (DN) for an LDAP subtree you want to search for groups. In the Active Directory example (below), all groups whose Distinguished Name is relative to the base DN (DC=storagegrid,DC=example,DC=com) can be used as federated groups.
The Group unique name values must be unique within the Group base DN they belong to. -
User base DN: The full path of the distinguished name (DN) of an LDAP subtree you want to search for users.
The User unique name values must be unique within the User base DN they belong to.
-
-
In the Transport Layer Security (TLS) section, select a security setting.
-
Use STARTTLS (recommended): Use STARTTLS to secure communications with the LDAP server. This is the recommended option.
-
Use LDAPS: The LDAPS (LDAP over SSL) option uses TLS to establish a connection to the LDAP server. This option is supported for compatibility reasons.
-
Do not use TLS: The network traffic between the StorageGRID system and the LDAP server will not be secured.
Using the Do not use TLS option is not supported if your Active Directory server enforces LDAP signing. You must use STARTTLS or LDAPS.
-
-
If you selected STARTTLS or LDAPS, choose the certificate used to secure the connection.
-
Use operating system CA certificate: Use the default CA certificate installed on the operating system to secure connections.
-
Use custom CA certificate: Use a custom security certificate.
If you select this setting, copy and paste the custom security certificate into the CA certificate text box.
-
-
Optionally, select Test connection to validate your connection settings for the LDAP server.
A confirmation message appears in the upper right corner of the page if the connection is valid.
-
If the connection is valid, select Save.
The following screenshot shows example configuration values for an LDAP server that uses Active Directory.
Guidelines for configuring an OpenLDAP server
If you want to use an OpenLDAP server for identity federation, you must configure specific settings on the OpenLDAP server.
Memberof and refint overlays
The memberof and refint overlays should be enabled. For more information, see the instructions for reverse group membership maintenance in the Administrator's Guide for OpenLDAP.
Indexing
You must configure the following OpenLDAP attributes with the specified index keywords:
-
olcDbIndex: objectClass eq -
olcDbIndex: uid eq,pres,sub -
olcDbIndex: cn eq,pres,sub -
olcDbIndex: entryUUID eq
In addition, ensure the fields mentioned in the help for Username are indexed for optimal performance.
See the information about reverse group membership maintenance in the Administrator's Guide for OpenLDAP.
Forcing synchronization with the identity source
The StorageGRID system periodically synchronizes federated groups and users from the identity source. You can force synchronization to start if you want to enable or restrict user permissions as quickly as possible.
-
You must be signed in to the Grid Manager using a supported browser.
-
You must have specific access permissions.
-
The identity source must be enabled.
-
Select Configuration > Access Control > Identity Federation.
The Identity Federation page appears. The Synchronize button is at the bottom of the page.
-
Click Synchronize.
A confirmation message indicates that synchronization started successfully. The synchronization process might take some time depending on your environment.
The Identity federation synchronization failure alert is triggered if there is an issue synchronizing federated groups and users from the identity source.
Disabling identity federation
You can temporarily or permanently disable identity federation for groups and users. When identity federation is disabled, there is no communication between StorageGRID and the identity source. However, any settings you have configured are retained, allowing you to easily reenable identity federation in the future.
-
You must be signed in to the Grid Manager using a supported browser.
-
You must have specific access permissions.
Before you disable identity federation, you should be aware of the following:
-
Federated users will be unable to sign in.
-
Federated users who are currently signed in will retain access to the StorageGRID system until their session expires, but they will be unable to sign in after their session expires.
-
Synchronization between the StorageGRID system and the identity source will not occur, and alerts or alarms will not be raised for accounts that have not been synchronized.
-
The Enable Identity Federation check box is disabled if single sign-on (SSO) is set to Enabled or Sandbox Mode. The SSO Status on the Single Sign-on page must be Disabled before you can disable identity federation.
-
Select Configuration > Access Control > Identity Federation.
-
Uncheck the Enable Identity Federation check box.
-
Click Save.



