Manage security certificates: Overview
 Suggest changes
Suggest changes


Security certificates are small data files used to create secure, trusted connections between StorageGRID components and between StorageGRID components and external systems.
StorageGRID uses two types of security certificates:
-
Server certificates are required when you use HTTPS connections. Server certificates are used to establish secure connections between clients and servers, authenticating the identity of a server to its clients and providing a secure communication path for data. The server and the client each have a copy of the certificate.
-
Client certificates authenticate a client or user identity to the server, providing more secure authentication than passwords alone. Client certificates don't encrypt data.
When a client connects to the server using HTTPS, the server responds with the server certificate, which contains a public key. The client verifies this certificate by comparing the server signature to the signature on its copy of the certificate. If the signatures match, the client starts a session with the server using the same public key.
StorageGRID functions as the server for some connections (such as the load balancer endpoint) or as the client for other connections (such as the CloudMirror replication service).
Default Grid CA certificate
StorageGRID includes a built-in certificate authority (CA) that generates an internal Grid CA certificate during system installation. The Grid CA certificate is used, by default, to secure internal StorageGRID traffic. An external certificate authority (CA) can issue custom certificates that are fully compliant with your organization's information security policies. Although you can use the Grid CA certificate for a non-production environment, the best practice for a production environment is to use custom certificates signed by an external certificate authority. Unsecured connections with no certificate are also supported but aren't recommended.
-
Custom CA certificates don't remove the internal certificates; however, the custom certificates should be the ones specified for verifying server connections.
-
All custom certificates must meet the system hardening guidelines for server certificates.
-
StorageGRID supports bundling of certificates from a CA into a single file (known as a CA certificate bundle).

|
StorageGRID also includes operating system CA certificates that are the same on all grids. In production environments, make sure that you specify a custom certificate signed by an external certificate authority in place of the operating system CA certificate. |
Variants of the server and client certificate types are implemented in several ways. You should have all the certificates needed for your specific StorageGRID configuration ready before you configure the system.
Access security certificates
You can access information about all StorageGRID certificates in a single location, along with links to the configuration workflow for each certificate.
-
From Grid Manager, select CONFIGURATION > Security > Certificates.
-
Select a tab on the Certificates page for information about each certificate category and to access the certificate settings. You can only access a tab if you have the appropriate permission.
-
Global: Secures StorageGRID access from web browsers and external API clients.
-
Grid CA: Secures internal StorageGRID traffic.
-
Client: Secures connections between external clients and the StorageGRID Prometheus database.
-
Load balancer endpoints: Secures connections between S3 and Swift clients and the StorageGRID Load Balancer.
-
Tenants: Secures connections to identity federation servers or from platform service endpoints to S3 storage resources.
-
Other: Secures StorageGRID connections requiring specific certificates.
Each tab is described below with links to additional certificate details.
-
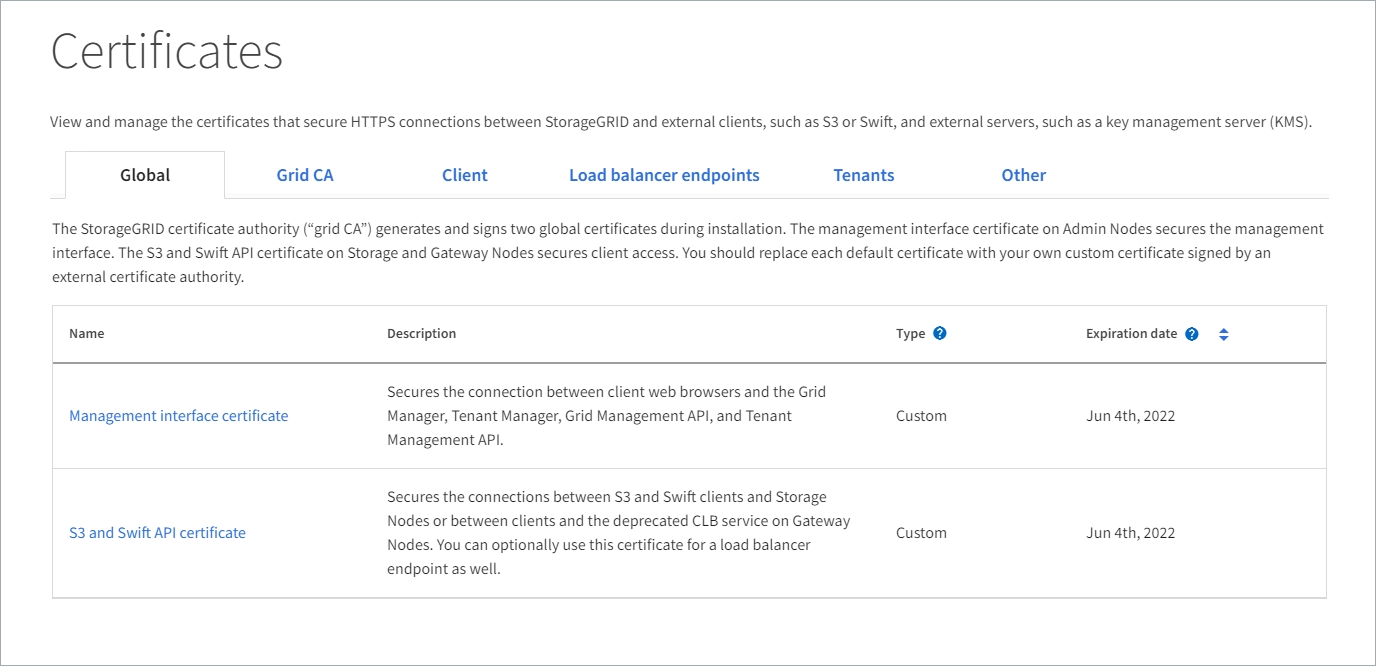
The global certificates secure StorageGRID access from web browsers and external S3 and Swift API clients. Two global certificates are initially generated by the StorageGRID certificate authority during installation. The best practice for a production environment is to use custom certificates signed by an external certificate authority.
-
Management interface certificate: Secures client web-browser connections to StorageGRID management interfaces.
-
S3 and Swift API certificate: Secures client API connections to Storage Nodes, Admin Nodes, and Gateway Nodes, which S3 and Swift client applications use to upload and download object data.
Information about the global certificates that are installed includes:
-
Name: Certificate name with link to managing the certificate.
-
Description
-
Type: Custom or default.
You should always use a custom certificate for improved grid security. -
Expiration date: If using the default certificate, no expiration date is shown.
You can:
-
Replace the default certificates with custom certificates signed by an external certificate authority for improved grid security:
-
Replace the default StorageGRID-generated management interface certificate used for Grid Manager and Tenant Manager connections.
-
Replace the S3 and Swift API certificate used for Storage Node and load balancer endpoint (optional) connections.
-
-
Use a script to generate a new self-signed management interface certificate.
-
Copy or download the management interface certificate or S3 and Swift API certificate.
The Grid CA certificate, generated by the StorageGRID certificate authority during StorageGRID installation, secures all internal StorageGRID traffic.
Certificate information includes the certificate expiration date and the certificate contents.
You can copy or download the Grid CA certificate, but you can't change it.
Client certificates, generated by an external certificate authority, secure the connections between external monitoring tools and the StorageGRID Prometheus database.
The certificate table has a row for each configured client certificate and indicates whether the certificate can be used for Prometheus database access, along with the certificate expiration date.
You can:
Load balancer endpoint certificates secure the connections between S3 and Swift clients and the StorageGRID Load Balancer service on Gateway Nodes and Admin Nodes.
The load balancer endpoint table has a row for each configured load balancer endpoint and indicates whether the global S3 and Swift API certificate or a custom load balancer endpoint certificate is being used for the endpoint. The expiration date for each certificate is also displayed.

|
Changes to an endpoint certificate can take up to 15 minutes to be applied to all nodes. |
You can:
-
View a load balancer endpoint, including its certificate details.
-
Specify a load balancer endpoint certificate for FabricPool.
-
Use the global S3 and Swift API certificate instead of generating a new load balancer endpoint certificate.
Tenants can use identity federation server certificates or platform service endpoint certificates to secure their connections with StorageGRID.
The tenant table has a row for each tenant and indicates if each tenant has permission to use its own identity source or platform services.
You can:
StorageGRID uses other security certificates for specific purposes. These certificates are listed by their functional name. Other security certificates include:
Information indicates the type of certificate a function uses and its server and client certificate expiration dates, as applicable. Selecting a function name opens a browser tab where you can view and edit the certificate details.

|
You can only view and access information for other certificates if you have the appropriate permission. |
You can:
Security certificate details
Each type of security certificate is described below, with links to the implementation instructions.
Management interface certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection between client web browsers and the StorageGRID management interface, allowing users to access the Grid Manager and Tenant Manager without security warnings. This certificate also authenticates Grid Management API and Tenant Management API connections. You can use the default certificate created during installation or upload a custom certificate. |
CONFIGURATION > Security > Certificates, select the Global tab, and then select Management interface certificate |
S3 and Swift API certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates secure S3 or Swift client connections to a Storage Node and to load balancer endpoints (optional). |
CONFIGURATION > Security > Certificates, select the Global tab, and then select S3 and Swift API certificate |
Grid CA certificate
Administrator client certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Client |
Installed on each client, allowing StorageGRID to authenticate external client access.
|
CONFIGURATION > Security > Certificates and then select the Client tab |
Load balancer endpoint certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection between S3 or Swift clients and the StorageGRID Load Balancer service on Gateway Nodes and Admin Nodes. You can upload or generate a load balancer certificate when you configure a load balancer endpoint. Client applications use the load balancer certificate when connecting to StorageGRID to save and retrieve object data. You can also use a custom version of the global S3 and Swift API certificate certificate to authenticate connections to the Load Balancer service. If the global certificate is used to authenticate load balancer connections, you don't need to upload or generate a separate certificate for each load balancer endpoint. Note: The certificate used for load balancer authentication is the most used certificate during normal StorageGRID operation. |
CONFIGURATION > Network > Load balancer endpoints |
Cloud Storage Pool endpoint certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection from a StorageGRID Cloud Storage Pool to an external storage location, such as S3 Glacier or Microsoft Azure Blob storage. A different certificate is required for each cloud provider type. |
ILM > Storage pools |
Email alert notification certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server and client |
Authenticates the connection between an SMTP email server and StorageGRID that is used for alert notifications.
|
ALERTS > Email setup |
External syslog server certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the TLS or RELP/TLS connection between an external syslog server that logs events in StorageGRID. Note: An external syslog server certificate is not required for TCP, RELP/TCP, and UDP connections to an external syslog server. |
CONFIGURATION > Monitoring > Audit and syslog server and then select Configure external syslog server |
Grid federation connection certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server and client |
Authenticate and encrypt information sent between the current StorageGRID system and another grid in a grid federation connection. |
CONFIGURATION > System > Grid federation |
Identity federation certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection between StorageGRID and an external identity provider, such as Active Directory, OpenLDAP, or Oracle Directory Server. Used for identity federation, which allows admin groups and users to be managed by an external system. |
CONFIGURATION > Access Control > Identity federation |
Key management server (KMS) certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server and client |
Authenticates the connection between StorageGRID and an external key management server (KMS), which provides encryption keys to StorageGRID appliance nodes. |
CONFIGURATION > Security > Key management server |
Platform services endpoint certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection from the StorageGRID platform service to an S3 storage resource. |
Tenant Manager > STORAGE (S3) > Platform services endpoints |
Single sign-on (SSO) certificate
| Certificate type | Description | Navigation location | Details |
|---|---|---|---|
Server |
Authenticates the connection between identity federation services, such as Active Directory Federation Services (AD FS), and StorageGRID that are used for single sign-on (SSO) requests. |
CONFIGURATION > Access control > Single sign-on |
Certificate examples
Example 1: Load Balancer service
In this example, StorageGRID acts as the server.
-
You configure a load balancer endpoint and upload or generate a server certificate in StorageGRID.
-
You configure an S3 or Swift client connection to the load balancer endpoint and upload the same certificate to the client.
-
When the client wants to save or retrieve data, it connects to the load balancer endpoint using HTTPS.
-
StorageGRID responds with the server certificate, which contains a public key, and with a signature based on the private key.
-
The client verifies this certificate by comparing the server signature to the signature on its copy of the certificate. If the signatures match, the client starts a session using the same public key.
-
The client sends object data to StorageGRID.
Example 2: External key management server (KMS)
In this example, StorageGRID acts as the client.
-
Using external Key Management Server software, you configure StorageGRID as a KMS client and obtain a CA-signed server certificate, a public client certificate, and the private key for the client certificate.
-
Using the Grid Manager, you configure a KMS server and upload the server and client certificates and the client private key.
-
When a StorageGRID node needs an encryption key, it makes a request to the KMS server that includes data from the certificate and a signature based on the private key.
-
The KMS server validates the certificate signature and decides that it can trust StorageGRID.
-
The KMS server responds using the validated connection.


